Reference no: EM131221457
Three computers, A, B, and C, have the numerical features listed below:
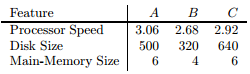
We may imagine these values as defining a vector for each computer; for instance, A's vector is [3.06, 500, 6]. We can compute the cosine distance between any two of the vectors, but if we do not scale the components, then the disk size will dominate and make differences in the other components essentially invisible. Let us use 1 as the scale factor for processor speed, α for the disk size, and β for the main memory size.
(a) In terms of α and β, compute the cosines of the angles between the vectors for each pair of the three computers.
(b) What are the angles between the vectors if α = β = 1?
(c) What are the angles between the vectors if α = 0.01 and β = 0.5?
(d) One fair way of selecting scale factors is to make each inversely proportional to the average value in its component. What would be the values of α and β, and what would be the angles between the vectors?
|
Compute the cosine distance between each pair of users
: Then, construct from the original matrix of Fig. 9.8 a new matrix whose rows correspond to users, as before, and whose columns correspond to clusters. Compute the entry for a user and cluster of items by averaging the nonblank entries for that use..
|
|
Which points need further clarification and why
: In this section, you will analyze your findings from the articles and answer these questions: With which points did you agree and/or disagree and why? Which points resonated with you and why? Which points need further clarification and why? How do..
|
|
Analyze the database security highlights
: Thoroughly analyze the database security highlights offered by COTS (business off the rack) DBMS's. For every component you ought to quickly layout the database security issue the element is tending to.
|
|
Computers and the future
: What do you think the future of computer technology will be 5 to 10 years from now. For example in the 1960's Star Trek have the flip communicator and then in the 1990's we have the motorola flip cell phone.
|
|
What would be the angles between the vectors
: One fair way of selecting scale factors is to make each inversely proportional to the average value in its component. What would be the values of α and β, and what would be the angles between the vectors?
|
|
Evaluate the effectiveness of organizations implementation
: For each management system element, discuss the objective evidence you found. Evaluate the effectiveness of the organization's implementation of each element against available reference sources and best practice information.
|
|
File joint income tax return
: Troy and Tracy are married and file a joint income tax return. Their adjusted gross income is $30,000 per year. On last years return, the Tanks claimed a $960 credit for child care expenses. The Tanks are in the 15% marginal income tax bracket. What ..
|
|
Discuss how papa principles of ethics can be applied
: Compare and contrast traditional outsourcing with the Software as a Service (SaaS). Under what conditions should a company choose SaaS over traditional outsourcing? Discuss how PAPA principles of ethics (Motiwalla & Thompson 2012, p.278) can be app..
|
|
How to implement virtual functions in c
: How to Implement virtual functions in C? What is the advantage of new Lock interface over synchronized block in Java? You need to implement a high performance cache which allows multiple reader but single writer to keep the integrity how will you ..
|