Reference no: EM133702156
TCP/IP Principles and Protocols
Assignment
Question 1 Routing table and packet delivery
The figure below shows the configuration of a hypothetical section of the Internet. Assume that all routers have fully updated tables.
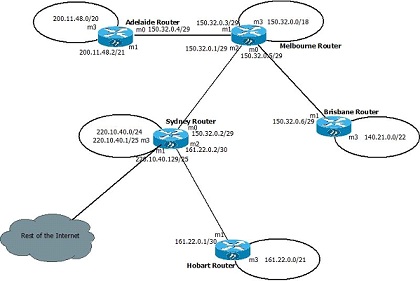
Construct the routing table of routers Adelaide and Sydney. Write the masks in dotted-decimal format and list in longest-mask order.
A packet arrives at the Hobart Router with the destination address 140.40.120.10. Explain the steps that the router takes to determine where next to forward this packet. What was the Router's forwarding decision? Show the Router's calculations for at least one of the table entries other than the default.
Question 2. Routing Protocol Configuration
For this question, open the file Assignment_Two_Q2.pkt.
All ports on all devices in the network are pre-configured with IP addresses. However, no routing protocol has been configured in the routers.
Configure RIP version 2 routing protocol in both routers and test the connectivity of the network by pinging from the East router to one of the PCs in Headquarters. Save this as a screenshot. Save the changed pkt file as ‘your-student-ID-Q2.pkt' and submit this file - it must have functional routing (e.g., if tested in a ping by the marker) to receive full marks. Use the CLI (Command Line Interface) to display the routing table (do for both routers) and save them in a screenshot. Include all screenshots in the Assignment2-answer-template_T1_2024.docx file.
Type the CLI commands you used to configure RIPv2 in both (HQ and East Branch) routers into the Assignment2-answer-template_T1_2024.docx file.
Question 3. DHCP Configuration
For this question, open the file Assignment_Two_Q3.pkt.
The PCs in this file are not configured yet i.e. they have no IP set up, static or otherwise.
Configure DHCP in both routers (HQ and East Branch) for the networks listed below.
(4 marks)
HQ router:
141.14.0.0
141.14.64.0
East Branch router:
192.168.1.0
192.168.2.0
Type the CLI commands you have used in both (HQ and East Branch) routers for DHCP implementation into Assignment2-answer-template_T1_2024.docx as your answer and submit.
After configuring DHCP, configure the PCs to obtain their IP address through DHCP. Then test the network's DHCP configuration by sending a packet from one host to another. Take a screenshot that demonstrates a successful transmission and include it in your Assignment2-answer-template_T1_2024.docx. Save your packet tracer file as your_student_ID-Q3.pkt' (replace "your_student_ID" with your student ID) and submit it.
Question 4. Research Questions on IoT Protocols
Study the two articles in Week 10 about IoT protocols focusing on basic functions and purposes. You may also engage with other literature as necessary. Then discuss the protocols by answering the following three questions.
Three main IoT protocols were discussed in the articles: The CoAP (Constrained Application Protocol), MQTT (Message Queuing Telemetry Transport) and XMPP (Extendible Message Persistent Protocol). In your own words, discuss the core purpose and function of each of these protocols. Your discussion should clearly explain why each protocol was named such. For example, why is CoAP called the "Constrained Application Protocol" - what is being constrained and how? Deep technical discussion is not required in this answer, rather you need to demonstrate a basic grasp of the concept behind each protocol.
Discuss the circumstances or scenarios in which each of the above protocols could be beneficial to use - for example when would it be better to use MQTT rather than XMPP, or what difference does it make?
Regarding the issue of whether IoT protocols should be standardised, there is more written about the advantages of standardising, than on the disadvantages of doing so. In your view, what might be some disadvantages of standardising IoT protocols? Based on that do you think IoT protocols should be standardised? Give reasons for your thoughts.
You should structure your report into a section for each of the above parts. There is no minimum/maximum length of the report. Support your assertions or conclusions by quoting reputable sources of information. You may include pictures or diagrams, but they must be relevant and must directly support your writing. Assume an audience with a similar background in networking as you. Your writing should demonstrate that you understand the main concepts and issues. Technical depth and expertise is not expected.