Reference no: EM132987697
PART 1: Packet Tracer - Skills Integration Challenge
Topology
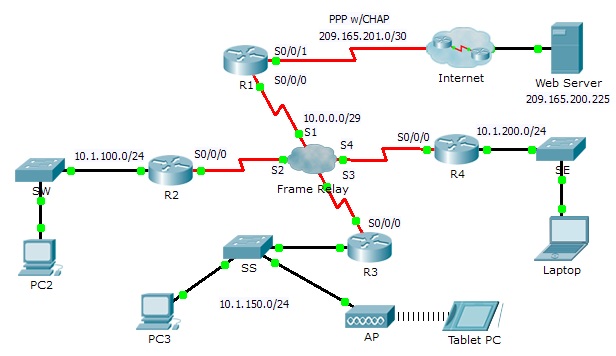
Background
This activity allows you to practice a variety of skills, including configuring Frame Relay, PPP with CHAP, EIGRP, static, and default routing.
Requirements
R1
• Configure R1 to use PPP with CHAP on the link to the Internet. ISP is the router hostname. The password for CHAP is cisco.
• Configure a default route to the Internet. Use the exit interface.
• Configure a static route to the LAN on R4. Use the next-hop IP address.
• Configure EIGRP.
- Use AS number 100.
- Advertise the entire 10.0.0.0/8 network and disable automatic summarization.
- Propagate the default route.
• Configure full mesh Frame Relay.
- Configure Frame Relay encapsulation.
- Configure a map to each of the other routers. The PVC to R4 uses IETF encapsulation.
- The LMI type is ANSI.
R2 and R3
• Configure EIGRP.
- Use AS number 100.
- Advertise the entire 10.0.0.0/8 network and disable automatic summarization.
- Do not send EIGRP messages out the LAN interfaces.
• Configure full mesh Frame Relay.
- Configure Frame Relay encapsulation.
- Configure a map to each of the other routers. The PVC to R4 uses IETF encapsulation.
- The LMI type is ANSI.
R4
• Configure static and default routing.
- Configure a static route for each of the LANs on R2 and R3. Use the next-hop IP address.
- Configure a default route to R1. Use the next-hop IP address.
• Configure full mesh Frame Relay.
- Configure Frame Relay encapsulation using IETF.
- Configure a map to each of the other routers.
- The LMI type is ANSI.
• Click Check Results to see what configurations you may still be missing. Implement necessary fixes and retest for full end-to-end connectivity. Complete the questions below and Part 2.
Troubleshooting and Explanations
1) Show screenshots of all configurations.
2) Show screenshots of all connections. All devices should be able to ping the web server and each other.
3) Show troubleshooting steps for EIGRP. Using screenshots, prove that EIGRP neighbors are communicating with each other properly.
4) Show troubleshooting steps for Frame-Relay. Using screenshots, validate Frame Relay encapsulation and DLCIs are working properly.
5) Explain each step.
6) What is the proper addressing and sub-netting and why?
7) Describe the benefits and EIGRP and Frame Relay.
8) How is EIGRP different than Frame-Relay?
PART 2: Now you try!
Instructions
1) Open a new / blank Packet Tracer window that does not have any devices
2) Add the same devices from Part 1 but use your first name and last name as a prefix. For example, if your name is "Amy Smith", router one will be named: "R1_Amy_Smith". Router 2 will be named "R2_Amy_Smith" and so on.
3) Design a new IP address table for all devices using any IP address in the 172.16.0.0/12 prefix range or 172.16.0.0 to 172.31.255.255. All addresses can be IPv4 for simplicity.
4) Design new public IP addresses using any address in the 100.100.0.0/16 prefix range.
5) Configure R1, R2, R3, and R4 the same as part 1 but use the new IP addresses you designed in Part 2.
6) Configure Frame Relay the same as part 1 but use the new IP addresses you designed in part 2.
7) Configure a router as the Internet. Use static public IP addresses using any address in the 100.100.0.0/16 prefix range.
8) Configure the PCs and Web Server from Part 1 with IPv4 addresses.
Troubleshooting and Explanations
1) Show screenshots of all configurations.
2) Show screenshots of all connections. All devices should be able to ping the web server and each other as appropriate from part 1 configurations.
3) Show troubleshooting steps for EIGRP and Frame Relay.
4) Justify how you know they are working with screenshots of each troubleshooting step. For example, how do you know EIGRP neighbors are connected properly? How do you know proper traffic is being sent by EIGRP and frame relay?
Attachment:- Infrastructure Internet Protocols Assignment.rar
|
What is the equilibrium price of gold futures
: What is the equilibrium price of gold futures on May 10th, 2021 for delivery in 273 days, February 7th, 2022?
|
|
Contract administration office as contract administrator
: Consider the five roles and responsibilities of the contract administration office as a contract administrator.
|
|
Is Ann Wood high-involvement manager
: Is Ann Wood a high-involvement manager? If so, provide evidence. If not, how well do you think she'll perform in her new job as head of marketing?
|
|
Identify any strategic groups that might exist in industry
: Identify any strategic groups that might exist in the industry. How does the intensity of competition differ across the strategic groups you have identified?
|
|
Packet tracer - skills integration challenge
: How you know they are working with screenshots of each troubleshooting step. For example, how do you know EIGRP neighbors are connected properly
|
|
Prepare the journal entries to record transactions
: Prepare the journal entries to record each of these five transactions. Assume that no cash discounts were taken on the collections of accounts receivable
|
|
Explain the history of your network traffic with wireshark
: Import the notepad file as a Hash Import to Forensic Software. Search for all occurrences of the hash. Does it search for the file or content of a file
|
|
Integrated set of components for collecting
: An Information System is integrated set of components for collecting, storing, and processing data and for delivering information, knowledge,
|
|
Change in way your colleagues are communicating
: Recently, you have noticed a change in the way your colleagues are communicating.
|