Reference no: EM13892376
A.
a. Encrypt the message "meet me at the usual place at ten rather than eight oclock" using the Hill Cipher with the key 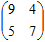 .
.
Show your calculations and the result.
b. Show the calculations for corresponding decryption of the ciphertext to recover the original plaintext.
B. Determine the values of Φ(27), Φ(49) and Φ(440), where Φ(n) is the Euler's Totient Function.
C Find 3201 mod 11; and 2341 mod 341
D. Determine the multiplicative inverse of x3 + x + 1 in GF(24) with m(x) = x4 + x + 1.
E. Develop a table similar to Table 4.9 on page 121 of the textbook for GF(28), with m(x) = x8 + x4 + x3 + x2 + 1 (from 0 to g14)
F The Miller-Rabin test can determine if a number is not prime but cannot determine if a number is prime. How can such an algorithm be used to test for primality?
G. Given x≡ 2 (mod 3), x≡2 (mod 7), and x≡3 (mod 5), please solve the x by using Chinese Remainder Theorem.
H. Given p = 17; q = 31; e = 7; C = 128, please calculate the d value for private key and recover the original plain text message M. (Need to show the details of the calculation in details)
I. User A and B use the Diffie-Hellman key exchange technique with a common prime q = 71 and a primitive root α = 7.
a. If user A has a private key XA= 5, what is A's public key YA?
b. If user B has a private key XB= 12, what is B's public key YB?
c. What is the shared security key?
J. Using the extended Euclidean algorithm, find the multiplicative inverses of
a. 13 mod 2436
b. 144 mod 233
K. Draw a matrix similar that shows the relationship between security mechanisms and attacks.
|
Does this practice impede quality care
: Take a position on whether or not you agree with the notion that a person is forced to see a PCP before being referred to a specialist. Does this practice impede quality care? Can the delay in seeing a specialist cause greater harm to a patient?
|
|
Discussion of kin networks
: 1. The remarried family has been called an incomplete institution. What does this mean? How does this affect the people involved in a remarriage? Include a discussion of kin networks and family law. Do you think this situation is changing?
|
|
What happen to the price for which investors could sell bond
: If tomorrow that probability is changed to .4 for the succeeding year, what will happen to the price for which the investors could sell their bond?
|
|
Successfully compete in the global marketplace
: As current and future managers of technology and innovation, what approaches and initiatives do you plan to utilize to ensure that your organization continues to successfully compete in the global marketplace?
|
|
Relationship between security mechanisms and attacks
: Draw a matrix similar that shows the relationship between security mechanisms and attacks - Show the calculations for corresponding decryption of the ciphertext to recover the original plaintext.
|
|
Do you believe that if costs of providing care goes up
: Take a position on the notion that costs and quality of care are connected. Do you believe that if costs of providing care goes up, quality goes down as shortcuts might be taken?
|
|
Develop a guerrilla marketing strategy for a small business
: Develop a guerrilla marketing strategy for a small business
|
|
Condition of a law or a rule
: A safe harbor is a condition of a law or a rule that lessens/removes a company's or individual's liability under some form of regulation, providing that the company or individual acts in good faith within the harbor.
|
|
What type of claim would each woman hold
: Ms. White and Ms. Black own farms next to each other. When the weather is good, each farm produces 2,000 tons of apples per year. What type of claim would each woman hold?
|