Reference no: EM131276193
Assignment
I. De-authentication frames
1) Read about the elements of a de-authentication frame and provide a graphic depicting the contents of a de-authentication frame. Make sure to provide the bit details for the frame control bits.
2) An attack may require de-authentication in order to capture the handshake during reauthentication. Explain which parts of the frame you would get from sniffing and which parts you would be able to construct based on an understanding the specification.
3) In two or three sentences, discuss the payload of the de-authentication frame.
II. WEP
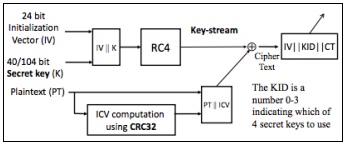
Assume you have started a sniffer and captured some unencrypted WEP management frames: the plaintext challenge from the Access Point, and the response from the Station to the Access Point
1. Write a paragraph explaining how you could recover the key stream (not the key)
2. Write a paragraph explaining how you can use the recovered key stream to generate an availability attack (One of the WEP weaknesses is important). There are many possible DoS attacks, e.g. syn floods, but you must figure out how to use the captured keystream.
3. It isn't an availability attack if you just do it once! Write a paragraph describing what you need to do to continue to maintain the attack on the Access Point? You should mention the MAC and the IV.
4. Write a short paragraph explaining why your attack is better than requesting access from the AP and just sending a random string of bits or reusing a legitimate syn frame?