Reference no: EM133552323
Introduction to Computer Systems and Networking
LO 1 Explain the theoretical underpinning of current computer technology, networking, security and their operational standards.
LO 2 Identify the components and describe the functions of computer hardware and peripherals.
LO 3 Representing text, image, audio and video data in binary format and converting them to HEX, or decimal where required.
LO 4 Analyse different computer systems and recommend/design a suitable computer system for a given application.
LO 5 Understand the CPU architecture and write fetch/execution cycles for program instructions.
Part 1 - Data Representation
Question 1. Use the ASCII table and convert the following binary numbers to text. Then find the decimal and hexadecimal equivalent of the text that you have found.
#1
01001000 01100101 01101100 01101100 01101111 00101100 00100000 01000111 01101111
01101111 01100100 00100000 01001101 01101111 01110010 01101110 01101001 01101110
01100111 00101110
#2
01000010 01101001 01101110 01100001 01110010 01111001 00100000 01101110 01110101
01101101 01100010 01100101 01110010 01110011 00100000 01100001 01110010 01100101
00100000 01100110 01110101 01101110
#3
01001000 01110101 01101101 01100001 01101110 01110011 00100000 01100011 01100001
01101110 00100000 01101110 01101111 01110100 00100000 01110010 01100101 01100001
01100100 00100000 01110100 01101000 01100101 01101101
#4
01000010 01110101 01110100 00100000 01100011 01101111 01101101 01110000 01110101
01110100 01100101 01110010 01110011 00100000 01100011 01100001 01101110
#5
01000011 01100001 01101110 00100000 01111001 01101111 01110101 00100000 01110010
01100101 01100001 01100100 00100000 01110100 01101000 01100101 01101101
PART 2: Multiple Choice Questions: Little Man Computer
1. What is the Little Man Computer (LMC)?
A. A small physical computer used for educational purposes.
B. A theoretical computer model for teaching computer architecture and programming.
C. A powerful supercomputer used in research institutions.
D. A pocket-sized computer for personal use.
2. How many mailboxes (memory locations) does the Little Man Computer have?
A. 10
B. 50
C. 100
D. 256
3. What is the range of values that can be stored in a single mailbox of the Little Man Computer?
A. 0 to 99
B. -99 to 99
C. 0 to 255
D. 000 to 999
4. What is the purpose of the accumulator (ACC) in the Little Man Computer?
A. To store the program instructions.
B. To store intermediate results during program execution.
C. To display the output of the program.
D. To store the user's input data.
5. Which Little Man Computer instruction is used to add two numbers together?
A. ADD
B. SUB
C. STA
D. INP Ans:
6. What does the LDA instruction do in the Little Man Computer?
A. Loads a value from the mailbox into the accumulator.
B. Loads the address of the mailbox into the accumulator.
C. Loads a value from the accumulator into the mailbox.
D. Loads the instruction code from memory into the accumulator.
7. Which Little Man Computer instruction is used to unconditionally jump to a specified instruction?
A. BRA
B. BRZ
C. BRP
D. OUT Ans:
8. Under what condition does the BRZ instruction in the Little Man Computer perform a jump?
A. When the accumulator is zero.
B. When the accumulator is negative.
C. When the accumulator is positive.
D. When the accumulator is greater than zero.
9. What is the purpose of the OUT instruction in the Little Man Computer?
A. To output the value stored in the accumulator.
B. To output the memory address of the accumulator.
C. To output the program execution status.
D. To output the instruction code of the current operation.
10. Which Little Man Computer instruction is used to read input from the user and store it in the accumulator?
A. ADD
B. INP
C. OUT
D. LDA
11. What is a parallel bus in computer architecture?
A. A bus that can transfer multiple bits simultaneously on separate lines.
B. A bus used only for internal communication within a CPU.
C. A bus that transfers data sequentially on a single line.
D. A bus that connects two separate computers for data sharing.
12. Which of the following statements is true about parallel buses?
A. They are more susceptible to noise and interference compared to serial buses.
B. They are typically slower than serial buses for data transfer.
C. They use a single data line to transfer multiple bits simultaneously.
D. They are commonly used for long-distance communication in networking.
13. What is the main advantage of using parallel buses?
A. Lower cost and simplicity of implementation.
B. Ability to transfer data over long distances without signal degradation.
C. Higher data transfer rates due to simultaneous transfer of multiple bits.
D. Compatibility with various types of devices and protocols.
14. Which type of bus is commonly used to connect peripheral devices such as printers and scanners to a computer?
A. Parallel bus
B. Serial bus
C. USB bus
D. Ethernet bus
15. What is a serial bus in computer architecture?
A. A bus that can transfer multiple bits simultaneously on separate lines.
B. A bus used only for internal communication within a CPU.
C. A bus that transfers data sequentially on a single line.
D. A bus that connects multiple computers to form a network.
16. Which of the following statements is true about serial buses?
A. They are more suitable for short-distance communication compared to parallel buses.
B. They are typically faster than parallel buses for data transfer.
C. They use multiple data lines to transfer data simultaneously.
D. They are not commonly used in modern computer systems.
17. What is the main advantage of using serial buses?
A. Lower cost and simplicity of implementation.
B. Ability to transfer data over long distances without signal degradation.
C. Higher data transfer rates due to simultaneous transfer of multiple bits.
D. Compatibility with various types of devices and protocols.
18. Which type of bus is commonly used for high-speed communication between the CPU and memory in modern computer systems?
A. Parallel bus
B. Serial bus
C. USB bus
D. PCI Express (PCIe) bus
19. In a serial bus, how is data transmitted?
A. Multiple bits are transmitted simultaneously on separate lines.
B. Data is transmitted one bit at a time on a single line.
C. Data is transmitted in packets containing multiple bytes.
D. Data is transmitted using multiple parallel data lines.
20. Which type of bus is more suitable for applications requiring long-distance communication, such as connecting devices in different rooms or buildings?
A. Parallel bus
B. Serial bus
C. USB bus
D. Ethernet bus
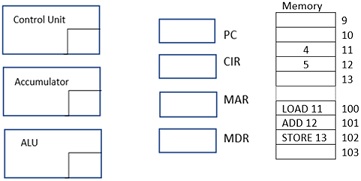
Question 3
Using the Figure below explain how we can add 4+5 in the processor's Registers Cycle.