Reference no: EM132064492
Assessment 1
Question 1. What is the rationale behind IP address scheme, why it is used, why we need subnets and how netmaking solves it?
Question 2. What are Public and Private IP ranges?
Question 3. What are the four main classes in IPV4?
Question 4. Design a head office local area network, you need to segregate your network into three parts:
1. A network for Administrative and Accounts departments (around 25 nodes)
2. A network for IT management (around 200 nodes)
3. A network for rest of the departments (around 120 nodes)
Assessment 2
1. Consider a network with network address 192.168.10.0/24, divide this network into 6 equal size subnets. And find followings
a. Subnet mask
b. Size of a subnet
c. Network addresses of each subnet
d. Broadcast addresses of each subnet
e. First 2 IP addresses of each subnetwork.
2. Answer following questions based on thee values given below
• Number of needed usable hosts in a single sub net - 22
• Network Address - 201.168.75.0
- I. Address class
- II. Default mask
- III. subnet mask
- IV. Number of bits borrowed
- V. Total number of subnets
- VI. Total number of host addresses
- VII. Number of usable addresses in a single subnet
- VIII. What is the 5th subnet range?
- IX. What is the net id of the 5th subnet?
- X. What is the subnet broadcast address for the 4th subnet?
- XI. What are the first and last assignable addresses for the 3rd subnet?
3. Based on the information in the graphic shown, design a network addressing scheme that will supply the minimum number of subnets, and allow enough extra subnets and hosts for 100% growth in both areas. Circle each subnet on the graphic and answer the questions below.
IP Address 172.16.0.0
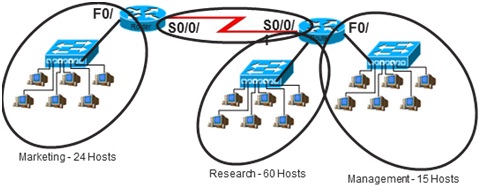
a. Address class Custom subnet mask
b. Minimum number of subnets needed
c. Extra subnets required for 100% growth
(Round up to the next whole number)
d. Total number of subnets needed
e. Number of host addresses in the largest subnet group
f. Number of addresses needed for 100% growth in the largest subnet
(Round up to the next whole number)
g. Total number of address needed for the largest subnet
h. Start with the first subnet and arrange your sub-networks from the largest group to the smallest.
- I. IP address range for Research IP address range for Marketing
- II. IP address range for Management
- III. IP address range for Router A to Router B serial connection
Assessment 3
You are required to answer these questions individually, based on above activity.
Question 1. What is an enterprise network?
Question 2. What are typical network design business goals? Describe them in your own words.
Question 3. Why it is necessary to find what applications are/will be running in the network? How a network application needs a network throughput?
Question 4. What business constraints can limit or create boundaries on your network design?
Assessment Task. Based on your learnings, you are required to perform a business analysis and create a solution for XYZ pty ltd.
XYZ Pty Ltd. Is a financial solutions and advisory firm based in UK, starting its business in Australia. Their plan is to build a local data centre for their financial applications that they want to promote in Australia, these applications can be used via cloud and hence they can be considered SAAS solution for financial planning. They have requested expression of interest and finalized Equinix as the data centre hosting provider.
They will create a setup of following servers in Equinix Sydney:
1. A web server farm, consisting of 4 web servers.
2. Two application servers
3. A cluster of database servers
You are required to create a network diagram and select network hardware that will support this setup. Equinix demands XYZ to build up their own design, procure the hardware and then set it up.
For all internal infrastructure, Equinix has given XYZ the network of 192.168.10.0/27.
A1. Please verify how many subnets can be created from above network, and allocate them to following design:
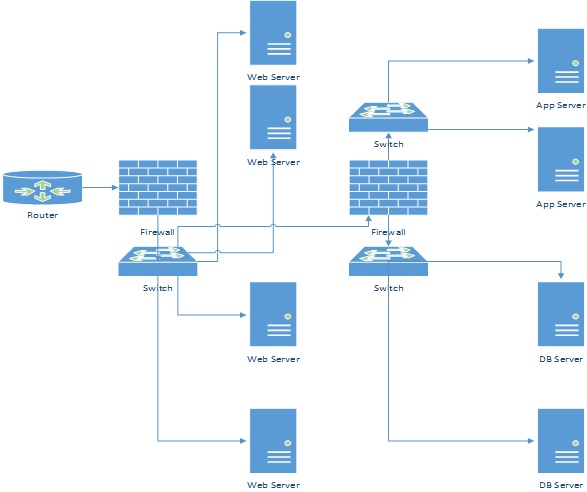
A2. Please show your work here:
A3. Fill following table based on your calculations:
A4. Now allocate IP addresses to all devices and interfaces
B. Chose what network devices will be fit for the design. Chose the vendor, hardware model and justify your selection.
XYZ will also have their head office in Sydney CBD. They plan to have around 25 employees and an internal back office support in a small network room where their local servers for back office will be hosted.
C. Please create the network for the head office.
1. A router that will connect to the internet, as well as the Equinix XYZ setup.
2. A firewall for the head office
3. A network for back office infrastructure:
3.1 A mail server
3.2 A DNS server
3.3 An Active Directory Server
3.4 A SharePoint File share server
4. A network for the 25 desktops or laptops
You need to look after the switching, subnetting and routing. You need to justify if any Public IP addresses are required and why? If you chose to use Private IP addresses, justify them as well.
C1. Please provide a complete network diagram of the head office network.
C2. Please provide a diagram of how head office will connect to the Equinix data centre.
C3. Please fill following table with your network design scheme.
Attachment:- Assessments.rar