Reference no: EM132515972
CIS114-6 Network Systems and Administration - Majan University College - University of Bedfordshire
Learning Outcome 1: Demonstrate deep and systematic understanding of system and networking concepts, including principles, technologies, and emerging trends.
Learning Outcome 2. Scientifically and critically analyse, implement and evaluate networking techniques, technologies, strategies and methodologies used in industry. Apply analytical and problem-solving skills in order to select and implement networking solutions appropriate to multiple organisational and environmental contexts.
Your Problem is to implement a virtualised environment-based solution demonstrating the operation of a VPN operating in site-to-site (Tunnel mode). Your virtual machines (VMs) requirements must include 2 VyOS routers (fully configured using the VyOS router own commands - similar to Juniper and Cisco routers commands
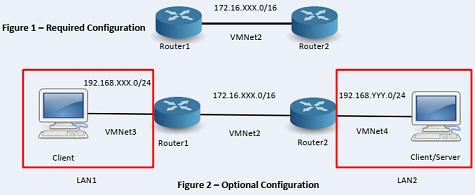
Figure 2 shows an optional configuration where additional XP VMs are to be used to demonstrate the VPN operations in both site-to-site and remote VPN (Tunnel and Transport modes) with additional Wireshark captures to be performed from one of the XP VMs.
Use of a command line sniffer such as tcpdump should is required on the networks to demonstrate the mode of operation.
You are required to either build the VMs from scratch or use the official VyOS VM available from our FTP server (see document on BREO), Dr Ali Mansour's shared Google drive (see link on BREO).
Problem 1 Implement the topology shown in Figure 1 with fully functional routers (i.e. a network connecting the two VyOS routers).
The network should be configured, tested, demonstrated, and clearly documented (part of Problem 3) showing its full operation. Routing between the two routers must be configured using any form of routing. Details of your routing implementation must be clearly stated/shown.
Problem 2 Configure, test, and demonstrate the VPN operation.
Captured traffic must be shown to demonstrate the operation of the VPN and when the VPN is not active.
Problem 3 Technical report documenting all the work done in the previous tasks. See the points below under Documentation Requirements.
Attachment:- Network Systems and Administration.rar
|
What is the most profitable production schedule
: Determine whether the Printing division can meet the sale demand next month.What department is a constraint, if any? What most profitable production schedule
|
|
Describe the competitive model of a firm
: Consider the competitive model of a firm where each firm has an identical linear supply curve (optimal supply rule). As the number of firms in the industry.
|
|
Mortgage with interest rate
: You bought a house with price of $250,000. Your LTV (loan-to-value ratio) is 80%. You choose the 30-year mortgage with interest rate 6%.
|
|
What is the internal rate of return
: What is the internal rate of return (IRR) of a project costing $3,000 (at year 0); having after-tax cash flows of $1,500
|
|
Systematic understanding of system
: Demonstrate deep and systematic understanding of system and networking concepts, including principles, technologies, and emerging trends
|
|
What is the reason the inmates are being given the drugs
: Why are diagnosed mental health problem inmates being held in a jail-type facility? What is the reason the inmates are being given the drugs?
|
|
What is standard deviation of the portfolio return
: The volatility of IBM and MSFT are 35% and 30%, respectively, and the correlation between IBM and MSFT is 0.6. What is standard deviation of the portfolio retur
|
|
Simulation experience scenario
: What are some ways that you see the principles of Incident Command demonstrated in this simulation, and some ways they could have been implemented better?
|
|
What is the effective borrowing cost
: What is the effective borrowing cost if the loan will be prepaid at the end of nine years? Show the calculations in Excel.
|