Reference no: EM132850614
COMP2003 Securing Networks - Southern Cross University
Assignment - Practical network security setup
Task Description
In this assignment, you will perform necessary setup to install, configure and troubleshoot an SME network.
You must successfully implement the network on Packet Tracer (or similar) network simulation software and perform important steps to manage the network security configuration.
In particular, you will complete the following tasks:
• Task 1: Install and connect the devices into a network as shown in the diagram.
• Task 2: Set up and test the security
• Task 3: Network testing and troubleshooting
• Task 4: Network documentation
Scenario
You are a junior network administrator and because of your ongoing experience your manager has assigned you a new client to assist them setup their new network.
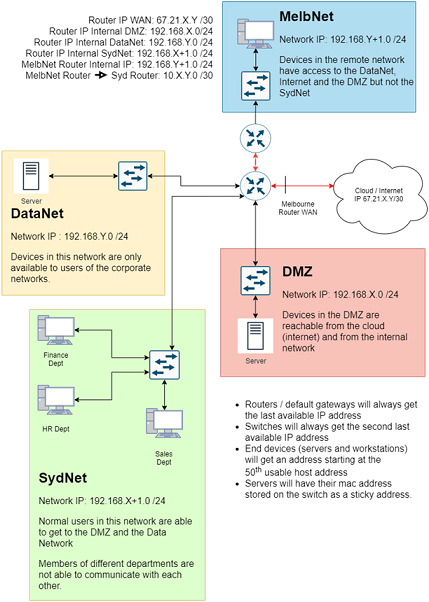
The design and requirements have been provided to you in a simple diagram and instruction set.
You have been advised of the following criteria:
1. Routers and default gateways are always set to the last IP address in the range.
2. Switches will always get the second last IP address in the range.
3. End devices (servers and workstations etc.) will get an IP address starting at the 50th usable host address.
4. Servers will have their MAC address stored on the switch. The following networks will be set up:
• DMZ - Used for placing internet facing devices to be able to be reached from the internet as well as the internal corporate network.
• Data Network (DataNet) - used for storing the internal company data that only the internal corporate users are able to access.
• Sydney Network (SydNet) - used by the normal users of the company in the head office that are able to access the internet, the internal servers network and the DMZ. There are multiple departments in the head office, and each should not be able to communicate with computers in other departments.
• Melbourne Network (MelbNet) - is for a remote office that are able to access the DMZ, the DataNet and the internet.
Your task is to configure the network in simulation software so that it can be tested before it is implemented.
You must devise any security options you deem appropriate to meet the requirements and configure and document them so they can be used when the network is implemented.
The following are the major assessment criteria of this assignment.
Task 1: Network environment setup
• Set up the routers, switches and PC's with the appropriate connections
• Perform basic configuration of the devices
• Test connectivity
• Save the configurations to the devices
Task 2: Security setup and performance
• Add the required security including any of the following:
o Switch port security
o VLAN's
o ACL's (most likely basic ACL's)
o static or dynamic routing
o Save the configurations to the devices
Task 3: Network testing and troubleshooting
• Correctly propose the hypothesis to be tested at each step e.g. connectivity between devices, security is working to stop X from occurring.
• Correctly identify the type of information that should be collected at each step
• Test the configuration using correct methodology
You must document what tests you will carry out, what the test is for and the result.
Consider using a table.
Task 4: Network Documentation
You must document your configurations for the devices you set up.
• Document the devices including:
o Host Devices (PC's and servers)
» Name/ID
» Link technology e.g. Ethernet
» Port Address e.g. Eth0
» Physical address e.g. MAC address
» IP Address
» Subnet Mask
» Default Gateway
» DNS
o Network Devices
» Interface configuration
• Name/ID
• Link technology e.g. Ethernet
• Port address e.g. G0/0/1
• Physical address e.g. MAC address
• Logical address e.g. IP Address / subnet mask
• Security applied
» Security Configuration
• Switch port security
• VLANs
• ACLs
• Routes
o Save the configurations to the devices
o Export the configurations (or copy/paste to a text file).
Attachment:- Practical network security setup.rar