Reference no: EM133001957
Active class 7: Who is Instructing What
The learning objective of this class is to learn about routing and routing algorithms.
At the end of this activity, you should be able to:
1. Explain the control plane operation of the Network layer
2. Build a simple network in Cisco Packet Tracer and simulate static routing and dynamic routing.
This class activity is designed to be worked through active participation and collaborating with peers under the guidance of the teaching team in the class. The active classes are designed to be interactive, and they are here for you to extend your learning. However, these classes will only help you to enhance your learning if you come prepared.
Activity 1: Routing
This is a group activity. Therefore, you need to form a group of four (4) or five (5) people. At your table (or in MSTeams chat) discuss the following questions and conduct the role play with your group members. Remember to take notes as they will help you prepare your task submissions and complete other activities.
1. Assume your network has two routers and a separate LAN connects to each router as shown in the following figure.
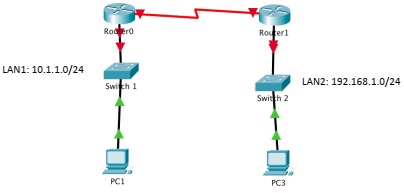
2. Now we are ready to do a role play. Two group members are acting as LANs (one member for each LAN). They are responsible for all the PC's connected to their corresponding LAN. Two group members (or one member) are acting as data plane of Router 0 and Router 1. The remaining member is acting as the control plane of both routers.
3. Now assume PC1 wants to send a message to PC3, you need to work together to support the request. Each device needs to list your configurations.
4. Discuss the responsibilities of the control plan of the routers. Tips: How router 0 knows about the LAN 2 and router 1
5. You are going to use these discussions for Activity 2 and 3.
Activity 2: Putting what you have learned into practice using Cisco Packet Tracer.
Now it's time to implement your network in Cisco Packet Tracer. Make sure to take screenshots of the networks you build, analysis, and verifications.
1. Open the packet tracer and implement the following network as a group and make sure to use Activity 1 discussions to configure each device in the network.
a. You need to make sure PC1, PC3 and PC5 can communicate with each other. Tip: You need to add static routing to each router now.
b. Verify that PC1 can communicate with both PC3 and PC5 using PING command and simulations.
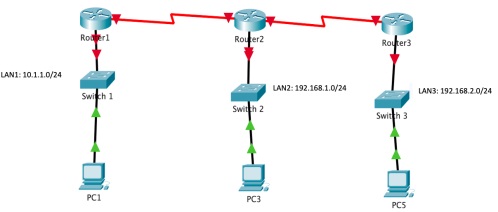
2. Now, add another serial connection between Router 1 and 3 and remove the direct connectivity between router 2 and 3.
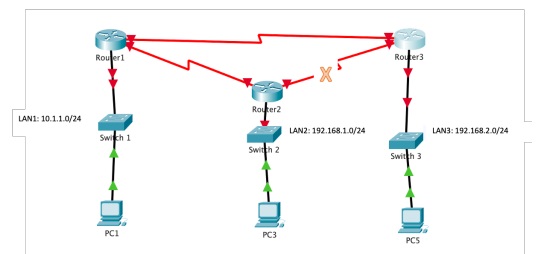
a. Discuss what changes now you need to make to enable the communication between PC1 and PC5 (Tip: what static routes you need to add).
b. Implement the changes and verify that PC1 and communicate with PC5 using PING command and simulations.
Activity 3: Alternative for Static Routing
In activity 2, you have noticed that you need to make changes in routers every time there is a change in the connection. Discuss the following with the group members.
1. Is there any alternative to stop manually configuring the routing table every time the connectivity changes?
2. What are the latest routing algorithms you can use?
3. Is there any routing algorithm available in Cisco Packet Traces?
4. Implement the same network as shown in the following figure. However, this time make sure to use the routing algorithm available in the routers that you use.
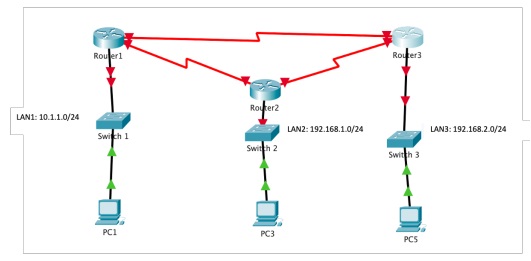
5. Verify the network connections using PING (in each PC).
6. Use the simulation tool to send a packet from PC1 to PC5. Have you seen any differences compared to the route you have seen in Activity 2? Explain what happened.
7. Now remove the connection between router 1 and 3 and use the simulation tool to send a packet from PC1 to PC5 without changing any configuration.
8. Explain what you observed.
Active class 8: Internet is Full of Network Protocols
The learning objective of this class is to learn the role of Network Address Translation (NAT) protocol, Dynamic Host Configuration Protocol (DHCP) and Internet Control Message Protocol (ICMP) which are (perhaps considered as) significant network layer protocols.
