Reference no: EM131280923
Part 1: Questions:
Question 1
Draw a (single) binary tree T, such that
- Each internal node of T stores a single character;
- A preorder traversal of T yields: HOECLFNKJIANGDB;
- An inorder traversal of T yields: EONFKLJCAINHDGB;
- A postorder traversal of T yields: ENKFJLANICODBGH.
Question 2
Assume that the binary tree from Question 1 above is stored in an array-list as a complete binary tree as discussed in class. Specify the contents of such an array-list for this tree.
Question 3
Draw the min-heap that results from running the bottom-up heap construction algorithm on the following list of values:
35 24 41 13 39 99 104 28 30 64 39 20 21 17 49.
Starting from the bottom layer, use the values from left to right as specified above. Show intermediate steps and the final tree representing the min-heap. Afterwards perform the operation removeMin() 3 times and show the resulting min-heap after each step.
Question 4
Create again a min-heap using the list of values from Question 3 above but this time you have to insert these values step by step using the order from left to right as shown in Question 3. Show the tree after each step and the final tree representing the min-heap.
Question 5
Give an algorithm for computing the depths of all the nodes of a tree T, where n is the number of nodes of T.
i) What is the complexity of your algorithm in terms of Big-O?
ii) What is the best possible complexity that you believe can be achieved when solving such problem? Explain why.
iii) If your algorithm does not achieve this best complexity, can you design a better algorithm to achieve such complexity! If so, give this algorithm as a second solution.
Question 6
Assume the utilization of linear probing for hash-tables. To enhance the complexity of the operations performed on the table, a special AVAILABLE object is used. Assuming that all keys are positive integers, the following two techniques were suggested in order to enhance complexity:
i) In case an entry is removed, instead of marking its location as AVAILABLE, indicate the key as the negative value of the removed key (i.e. if the removed key was 16, indicate the key as -16). Searching for an entry with the removed key would then terminate once a negative value of the key is found (instead of continuing to search if AVAILABLE is used).
ii) Instead of using AVAILABLE, find a key in the table that should have been placed in the location of the removed entry, then place that key (the entire entry of course) in that location (instead of setting the location as AVAILABLE). The motive is to find the key faster since it now in its hashed location. This would also avoid the dependence on the AVAILABLE object.
Will either of these proposal have an advantage of the achieved complexity? You should analyze both time-complexity and space-complexity. Additionally, will any of these approaches result in misbehaviors (in terms of functionalities)? If so, explain clearly through illustrative examples.
Question 7
Assume a hash table utilizes an array of 13 elements and that collisions are handled by separate chaining. Considering the hash function is defined as: h(k)=k mod 13.
i) Draw the contents of the table after inserting elements with the following keys: 32, 147, 265, 195, 207, 180, 21, 16, 189, 202, 91, 94, 162, 75, 37, 77, 81, 48.
ii) What is the maximum number of collisions caused by the above insertions?
Question 8
To reduce the maximum number of collisions in the hash table described in Question 6 above, someone proposed the use of a larger array of 15 elements (that is roughly 15% bigger) and of course modifying the hash function to: h(k)=k mod 15. The idea was to reduce the load factor and hence the number of collisions.
Does this proposal hold any validity to it? If yes, indicate why such modifications would actually reduce the number of collisions. If no, indicate clearly the reasons you believe/think that such proposal is senseless.
Question 9
Assume an open addressing hash table implementation, where the size of the array N = 19, and that double hashing is performed for collision handling. The second hash function is defined as:
d(k) = q - k mod q,
where k is the key being inserted in the table and the prime number q is = 11. Use simple modular operation (k mod N) for the first hash function.
i) Show the content of the table after performing the following operations, in order: put(38), put(15), put(43), put(22), put(71), put(8), put(28), put(37), put(19).
ii) What is the size of the longest cluster caused by the above insertions?
iii) What is the number of occurred collisions as a result of the above operations?
iv) What is the current value of the table′s load factor?
Question 10
Assume the utilization of linear probing instead of double hashing for the above implementation given in Question 8. Still, the size of the array N = 19, and that simple modular operation (k mod N) is used for the hash function. Additionally, you must use a special AVAILABLE object to enhance the complexity of the operations performed on the table.
i) Show the contents of the table after performing the following operations, in order: put(29), put(53), put(14), put(95), remove(53), remove(29), put(32), put(19), remove(14), put(30), put(12), put(72).
ii) What is the size of the longest cluster caused by the above insertions? Using Big-O notation, indicate the complexity of the above operations.
iii) What is the number of occurred collisions as a result of the above operations?
