Reference no: EM13983688
Project: Cloud Computing Security Policy
Background: A small non-profit organization (SNPO-MC) has received a grant which will pay 90% of its cloud computing costs for a five year period. This grant contains provisions which arise from the federal government's "cloud first" mandate and related IT reform efforts (see https://cio.gov/wp-content/uploads/downloads/2012/09/25-Point-Implementation-Plan-to-Reform-Federal-IT.pdf)
Before the organization can take advantage of the monies provided by this grant, it must present an acceptable cloud computing security policy to the federal agency which has issued the grant. This policy must also identify and address relevant requirements (items 3, 4, 5, and 6) as set forth in Part I: Section A "Apply ‘Light Technology' and Shared Solutions" of the federal government's25 point implementation plan.
Organization Profile: The organization is headquartered in Boston, MA and has two additional operating locations (offices) in New Orleans, LA and San Francisco, CA. Approximately 50 employees work in a formal office setting at one of these locations. These employees use organization owned IT equipment. The remaining 1,000 staff members are loaned staff or other volunteers who work from their home offices using personally owned equipment. The organization wants to shift to using more cloud-based computing resources so that it can avoid having to purchase new and/or replacement equipment.
Figure 6-1. SNPO-MC As-Is Enterprise IT Architecture
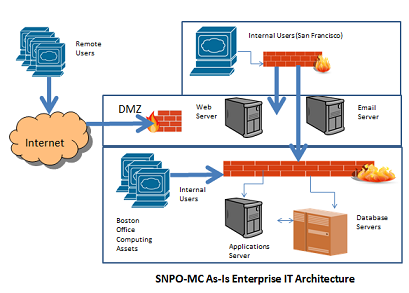
Definitions: Employees of the organization are referred to as employees.
Executives and other staff who are "on loan" from Fortune 500 companies are referred to as loaned staff members. Loaned staff members usually telework for the organization one to two days per week for a period of one year.
Volunteers who perform work for the organization are referred to as volunteer staff members. Volunteer staff members usually telework from their homes one to two days per week.
Cloud Computing includes but is not restricted to:
• Platform as a Service
• Infrastructure as a Service
• Software as a Service
Issues List:
• Who speaks with authority for the firm?
• Who monitors and manages compliance with laws and regulations?
• Ownership of content
• Privacy and confidentiality
• Enforcement
• Penalties for violations of policy
• Use by sales and marketing
• Use by customer service / outreach
• Use by public relations and corporate communications (e.g. information for shareholders, customers, general public)
• Use for advertising and e-commerce
• Use by teleworkers
• Review requirements (when, by whom)
• Use of content and services monitoring tools
• Content generation and management (documents, email, cloud storage)
Resources (suggested by the organization's IT Staff for your consideration):
1. https://www.nsa.gov/ia/_files/support/Cloud_Computing_Guidance.pdf
2. https://www.sans.org/reading-room/whitepapers/analyst/cloud-security-compliance-primer-34910
3. https://csrc.nist.gov/publications/nistpubs/800-144/SP800-144.pdf
Tasking:
1. Research best practices for cloud computing. Use the readings posted in the LEO classroom, the resources listed above, and at least three additional resources that you find on your own.
2. Write a policy which addresses the following requirements from the federal government's 25 point plan:
• Shift to a "Cloud First" policy
• Stand-up contract vehicles for secure IaaS solutions
• Stand-up contract vehicles for commodity services
• Develop a strategy for shared services
3. Create a transition strategy for moving from the "As-Is" enterprise architecture to cloud-based services. You should consider IaaS, PaaS, and SecaaS strategies. You should also address deployment considerations (private, public, community, hybrid clouds) and the criteria for selecting an appropriate deployment strategy. Document your transition strategy in a "background" section in your policy. (This strategy forms the basis for the "need" for security for cloud based services to be used by SNPO-MC in the future and should include the "to be" state for its Enterprise IT architecture.
4. Develop and document 10 to 15 policy statements which address requirements for securing the cloud-based "to-be" enterprise architecture. These statements should be specific and based upon best practices.
Your deliverable for this project is a 5 to 8 page professionally formatted draft policy which addresses security requirements for Cloud based services used by the non-profit organization. See the following resources for suggested formats.
• https://it.tufts.edu/cloud-pol
• https://www.american.edu/policies/upload/IT-Security-Policy-2013.pdf