Reference no: EM132062148
Assignment: First assignment: Step 1: Define a Computer class that can be used to describe your computer. The class must have at least two attributes. One variable must be an integer data type and the other must be a String data type. At least one method should be defined in your class. Step 1a: Prepare a class diagram to illustrate your Computer class. Copy to a Word document. Step 1b: Prepare the source code that implements your Computer class. Give your source code a filename of Computer.java.
Step 2: Prepare a program that utilizes your Computer class. The requirements for the program include prompting the user for input, making a calculation, and printing out the results. Begin by creating your pseudocode for this program. Once you have your pseudocode, copy it into your Word document. You can now begin writing your program.
Your program should prompt the user for information about their existing computer followed by information about a future, more desirable computer. This means that your program will create two instances of Computer class, the first instance reflects the existing Computer, and the second instance reflects the future Computer.
Use the Scanner class for obtaining input from the user keyboard. The program must calculate the difference (improvement) between the existing and future Computer class variables of integer data type. For example, Computer class may contain an integer variable named memory. The value of the memory variable for the existing Computer instance may be 8, while the value for this variable in the future Computer instance may be 10. Calculating the difference would indicate an improvement of 2.
Print to the screen the values for the existing computer class and the desired computer class, along with the calculated improvement.
Your assignment submittal should include your properly commented Java source code for your Computer class as well as for your program.
The first step should be to plan your program. Prepare a Word document that shows your program plan description including class diagram and your pseudocode defining program logic.
The second step should be to write the code based upon your planning document.
Second Assignment: Your consulting firm has been hired to develop a program that meets the following requirements.
Your program must provide a menu to the user. This menu should list three different products of your choice. Once the user selects one product, they should specify which state they are located. The state choices should include CT, VT, WI, CA and WA. State taxes vary for each state (7.5%, 7.8%, 6.8%, 7.2% and 6.4%, respectively). The user should then specify the desired number of cases (assume there are 12 items per case). The appropriate state tax should be added to the total cost of the product (item quantity multiplied by unit price).
Display the following to the user.
Name of the product selected
Number of cases
Number of items
Subtotal (units x price per unit)
State tax (with the percentage and state abbreviation in parentheses)
Total cost (subtotal plus state tax)
a) Your program needs to include at least one repetition statement, one selection statement, Scanner class, and at least one array in this code.
b) Appropriate calculations are necessary.
c) Print out to the user the above bulleted items.
Your assignment submittal should include your Java source code, class files, program design document including class diagrams and pseudocode.
3rd Assignment: You are the lead trainer for the software development team at a large telecommunications company. You have been tasked with preparing a training document that explains the principles of polymorphism, inheritance, and encapsulation. Research these principles and provide examples for each principle, showing how they would be used in software development. Be sure to answer the question of how each principle would be employed in the software development process.
Java programmers use class hierarchies for the purposes of inheritance. For example, given a Tree class, you could define Conifer and Deciduous subclasses that inherit from the parent Tree class, as follows:
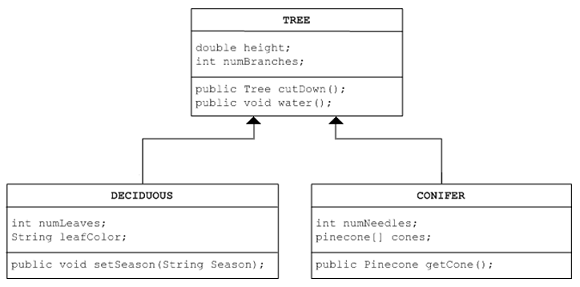
In your training document explanations regarding inheritance, depict inheritance by using a computer memory hierarchy in a class hierarchy diagram.
Deliverable: Prepare a 6-8-page document that provides detailed explanations for polymorphism, inheritance, and encapsulation. Research computer memory hierarchy and the topic to use in your inheritance explanations at this link, making sure to cite it in APA style if you use specific information from the article. Develop a class hierarchy diagram for the memory hierarchy found at the URL. Include in your class hierarchy diagram at least three subclass levels. Each class and subclass must include at least one variable and one method.