Reference no: EM132358214
Configure and Manage Intrusion Prevention System on Network Sensors Assignment -
Outcomes Assessed - Performance Criteria: Addresses some elements of performance evidence and knowledge evidence as shown in the Assessment Matrix
Assessment Task 1: Research and Presentation: IPS Sensors
Description: Intrusion detection system (IDS) and intrusion prevention system (IPS) solutions form an integral part of a robust network defence solution in today's electronically charged environment. Maintaining secure network services is a key requirement of a profitable IP-based business.
In this assessment task, you will research and evaluate the ways IPS sensors are used to mitigate network attacks. To help you provide a context for this task, the following business scenario is given. However, you may choose any other organisational of your preference.
Case Scenario: For more than 70 years, Weltman, Weinberg & Reis (WWR) has been a leader in providing collection services and legal representation to creditors. Headquartered in Sydney, Australia, WWR is the largest creditor's rights law firm in the country. The company depends on its network to connect 1000 employees at nine offices, and to provide real - time status information on cases and files.
Protecting the sensitive client information that resides on its network is a top priority for WWR. Much of the firm's application data contains confidential or non-public information (NPI). Along with privacy concerns, maintaining data integrity is also important, because customer contact records and other business information is often used in legal proceedings. Records that have become corrupted or inaccurate because of a security or network issue can result in a total breakdown of the process and a significant loss to the firm.
WWR needed a flexible, manageable security solution that could provide a defence-in-depth approach, safeguarding not only the network perimeter, but also the firm's internal network all the way to the desktop level.
Your research and presentation will include;
- System requirements of the network according to industry standards for inline operations.
- Compare inline to promiscuous mode sensor operations and evaluate how IPS protects network devices from attacks.
- Evaluate the evasive techniques used by hackers and determine ways IPS can defeat those techniques in the network.
- Evaluate the considerations necessary for selection, placement, and deployment of a network IPS including using features of IPS signature.
- What is the Meta Signature Engine?
- From a cisco.com site, research how to create a meta signature.
- What is Passive Operating System fingerprinting?
Assessment Criteria - The following assessment criteria will be used for marking this assessment task. Ensure that you have addressed all of the criteria in your work;
- Researched, complied and organised information on IPS sensors
- Appropriate IPS product is selected that best match/address the enterprise needs and requirements
- Research demonstrates a comparative study of at least two competing products
- Described the key functions and features of the product
- Analysed and outlined system requirements for implementing IPS sensor solution
- Provided a rationale for using the IPS sensors
- Compared inline to promiscuous mode sensor operations and evaluate how IPS protects network devices from attacks
- Referred to at least two commonly known hacker attacks and explained how IPS can counter those attacks
- Outlined the criteria for selection, placement, and deployment of a network IPS including using features of IPS signature
- Gathered and explain information on Meta signatures and passive operating system fingerprinting as security features
- Presented the research summary to the class
- Presentation was well structured, cohesive and maintained a consistent flow of information
- Maintained an eye contact with the audience and allowed for feedback
Assessment Task 2: Install and Configure IPS Sensors
Description: Consider the following network topology;
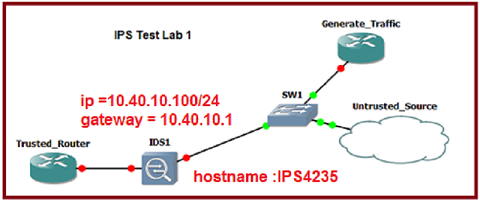
Task: Install, initialize and test a Cisco IPS 4235 appliance
Initial configuration and first task;
- Console into the sensor
- Use the username cisco and password qaz123wsx
- Create other user accounts
- Set up communication with external source
1. Enter the command to initialize the sensor: setup
2. Enter the command to change the hostname to that shown on the lab diagram above:
3. Enter the command to change the control interface IP address and gateway to that shown on the lab diagram. Notice the comma between the entries.
