Reference no: EM13952374
Project: Prepare a Local IT Security Policy
Introduction
In Project 1, you developed an outline for an enterprise level IT security policy. In this project, you will write an IT security policy which is more limited in scope - a local IT security policy. This policy will apply to a specific facility - a data center. Your policy must be written for a specific organization (the same one you used for Project #1). You should reuse applicable sections of Project #1 for this project (e.g. your organization overview and/or a specific section of your outline).
If you wish to change to a different organization for project #2, you must first obtain your instructor's permission.
Your local IT security policy will be used to implement access control for the information, information systems, and information infrastructure (e.g. networks, communications technologies, etc.) which are housed within the data center. Your policy must protect the data center by preventing personnel who are not authorized to access or use the resources of the organization from gaining access and potentially causing harm (e.g. loss of confidentiality, integrity, or availability). Such personnel may include employees, contractors, vendors, and visitors. You should also address unauthorized individuals who may attempt to gain access to the facility, its information systems, or its networks.
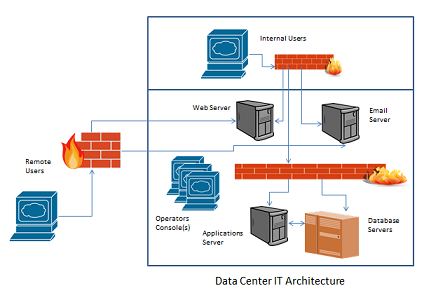
Your policy is being written by you as the facility manager. In this role, you are also the information system owner (ISO) for all IT systems and networks within the data center. The information systems hosted in the data center are shown in Figure 2-1.
The primary audience for your policy is the Tier 1 staff responsible for day-to-day operations and maintenance in the data center. Your policy will be communicated to other personnel and to the senior managers who are ultimately responsible for the security of the organization and its IT assets. These managers include: CEO, CIO/CISO, and CSO.
Research:
1. Research the subject of access controls and control measures (security controls) required for a data center. Suggested control measures are listed in Table 2-1.Use the IT architecture shown in Figure 2-2 to identify the types of systems and networks which must be secured against unauthorized access.
Table 2-1. Access Control Measures for a Data Center
- Concurrent Session Control
|
- Permitted Actions without Authentication
- Previous Logon (Access) Notification
- Publicly Accessible Content
|
- Unsuccessful Logon Attempts
- Use of External Information Systems
|
2. Using Figure 2-2, identify at least five specific types of information which are likely to be stored within the data center (use your organization's missing, products, and services). Research the types of access controls which must be provided to protect the confidentiality, integrity, and availability of such data. (Remember to consult Table 2-1.)
Figure 2-2. Data Center IT Architecture Diagram
Write:
1. Use the following outline to prepare your local IT security policy for the data center. See the policy template / sample file (attached to the assignment entry) for formatting and content suggestions for individual sections.
I. Identification
a. Organization: [name]
b. Title of Policy: Data Center Access Control
c. Author: [your name]
d. Owner: [role, e.g. Data Center Manager]
e. Subject: Access Control for [data center name]
f. Review Date: [date submitted for grading]
g. Signatures Page: [authorized signers for the policy: CEO, CISO, Data Center Manager]
h. Distribution List
i. Revision History
II. Purpose
a. Provide a high level summary statement as to the policy requirements which are set forth in this document.
III. Scope
a. Summarize the information, information systems, and networks to be protected.
b. Identify who is required to comply with this policy. See the project description for categories of personnel and other individuals.
IV. Compliance
a. Identify the measures which will be taken to ensure compliance with this policy (e.g. audits, compliance reporting, exception reporting, etc.)
b. Identify the sanctions which will be implemented for compliance failures or other violations of this policy.
c. Include information about how to obtain guidance in understanding or interpreting this policy (e.g. HR, corporate legal counsel, etc.)
V. Terms and Definitions
VI. Risk Identification and Assessment
a. Using Figure 2-1, identify potential control weaknesses, threats, and vulnerabilities ("risks") which could negatively impact the information, information systems, and information infrastructure for the data center.
b. Identify and discuss the level of risk associated with the identified weaknesses, threats, and vulnerabilities.
c. Identify the control measures which will be implemented to mitigate or otherwise address each risk or risk area.
VII. Policy
a. For each control measure, write a policy statement ("Shall" wording) which addresses the implementation of that control. (See Table 2-1.)
b. Include an explanatory paragraph for each policy statement.
2. Prepare a Table of Contents and Cover Page for your policy. Your cover page should include your name, the name of the assignment, and the date. Your Table of Contents must include at least the first level headings from the outline (I, II, III, etc.).
3. Prepare a Reference list (if you are using APA format citations & references) or a Bibliography and place that at the end of your file. (See Item #3 under Formatting.) Double check your document to make sure that you have cited sources appropriately.