Reference no: EM131820526
Topology Diagram
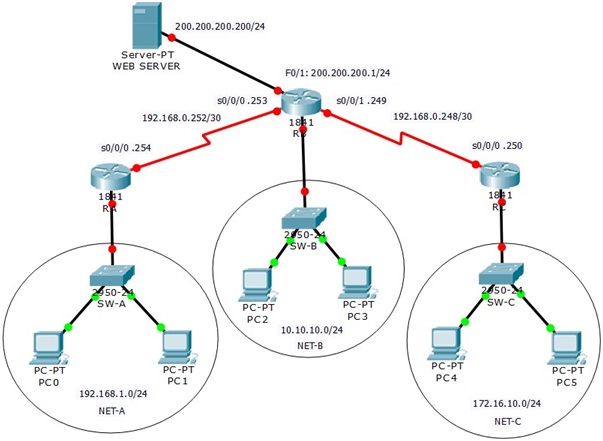
Task 1: Prepare the Network
Step 1: Create a network that is similar to the one in the topology diagram and paste a screenshot here.
Note: This lab was developed and tested using 1841 routers.
Task 2: Perform Basic Router Configurations
Configure the RA, RB, RC routers and switches according to the following guidelines: Step 1: Configure the router hostname to match the topology diagram.
Step 2: Configure IP addresses and masks on all devices.
Issue command: do show ip int brief on each router and paste the output here to show that you have configured the router names and all router interfaces.
Task 3: Perform Basic Routing Configurations
Enable OSPF area 0 with a process ID of 1 on all routers for all networks.
Step 1: Write down command to enable OSPF routing for each router
Step 2: Write down command to allow commands that allow OSPF routing to advertise the connected networks for each router
Step 2: Implement the OSPF commands on packet tracer and paste the routing table of each router here
Step 3: Verify the network connectivity by pinging PCs on different networks (paste screenshots here to show the network is connected)
Task 4: Configuring a Standard ACL
Standard ACLs can filter traffic based on source IP address only. A typical best practice is to configure a standard ACL as close to the destination as possible. In this task, you are configuring a standard ACL. The ACL is designed to block traffic from NET-A to access NET-B.
Answer the following questions and complete all required commands
Which router should we create the access-control list?
Step 1: Create the ACL on the router.
In global configuration mode, create a standard named ACL called A_TO_B_DENY.
R(config)#ip access-list standard A_TO_B_DENY
In standard ACL configuration mode, add a statement that denies any packets with a source address of NET-A and prints a message to the console for each matched packet.
R(config-std-nacl)#deny NET-A-IP WILD-CARD
Permit all other traffic.
R(config-std-nacl)#permit any
Step 2: Apply the ACL.
Which interface should we apply the ACL and for which direction?
Apply the ACL A_TO_B_DENY
R(config)#interface int_name
R(config-if)#ip access-group A_TO_B_DENY direction (IN/OUT)
R(config-if)#end R#copy run start
Step 3: Test the ACL.
Before testing the ACL, make sure that the console of the router is visible. This will allow you to see the access list log messages when the packet is denied.
Test the ACL by pinging any PC in NET-B from NET-A. Since the ACL is designed to block traffic with source addresses from NET-A network, the ping should fail.