4. Don't allow telnet and don't allow browsing to port 80. Press return when these default values are shown:
5. Only allow hosts on 10.40.0.0/16 to manage the sensor.
6. Add an inline pair called perimeter. Gi0/1 and Gi0/3 are the interface pair.
7. Press enter to "Save this configuration and exit setup."
Assessment Criteria - The following assessment criteria will be used for marking this assessment task. Ensure that you have addressed all of the criteria in your work.
This task will be observed by the trainer/assessor;
- Identified and selected the right equipment
- Selected and connected a cisco IPS sensor hardware
- Checked connections
- Set up the network as per the given topology
- Configured the IPS sensor as instructed
- Entered commands as instructed
- Checked and tested configuration
- Displayed and verified messages and feedback
- Created user accounts
- Communicated with an untrusted source and verified system integrity
- Took preventive measures to mitigate the threats
- Debugged the commands where needed and ensured system integrity
- Followed instructions and maintained a methodical approach to the task
- Demonstrated knowledge of IPS configuration needs
Assessment Task 3: Configuration commands using CLI
Description: Consider the following network topology;
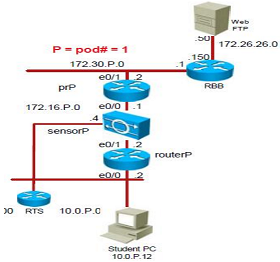
Task 1: Sensor Initialisation
1. Console into the sensor using the program Putty.
2. Use the username cisco and password qaz123wsx
- Enter the command to initialise the sensor
- Enter the command to change the hostname to that shown on the lab diagram above
- Enter the command to change the control interface IP address and gateway to that shown on the lab diagram
- Don't allow telnet and don't allow browsing to port 80
- Add an ACL entry to allow your PC to manage the sensor
- Press enter to "Save this configuration and exit setup."
Task 2: Test connectivity to the newly configured sensor
1. Test your initialization by remotely accessing your sensor using SSH.
2. Using Putty or Teraterm, initiate an SSH connection to the sensor's control address of 10.0.1.4
3. When prompted, enter the username cisco and password qaz123wsx
The following should be seen:
Sensor1#
Task 3: Navigating the sensor CLI
Log back into the sensor using the username cisco and password qaz123wsx
1. Display two of the Command options available in the first level of the CLI, the privileged
EXEC mode: sensor1#?
Check: Successfully connected to the sensor using SSH?
2. Enter the second level of the CLI, configuration mode:
sensorP# configure terminal
sensorP(config)#
3. Display two of the Command options available in configuration mode:
sensorP(config)# ?
4. Display two of the services that can be configured via the CLI:
sensorP(config)# service ?
5. Enter configuration mode for event action rules:
sensorP(config)#service event-action-rules rules0
sensorP(config-eve)#
6. Display two of the commands available from the event action rules configuration mode:
sensorP (config-eve)# ?
7. Enter host configuration mode:
sensorP(config)# service host
sensorP(config-hos)#
8. What command available from the host configuration mode will allow you to set time related settings?
sensorP(config-hos)# ?
9. Enter interface configuration mode:
sensorP(config)#service interface
sensorP(config-int)#
10. From the display of the commands that are available from the interface configuration mode:
sensorP(config-int)# ?
What is the function of the COMMAND BYPASS-MODE?
11. Display two of the configuration options and settings for a specific signature by completing the following substeps:
Enter configuration mode for signature 12505, subsignature 3 (H225: SETUP fixed signature 1):
