Reference no: EM133127391
Question:
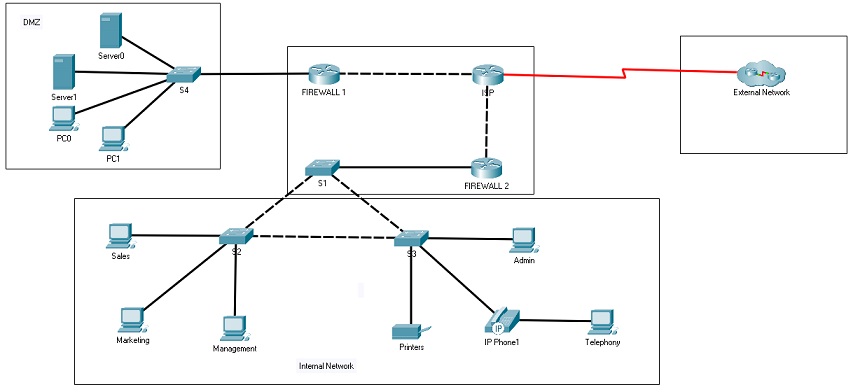
Based on your original design, Redesign a flat network with the following rules:
All you have to do is add the two new groups and answer the questions below:
You are expected to add access for two groups with appropriate security into the new network:
1) Risk management and Internal Audit (a single group) need full access to all systems on the network to be able to track all activity for risk management ad compliance checking purposes. However, their systems should be out of reach from anyone not in that group.
2) HR will operate fully remote - but need the ability to connect to guest wireless when they come in to the office space(s) and be able to use the office phones and printers (phones are all VoIP and hence the laptop needs to be able to link to the phone over the network).
What modifications/additions/enhancements are required to accommodate this? IF the network diagram will change, update the submitted diagram appropriately. Also, explain any additional controls (firewall rules, proxy configuration, IDS/IPS configuration or others) required to accomplish this enhancement securely.