Reference no: EM13903695
Question 1: PCAP Analysis
Note: for this question, you need to download a PCAP file located in the course Moodle web site.
Peter is the Network Security Manager for a small spare parts business. The organisation uses an e-sales application to provide a front-end for its e-sales business. Customers are complaining that in the last two or three days the system has become very slow, taking them longer than normal to place their orders. This information has been corroborated by staff complaining that they are not happy with the slow response of the system to complete their daily activities. Peter suspects that the system has been the target of criminal hands and before he starts responding to the attack, he decides to investigate a little further the issue. First, he reviews the firewall logs and notices something abnormal in the type of traffic directed to a number of internal hosts including the organisation's web server. Curious about this traffic, Peter uses Wireshark to capture a trace of the traffic. [A section of this trace can be accessed from the course Moodle web site].
Based on the above fictional scenario and the provided PCAP:
(a) Identify the anomaly in the traffic this organisation is going through. What sort of evidence do you have to make this claim?
(b) What sort of utility or tool do you think probably the "attacker" is using to conduct this attack?
(c) Provide the IP address of the host used by the perpetrator. Based on this information, what can you tell about the profile of this individual? Explain why.
(d) What Wireshark filter do you think Peter used to produce the given PCAP? Explain why.
Question 2
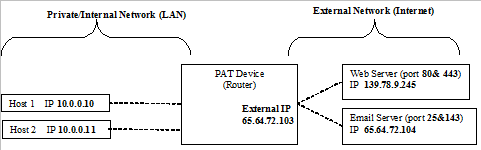
A small office has a single external IP address and a small router that provides PAT. The office router's external IP address is 65.64.72.103 and two of the internal hosts have the IP addresses 10.0.0.10 and 10.0.0.11. The hosts periodically connect to an external Web server at 139.78.9.245 and a mail server at 65.64.72.104.
Copy and complete the following PAT table, with the appropriate values.
|
Packet addressing on internal network
|
Packet addressing on external network
|
|
Source IP
|
Source Port
|
Destination IP
|
Dest. Port
|
Protocol
|
Source IP
|
Source Port
|
Destination IP
|
Dest. Port
|
|
10.0.0.10
|
1033
|
139.78.9.245
|
80
|
http
|
|
|
|
|
|
10.0.0.10
|
1035
|
65.64.72.104
|
25
|
smtp
|
|
|
|
|
|
10.0.0.11
|
1045
|
139.78.9.245
|
443
|
https
|
|
|
|
|
|
10.0.0.11
|
1065
|
65.64.72.104
|
143
|
imap
|
|
|
|
|
Question 3
You are the system's administrator of Reliable Power Supplies (RPS), a medium sized company that builds UPSs and switched power supplies for the computing industry. Your task is the analysis, design and configuration of a Firewall System that secures the inbound and outbound traffic at RPS. After conducting the needs analysis you have a clear picture of the type of firewall system that best suits RPS.
In the internal network, there is a special host (192.168.1.253/28) running an application that would be disastrous if it was compromised. Therefore for your design, you opt for a dual firewall system that you believe is the best option for this specific case. You also go for a demilitarized zone (Network Address 10.0.0.0/24) containing the e-mail (10.0.0.20/24) and Web services (10.0.0.30/24) of the company.
Apart from providing NAT services and Packet Filtering, the first firewall (part of the dual configuration) acts as a Web and FTP Proxy server. This first firewall is connected to the Internet via 200.27.27.10/25 and to the DMZ via 10.0.0.10/24.
The second firewall is used to filter traffic between the internal network and the DMZ. It is connected via 10.0.0.254/24 to the DMZ and via 192.168.1.254/28 to the internal network.
The internal network address is 192.168.1.240/28.
The security policy requirements used to configure the firewalls are outlined as follows:
RPS Web server contains public information including a product catalogue that is accessible to Internet users and it also provides secure online purchasing functionality using SSL/TLS. The internal users are also allowed to access all RPS WWW services; however they are allowed to access Internet WWW and FTP services only via the proxy located on the first firewall via port 3028. As mentioned, the internal network has a special host (192.168.1.253/28) which has complete access to any host and any services without using proxy services configured in the first firewall system. The remaining internal hosts must go via proxy on first firewall.
The security policy requirements also dictate the e-mail server to receive from and send messages to hosts on the Internet and the internal users; however these internal users are to retrieve their messages via IMAP.
Any other service which is not explicitly outlined in the security policy should be restricted from RPS network.
Your tasks:
1. Provide a network layout (network diagram) showing all the components of RPS network including both firewalls, the email and web servers, the DMZ, and all the internal hosts (Note that you should draw all the internal hosts. The number of internal hosts can be found from the internal network address given above). Ensure you label all hosts (servers, internal computers and firewalls) with appropriate names and write the IP addresses for each network interface.
Including all components of the network
Labeling all hosts with names and respective IP addresses
2. You are required to develop two sets of rules for the dual firewall. One will process traffic travelling between the Internet to the DMZ and Intranet. The other will process traffic travelling between the Intranet and the DMZ. You need to also explain what each rule does.
Meeting the requirements of the Internet rules
The descriptions of the Internet rules
Meeting the requirements of the Intranet/DMZ rules
The descriptions of the Intranet/DMZ rules
Question 4
DNS and ARP poisoning attacks are similar; however there are fundamental differences between the two. You are to research these specific differences contrasting the way the attacks are conducted and some of the countermeasures available. Ensure you use at least three in-text academic references to contrast these attacks.
Remember that you are not to repeat in your research what DNS and ARP poisoning attacks are. We already know that from our discussions in class. In writing about the differences between the two types of attacks, contrast for example the complexity of the attacks (which one is easy to conduct and why), the impact (consequences) of the attacks, which one is more common and the different mechanisms available to counter the attacks. Write no more than 300 words (about a page including in-text references).
Contrasting the complexity of the two type of attacks
Contrasting the impact (consequences) of the attacks
Contrasting the countermeasures
The format of the writing (referencing, grammar and structure)
Attachment:- PCAP Analysis.pcap