sensorP(config-sig)# signatures 12505 3
sensorP(config-sig-sig)#
Task 4: Changing the event-action for a signature
12. What command will display the settings for signature 12505, subsignature 3?
sensorP(config-sig-sig)#show settings
13. From the settings for signature 12505, subsignature 3, write down the alert-severity and the sig-fidelity- rating:
14. Find out what this signature is matching
15. Enter configuration mode for the signature engine corresponding to signature 12505, subsignature 3:
16. Change the trigger event action to produce-alert sensorP(config-sig-sig-ser)# event-action produce-alert
Task 5: Back Up and Restore the Current Configuration
17. Enter the command to backup your current configuration
Sensor1#
18. Display the backed-up configuration file
19. View the ACLs in your current configuration again
Task 6: Display sensor events
Display all the events that have occurred in the last 30 minutes
Task 7: Add a user account
Display the user accounts that are already created:
20. Exit privileged EXEC mode:
sensorP# exit
sensorP login:
21. Log in with the administrator account, admin:
Sensor login: admin
Password: admin
22. Create a new account with privilege level viewer.
Assessment Criteria - The following assessment criteria will be used for marking this assessment task. Ensure that you have addressed all of the criteria in your work.
This task will be observed by the trainer/assessor;
- Identified and selected the right equipment
- Selected and connected a cisco IPS sensor hardware
- Checked connections
- Set up the network as per the given topology
- Configured the IPS sensor as instructed
- Entered commands as instructed
- Checked and tested configuration
- Displayed and verified messages and feedback
- Created user accounts
- Tuned Tune sensor signatures to provide optimal protection of the network
- Created custom signatures and a meta signature
- Configured gateway for passive operating system (OS) fingerprinting
- Configured advanced featured and resolved anomalies
- Demonstrated knowledge of IPS configuration needs
Assessment Task 4: Knowledge Test
Description: This is a closed book test and must be undertaken in presence of an assessor. All the questions must be answered.
Q1. What cisco proprietary protocol allows dynamic failover of next hop gateways for PCs in a LAN?
Q2. Write the configuration commands to activate HSRP group 14 with a virtual ip of 10.10.1.254. Ensure that this device will become the active router irrespective of whether it boots before or after other HSRP members.
Q3. How does an HSRP standby router know that it needs to take over the active role?
Refer to the following graphic for questions 4 to 7 (see in attached file)
Q4. Which is the address of the virtual router?
Q5. What is the address of the router that becomes active?
Q6. This multilayer switch is the standby router. What is a possible value of the HSRP priority of the active router?
Q7. The special HSRP mac address is 0000.0c07.ac64. What do the last two hex numbers - 64 in this example - tell us?
Refer to the following graphic for questions 8 to 10 (see in attached file)
Q8. For HSRP group 1, what is the device that is active?
Q9. If the active device for HSRP group 1 fails then recovers a while later, will it be able to be active router again? Explain.
Q10. The above example, shows load balancing. If a PC has a gateway address set to 172.16.10.120, will it use routerA as its gateway? Explain.
Refer to the following Graphic for all questions: (see in attached file)
Q11. What routing protocol was being used inside the International Travel Agency?
Q12. What routing protocols may be used to link the International Travel Agency with the internet?
Q13. How can you check the path taken by packets from PC_4 to PC_2?
Q14. A continuous ping from Another_Company router to local_server2 goes via CE1 then Firewall_1. What path will allow the ping to continue if the link from Telstra2 to CE1 fails?
Q15. A continuous ping from Another_Company router to local_server2 goes via CE1 then Firewall_2. What path will allow the ping to continue if the link from Firewall_2 to CE1 fails?
Q16. A continuous ping from PC_2 router to PC_4 goes via Firewall_1 then CE2. What path will allow the ping to continue if the link from Telstra1 to CE2 fails?
Q17. How could you check that load balancing occurs for traffic from PC_1 to the Internet_server?
Q18. A continuous ping from PC_3 router to PC_4 goes via Firewall_2 then CE2. Why is failure recovery not possible if the Firewall_2 fa0/0 port fails?
Assessment Criteria - The following assessment criteria will be used for marking this assessment task. Ensure that you have addressed all of the criteria in your work.
- The test was completed according to given instructions.
- All the questions are attempted and answered.
- The answers demonstrate the breadth of knowledge on the subject matters as required.
Attachment:- Intrusion Prevention System Assignment File.rar