Reference no: EM13896515
Question 1:
a) Name four socket functions (C functions) used to create client/server applications.
b) Name the five layers in a typical TCP/IP computer network.
c) What are the services provided by TCP?
d) The source and destination port numbers are included in the packet header. Which layer needs to be able to read these port numbers?
Question 2: (The Application Layer)
a) If an FTP client is in active mode, what are the two FTP commands (protocol commands) issued by the client when the user issues:
ftp> ls
b) If an FTP client is in passive mode, what are the two FTP commands (protocol commands) issued by the client when the user issues:
ftp> get
c) The command netstat is used by a system administrator. Explain the difference between LISTEN and ESTABLISHED states.
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 localhost:1234 *:* LISTEN
tcp 0 0 localhost:43000 it046500:20 ESTABLISHED
d) How many simultaneous connections does HTTP needs in order to download a single file? How many simultaneous connections does FTP needs in order to download a single file?
e) Briefly explain what is a DNS (Domain Name Service) iterated query. Explain why this method is important to keep the scalability of the DNS.
Question 3: (The Transport Layer)
a) A distributed system uses UDP to transfer files between nodes. You are asked to design a simple reliable protocol to replace it. What are the essential elements that you need to include in such a protocol? Your solution should focus on possible lost and damaged packets, not performance.
b) Explain the difference between Go-Back-N and Selective Repeat. Given a choice, which one is better for the performance of the network?
c) Explain the difference between "Congestion Control" and "Flow Control" from the view point of a transport protocol.
Question 4. (Network Layer)
a) What are the two important functions provided by the network layer protocols? Emphasize the importance of the difference between the two functions.
b) The network administrator checks an Ethernet card configuration using the command ipconfig. He extracts the values for the IP address and for the Mask:
IP address 192.123.246.12
Mask 255.255.255.128
Write two examples of IP addresses that this machine can access:
1) one IP address that is accessible directly (no routing) by this machine.
2) one IP address that is only accessible via the gateway (router).
c) There are four routers connected via certain links (Figure 1). Suppose that the following table is used for the initialisation of D's routing table:
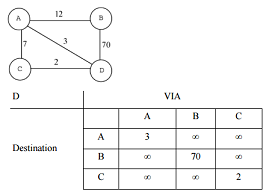
And the minimum cost is an array of 4 integers in the order A, B, C, D:
A advertises its minimum costs as: 0, 12, 7, 3
B advertises its minimum costs as: 12, 0, ∞, 70
C advertises its minimum costs as: 7, ∞, 0, 2
Show the first update on D's table if node D simultaneously receives packets with the minimum cost information from the routers A, B and D.
d) There are possibly hundreds of millions of IP addresses in the Internet. Explain why the routing tables in TCP/IP routers do not need to contain lots of entries, and are usually rather small.
Question 5. (Data-link and Physical Layers)
a) What is the purpose of CRC (Cyclic Redundancy Check)?
b) Compute the CRC value for the character "1110 0001" considering:
- the algorithm uses a standard polynomial method with 16 bits
- the generator is 0x8005
- no reverse bytes, no reverse results
Write the final result of the CRC in hexadecimal.
c) Collisions are a challenging problem for data link protocols. Explain the main differences between data-link layer protocols for wired networks and protocols for wireless networks.
d) Explain brifly how the ARP protocol keeps a table with the IP addresses and correspondent MAC (hardware) addresses.
Question 6. (Network Security)
a) MD5 is a well known method for message digests. Message digests find a fixed-length number (say, 128 bits) that correlates to a certain file.
Give two reasons why CRC is not a suitable method to be used as a message digest, even though CRC also finds a fixed-length number that correlated to a file.
b) Considering the RSA algorithm, find suitable e and d for the following pair of prime numbers, explaining how you chose them:
p = 5 q = 11
n = ?
z = ?
e = ? d = ?
c) Discuss the difference between asymetric encryption and symmetric encryption. Complete the table stating advantages and disadvantages of these two encryption methods.
d) Explain briefly what is a "packet sniffing" attack. Discuss and compare the implications of such atacks for wired networks and wireless networks.