Question 11
Given the following tree, which is assumed to be an AVL tree:
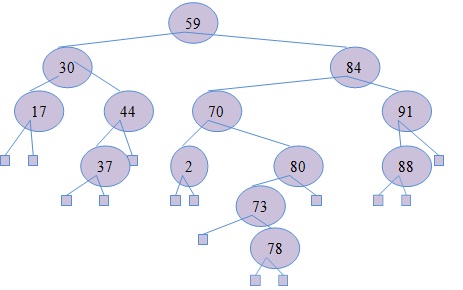
i) Are there any errors with the tree as shown? If so, indicate what the error(s) are, correct these error(s), show the corrected AVL tree, then proceed to the following questions (Questions ii to iv) and start with the tree that you have just corrected. If no errors are there in the above tree, indicate why the tree is correctly an AVL tree, then proceed to the following questions (Questions ii to iv) and continue working on the tree as shown above.
ii) Show the AVL tree after put(74) operation is performed. Give the complexity of this operation in terms of Big-O notation.
iii) Show the AVL tree after remove(70) is performed. Give the complexity of this operation in terms of Big-O notation.
iv) Show the AVL tree after remove(91) is performed. Show the progress of your work step-by-step. Give the complexity of this operation in terms of Big-O notation.
Question 12
Show the steps that a radix sort takes when sorting the following array of Integer keys:
783 99 472 182 264 543 356 295 692 491 94
Part 2: Programming Questions:
The Canadian Real Estate Association (CREA). Operates on multiple lists of n properties where each property is identified by a unique ULS code of 8 digits (e.g. # ULS: 20942894), some of the lists are local for cities and areas, where n counts few hundred properties. Others are at the provincial level, that is n counts tens of thousands or more. CREA needs your help to design a smart "real estate listing" data structure called SmartULS. Keys of SmartULS entries are integers of 8 digits, and one can retrieve the key of a SmartULS or access a single element by its key. Furthermore, similar to sequences, given a SmartULS element one can access its predecessor or successor (if it exists). SmartULS adapts to their usage and keep the balance between memory and runtime requirements. For instance, if a smart ULS contains only a small number of entries (e.g., few hundreds), it might use less memory overhead but slower (sorting) algorithms. On the other hand, if the number of contained entries is large (greater than 1000 or even in the range of tens of thousands of elements), it might have a higher memory requirement but faster (sorting) algorithms. SmartULS might be almost constant in size or might grow and/or shrink dynamically. Ideally, operations applicable to a single SmartULS entry should be O(1) but never worse than O(n). Operations applicable to a complete SmartULS should not exceed O(n2).
You have been asked to design and implement a SmartULS, a smart data structure which automatically adapts to the dynamic content that it operates on. In other words, it accepts the size (total number of properties n identified by their 8 digits ULS number as a key) as a parameter and uses an appropriate (set of) data structure(s) from the one(s) studied in class in order to perform the operations below efficiently1.
The SmartULS must implement the following methods:
- setSmartThresholdULS(Size): where 100 ≤ Threshold ≤ ~500,000 is an integer number that defines when the list size should be implemented with a data structure such as a Tree, Hash Table, AVL tree, binary tree, or sequence, if its size is greater than or equal to value of Threshold.
- generate(): randomly generates new non-existing key of 8 digits
- allKeys(SmartULS): return all keys in SmartULS as a sorted sequence
- add(SmartULS,key,value2): add an entry for the given key and value
- remove(SmartULS,key): remove the entry for the given key
- getValues(SmartULS,key): return the values of the given key
- nextKey(SmartULS,key): return the key for the successor of key
- prevKey(SmartULS,key): return the key for the predecessor of key
- rangeKey(key1, key2): returns the number of keys that are within the specified range of the two keys key1 and key2.
1. Write the pseudo code for each of the methods above.
2. Write the java code that implements the methods above.
3. Discuss how both the time and space complexity change for each of the methods above if the underlying structure of your SmartULS is an array or a linked list?
You have to submit the following deliverables:
a) A detailed report about your design decisions and specification of your SmartULS ADT including a rationale and comments about assumptions and semantics.
b) Well-formatted and documented Java source code and the corresponding class files with the implemented algorithms.
c) Demonstrate the functionality of your SmartULS by documenting at least 5 different but representative data sets. These examples should demonstrate all cases of your SmartULS ADT functionality (e.g., all operations of your ADT for different sizes). You have to additionally test your implementation with benchmark files that will be posted soon here:
https://users.encs.concordia.ca/~haarslev/teaching/comp352/
Both the written part and the programming part must be done individually or by team of max 2 students. Submit all your answers to written questions in PDF (no scans of handwriting) or text formats only. Please be concise and brief (less than ¼ of a page for each question) in your answers. For the Java programs, you must submit the source files together with the compiled executables. The solutions to all the questions should be zipped together into one .zip or .tar.gz file and submitted via EAS. You may upload at most one file to EAS.
For the programming component, you must make sure that you upload the assignment to the correct directory of Assignment 3 using EAS. Assignments uploaded to the wrong directory will be discarded and no resubmission will be allowed.
You will need to submit both the pseudo code and the Java program, together with your experimental results. Keep in mind that Java code is not pseudo code.