Reference no: EM13722350
You are required to set up a small network with network ID: 210.15.5.96/27. In this network, there are three routers, two servers, one acting as DHCP Server and another as Mail/DNS Server.
You can use Cisco Packet Tracer for this assignment (more information on use of Packet Tracer can be discussed with your Lecturer in Tutorial class).
Topology is as shown below:
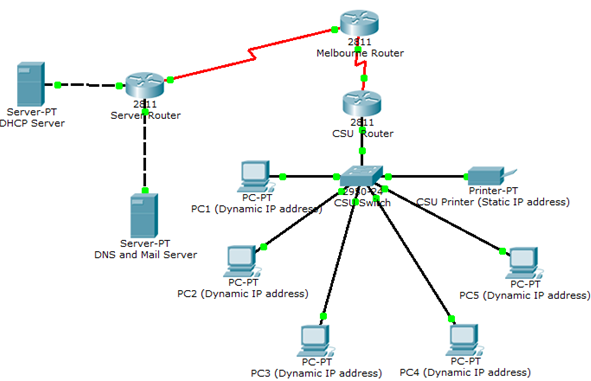
The requirements are as follows:
1. CSU network has only 10 networking devices (including printers, scanners and PCs etc.)
2. CSU network require only 5 dynamically assigned IP addresses, so PC1-PC5 will get IP address from DHCP Server, these address must be starting from 210.15.5.113
3. Configure DHCP Server for CSU network
4. Configure MAIL server for CSU.com, create two email user IDs as follows:
5. [email protected] user name: jatinder password: abc123
a. <Your first name>@csu.com user name: <your first name> password: xyz123
6. MAIL Server will also act as DNS Server for CSU Network, so you also need to configure it as DNS Server
7. When subnetting the network, ensure that the subnet allocated to CSU Network must have IP address mentioned in step 2. Other subnets/IP address must be configured in ascending order as follows:
a. Lowest subnet to DHCP Server
b. Next subnet to DNS/MAIL Server
c. Next subnet to connect Server Router and Melbourne Router
d. Next subnet to Melbourne Router and CSU Router
8. All Servers and Printer should be configured with static IP addresses, all PCs should be configured with Dynamic IP address
9. Use RIP Version2 as routing protocol
Fill the table below with information:
Device IP Address/ Subnet mask
DHCP Server IP address
DHCP Server Gateway IP address
DNS/MAIL Server IP address
DNS/MAIL Server Gateway IP address
Server Router Serial Interface address
CSU Router Serial Interface address
CSU Printer IP address
CSU Printer Gateway address
PC1-PC5 Gateway address
Following information must be provided as snap shots:
1. Show routing tables of all three routers
2. Show running configuration of CSU Router
3. Ping from PC1 to DNS Server
4. Ping from PC5 to DHCP Server
5. From PC1 send and receive minimum 4 email between you and jatinder and show the snap shot of conversation as per example given below:
6. Show dynamically obtained IP address by PC1
7. Show the DHCP Server setting
8. Submit your packet tracer file by email (to your class lecturer)
9. Properly drafted assignment submission
10. Clear Subnetting calculations with logical topology
11. Explain (one page minimum) the functioning and purpose of all setting you used in DHCP Server in this assignment, also provide APA style references.
|
Let g = (v, e) be an undirected graph with v
: Let G = (V, E) be an undirected graph with V = {1, . . . , K}. Let C1, . . . , CL be the set of maximal cliques in G. Let p(x) = (1/Z)*exp [Sum_l=1toL(ψ_l(x_Cl))]
|
|
Explain the process of strategy mapping
: Explain the process of strategy mapping and how it relates to performance management and establishing value propositions.
|
|
Determine the bounds on the p-value
: Determine the bounds on the p-value that would be used in testing each of the following null hypotheses using the p-value approach.
|
|
Demonstrate ethical scholarship in accurate representation
: Write your responses in a clear, concise, and organized manner; demonstrate ethical scholarship in accurate representation and attribution of sources; display accurate spelling, grammar, and punctuation per APA (6th edition) standards.
|
|
Set up a small network with network
: Required to set up a small network with network ID: 210.15.5.96/27. In this network, there are three routers, two servers, one acting as DHCP Server and another as Mail/DNS Server.
|
|
What is the acceleration of the turkey
: The Thanksgiving turkey (mT = 7.0 kg) is in the center of the table, on the tablecloth. what is the acceleration of the turkey
|
|
Discuss your own theory of personality
: 1.In a three to four page paper, respond to the following: a.Discuss your own theory of personality, and explain how your Christian faith and the theories of personality you have studied complement each other in the lifelong challenge of knowin..
|
|
Explain the honesty and legitimacy of a franchise
: What clues should you look for that should arouse your suspicions regarding the honesty and legitimacy of a franchise. Identify at least eight.
|
|
Most useful for coping with death and grief
: Which of the following concepts did freud believe to be most useful for coping with death and grief?
|