Reference no: EM132615507
Question 1
Four kinds of problems are found with 1NF designs that do not exist in 2NF. What are they? Use figure 1 below to discuss these four problems.
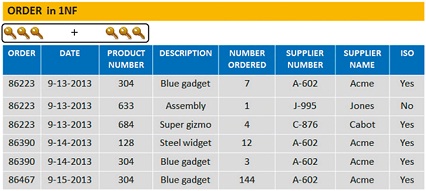
Figure 1
Study Parrot Palace case study below and answer questions that follow:
Parrot Palace
Parrot Palace works with TV and movie producers who need birds that can perform special tricks, such as playing dead, reciting poetry, ladder climbs, and various other tricks. Parrot Palace has about 50 birds and a list of 20 tricks from which to choose. Each bird can perform one or more tricks, and many tricks can be performed by more than one bird. When a bird learns a new trick, the trainer assigns a skill level. Some customers insist on using birds that score a 10, which is the highest skill level. As an IT consultant, you have been asked to suggest 3NF table designs. You are fairly certain that an M: N relationship exists between birds and tricks.
Draw an ERD for the Parrot Palace information system. Indicate cardinality. (13)
Create 3NF table designs.
Question 2
Read each of the following CASE STUDIES and answer the questions that follow each case study:
CASESTUDY-1: Jonathan is part of a team that is responsible for implementing a new information system, the design of which was developed using traditional structured methods. To manage the complexity of the application development process, Jonathan wants to employ structured development techniques, and he turns to you for information about these techniques. You begin by telling him about structure charts, which show program modules and the relationships among them using various graphical symbols.
1. You inform Jonathan that one type of element in a structure chart is a data couple, which shows data that one module passes to another. What symbol is used for a data couple?
a. an arrow with a filled circle
b. an arrow with an empty circle
c. a line with a diamond on one end
d. a curved arrow
2. Jonathan asks you how to represent the fact that one program module (a control module) determines which other subordinate modules will be invoked. You tell him that he can use a condition. What symbol is used for a condition?
a. an arrow with a filled circle
b. an arrow with an empty circle
c. a line with a diamond on one end
d. a curved arrow
CASESTUDY-2: Libby and her team have finished the coding of a new application, and they are ready to begin testing. She asks Emma for help in designing the types of tests that she and her team should perform.
3. Libby mentions that she must test a program that interacts with other programs, and she wants to begin by testing the program individually. Emma tells her about a process in which a programmer simulates each program outcome or result and displays a message to indicate whether or not the program executed successfully. What is the name of this process?
a. integration testing
b. system testing
c. link testing
d. stub testing
4. Emma also recommends that Libby test groups of programs that depend on each other to ensure that they work together properly. What is one name for this type of testing?
a. integration testing
b. unified testing
c. unit testing
d. stub testing
CASESTUDY-3: Jamal's firm contracts to provide risk management services for a wide range of smaller companies that cannot provide the service for themselves. One of Jamal's responsibilities at the end of each month is to review the threats encountered by the companies and put them into the appropriate categories.
5. One of his firm's clients details an incident in which a hacker - a former employee - stole trade secrets from the client and threatened to release them to the competition if he was not paid. In which of the following categories does Jamal place this incident?
a. vandalism
b. trespass and espionage
c. extortion
d. software attack
6. Another of Jamal's clients has software that is so outdated that it has become increasingly vulnerable to attack. How does Jamal categorize this threat?
a. human error
b. technical obsolescence
c. service failure
d. espionage
CASESTUDY-4: As another one of his responsibilities, Jamal captures information from clients about attacks they have borne and from their description, he identifies the kind of attack they have experienced.
7. One of Jamal's clients reports that the traffic on their network is being intercepted and scanned for valuable information. How does Jamal categorize this incident?
a. spoofing
b. man in the middle
c. dumpster diving
d. sniffing
8. Another of Jamal's clients describes a situation in which a caller to their help desk pretended to be a legitimate user and requested that his password to his company account be changed. How does Jamal categorize this incident?
a. social engineering
b. man in the middle
c. spoofing
d. privilege escalation
Question 3
3.1 Explain configuration management in depth.