Reference no: EM131670964
You have been hired as part of the network security team at UMUC. After completing orientation and training, your manager calls you into a meeting to discuss your first project.
The university has completed the implementation of the leased building in Adelphi, Maryland. The university realizes it needs to secure the faculty, students, and visitors network and data. With your background and skills, the university is looking to you for guidance.
In addition to helping the university secure its network, you are required to obtain your CompTIA Security+ certification within 60-days of being hired. As you will recall, the university leased building in Adelphi, Maryland was designed and implemented via the following layout:
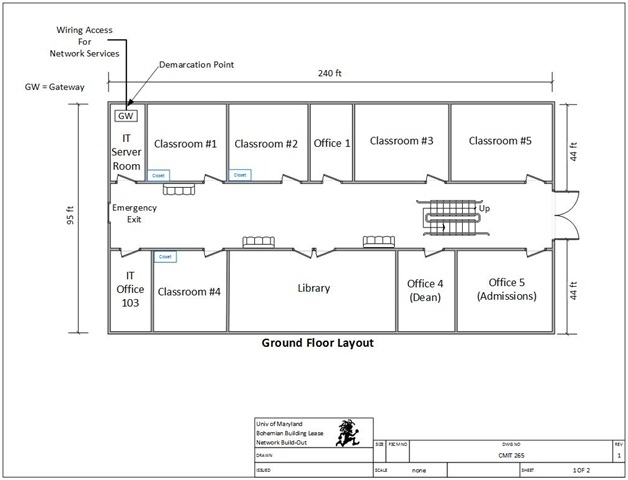
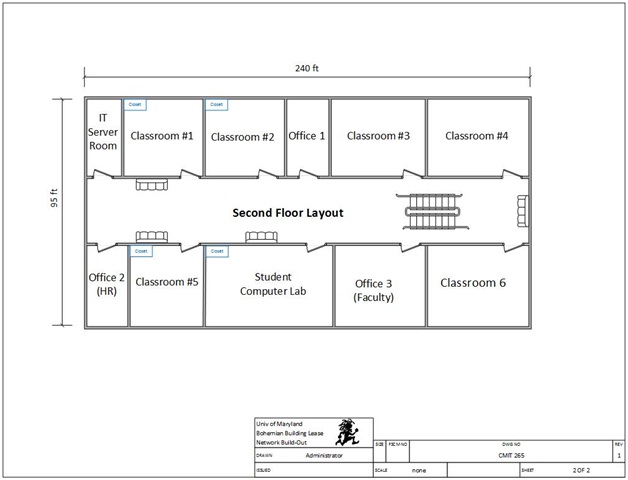
You've been asked to perform network security analysis and planning, secure the boundary devices, hosts, and software; and secure the data at rest and in transit.
Your deliverable should explain the requirement, propose a solution, and justify the solution. You should make use of the TestOutLabSim material to create the task, and study for CompTIA Security+ certification. You should also make use of other sources as required.
It is important that your deliverable explain the technical issues in layman's terms. Before you begin, make sure to review the Network Security Proposal (Parts 3).
Attachment:- Securing Data.rar