Reference no: EM13380243
Study carefully the following network topology. It is required that the small business Smart Office Services Pty Ltd have its Central office (HQ) and two branch offices (BRANCH1 and BRANCH2) linked via serial leased lines using routers.
You will be assigned a SINGLE IP Address to configure this network. Your lecturer will email you the IP address. You must need to reply with a confirmation e-mail once you have received your allocated IP address.
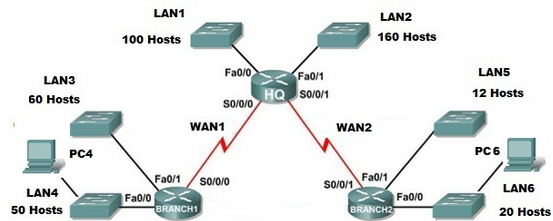
Examine the network requirements and answer the following ten questions. Keep in mind that IP addresses will be needed for each of the LAN interfaces.
Question 1. How many subnets are needed in the topology?
Question 2. Construct a table to list each subnet's information such as router interfaces, available IP Addresses range, broadcast address, subnet mask, and the default gateway. Please show the working. [Note: VLSM must be used in the most efficient way to subnet the given IP address. The highest available IP address of a subnet should be assigned as the default gateway of the subnet. PC4 and PC6 should be assigned the lowest available IP addresses of LAN4 and LAN6 respectively.]
Question 3. What cable type should be selected between two routers? Explain the reason.
Question 4. Usually, the clock rates are assigned by ISPs. From the clock signal viewpoint, what are both ends of a serial link called?
Question 5. Construct the topology in the packet tracer software. Select any one of the routers in the topology, and using appropriate command(s) find out and list the following information about the router: version number of the IOS, sizes of different memories (ROM, RAM, Flash and NVRAM).
Question 6. Using the packet tracer, configure the routers as follows:
- Name the routers and label them as HQ, BRANCH1 and BRANCH2.
- Set the secret password as 'class' on all routers.
- Configure all router interfaces and PCs.
- Configure TELNET on the HQ router with a password of 'xyz123' and (a suitable) MOTD.
- Save the changes on all routers.
Question 7. Select, configure and justify necessary static routes on three routers to make the successful connection between routers.
Question 8. Ping the PC4 from the PC6. Record the information flow in EVENT LIST of simulation and explain the PDU information such as TYPE and involved layers in each stage.
Question 9. Which protocol is used by PING? List the names of two PING messages.
Question 10. Define network convergence. How can you identify your configured network has reached convergence?