At the end of this activity, you should be able to:
1. Explain the functionalities of the mentioned protocols
2. Build a simple network and analyse the protocols.
Activity 1: Group Discussion.
It is predicted that we will have 50 billion IoT devices in our networks soon. Yes, just IoT devices! If you think about this, most devices need an IP address to communicate with the network. Discuss the following questions with your group members.
1. Do we have enough IP addresses to assign for each device that connect to the network?
2. Do we have any solution?
3. Explain a protocol that we can use along with IPv4 to conserve the global IP address space?
Activity 2: Who does assign an IP address when your computer connects to the network?
This is the role of DHCP. First, we are going to do a small role play to mimic DHCP. Each member of the group has a role to play. Assume your group is your local area network (LAN). For example, you could consider a LAN at home or at Campus or at your workplace.
1. One group member can act as a router with a DHCP server and other three members are host devices that try to connect to the network. These host devices could be a PC, a printer, and network storage device. A sample network is shown in the below figure.
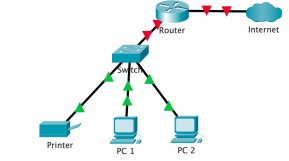
2. Assume the all the devices are physical connected as shown in the above figure. Now, your job is to set up the network and establish the connections with the router using DHCP. Each member needs to send/ respond with the correct message and message sequence to establish the connections and receive IP address for each host.
3. Draw a timing diagram to indicate the sequence of messages transferred between devices.
4. Next, we are going to implement a DHCP server in Cisco packet tracer and check the DHCP in action. Make use to take screenshots of the networks you build, analysis, and verifications. Open the packet tracer and implement the following network. You may need to use the same model of the devices shown in the diagram. Today, we are not going to use static IP configuration for the hosts as we are going to check the DHCP in action. Tips: You need to add a module with a fast ethernet port to the router, so that the router can support three LANs as shown in the below network diagram.
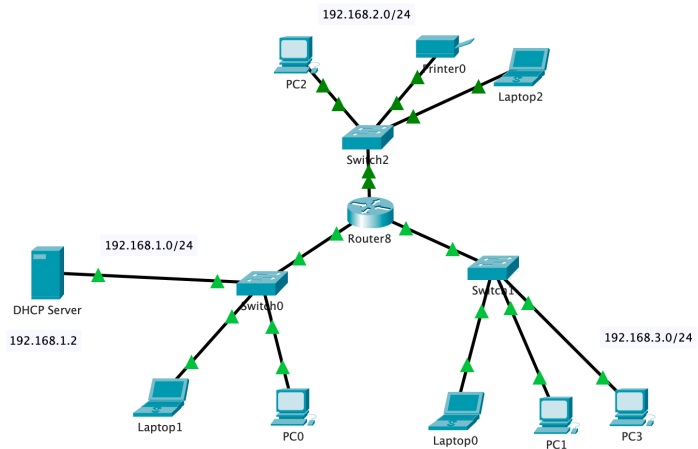
a. Set up the DHCP server by configuring network pools, default gateway, and IP address (use the subnets mentioned in the diagram).
b. Set up the router by configuring the interfaces and DHCP (use the subnets mentioned in the diagram).
c. Set up each host with DHCP to obtain IP configuration and verify the IP address and the default gateway configured.
d. Verify the connectivity between each host in the network.
Activity 3: ICMP
In this activity, we are going to use Cisco Packet tracer's simulation tool to explore ICMP. To do this, you are going to use the network that you have implemented in Activity 2.
1. Use the Simulation mode and send a simple packet from one host (Host A) from LAN1 to another host (Host B) in LAN2. In simulation tool, you can run the simulation step by step. When you go through each step, pay attention to the type of the message passed (highlighted in the below figure).
2. You may notice when Host A ping Host B, we use ICMP protocol. Double click on one entry as shown below to explore the ICMP message,
3. You should be able to view the packet details as follows.
4. Explain what information you can find in "outbound PDU details".
5. Have a closer look at the ICMP message format. Can you identify the type of ICMP message and specific information is in there (type and code)? You can refer to RFC792 for more help. https://datatracker.ietf.org/doc/html/rfc792
6. Can you identify the changes in ICMP message when you use a traceroute from Host A to Host B compared to what you have witnessed in the above question? Note that you can use tracert command in each device (in command prompt) similar to the way that ping command is used.
Above and Beyond Tasks:
Those who are targeting for Credit and above can complete the following task as part of Task 4.1C and 5.2D to demonstrate your deeper understanding on network layer.
1. Analyze DHCP in Wireshark (you may want to disconnect your wireless connection and connect it again whilst capturing the packets). You can show the sequence of DHCP messages and the details of those messages.
2. Why are different inter-AS and intra-AS protocols used in the Internet? What are the examples of these two different types of routing protocols?
Attachment:- Protocols.rar