Reference no: EM1348463
Database Systems
1. What is an SQL injection attack? Explain how it works, and what precautions must be taken to prevent SQL injection attacks.
2. What are two advantages of encrypting data stored in the database?
3. RAID systems typically allow you to replace failed disks without stopping access to the system. Thus, the data in the failed disk must be rebuilt and written to the replacement disk while
the system is in operation. Which of the RAID levels yields the least amount of interference between the rebuild and ongoing disk accesses? Explain your answer.
4. In the sequential file organization, why is an overflow block used even if there is, at th emoment, only one overflow record?
5. For each of the following two B+ trees, show the steps involved in the following queries: (Note: there are two B+ trees. You are supposed to answer question #a and #b for both trees).
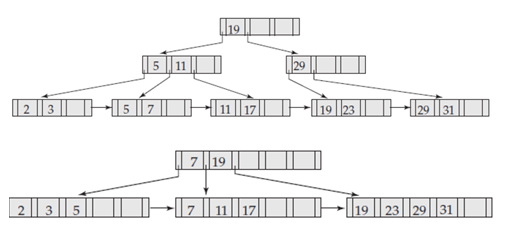
a. Find records with a search-key value of 7.
b. Find records with a search-key value between 3 and 17, inclusive.
6. What are the causes of bucket overflow in a hash file organization? What can be done toreduce the occurrence of bucket overflows?
7. Why is a hash structure not the best choice for a search key on which range queries are likely?
8. Suppose you need to sort a relation of 40 gigabytes, with 4 kilobyte blocks, using a memory size of 40 megabytes. Suppose the cost of a seek is 5 milliseconds, while the disk transfer rate is 40 megabytes per second.
a. Find the cost of sorting the relation, in seconds, with bb = 100.
b. How many merge passes are required?