Reference no: EM133092119
Question 1.
The network below belongs to a small-sized pharmaceutical company researching vaccines. The methods and products developed in this company are at the target of state-sponsored hacker groups.
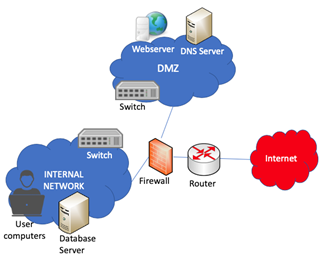
Although database server is the primary critical asset that stores intellectual property and webserver is used to access the data by authorized users from the Internet, the attack surface includes all of the assets you see in the figure.
Assets (Attack surface): Database server, user workstations, internal & DMZ switch, Webserver, DNS server, firewall, router, and company employees.
As a result, hackers have been trying all possible ways of exploiting vulnerabilities in these assets. Moreover, the activities of internal employees should also be observed, and it should be confirmed that they follow the need-to-know principle and don't perform malicious activities.
Select one of the following monitoring tools that also have strong network security monitoring capabilities. Please carefully review the website of the software you chose.
1. Nagios
2. Cacti
3. Solarwinds
Explain how this network monitoring tool helps security administrators in detecting the following cases. Feel free to provide the names of the modules/plugins/agents of the selected tool. Select at least three attack case for your answer.
1. Hackers are scanning externally visible IP addresses of the company.
2. Hackers are performing vulnerability scanning of the web applications hosted on the webserver.
3. Hackersare trying to poison the cache of the DNS server.
4. Internal threats are installing malicious tools on their computers.
5. Internal threats are trying to access/dump/backup database.
6. Internal threats are launching man-in-the-middle (Arp cache poisoning) attack.
7. Intenral threats are accessing external malicious websites.
Question 2.
You are the security administrator of this network; please draft a network operational procedure that lists the steps of discovering one of the three malicious behaviors you selected in the previous question. You can conduct research of existing procedures on the web.
|
Platform security architecture
: How does the Platform Security Architecture (PSA) build trust while reducing security costs and time-to-market?
|
|
Encouraging security architecture developments
: The Open Group has created an Enterprise Security Architect certification. The SANS Institute hosted three "What Works in Security Architecture" Summits.
|
|
Emerging threats and countermeasures
: We reviewed number of areas in information security and threats that companies face, we face, numerous threats and ways we can help to minimize these attacks
|
|
Baseline security requirements
: What are baseline security requirements that should be applied to the design and implementation of applications, databases, systems, network infrastructure,
|
|
Network monitoring tool
: Explain how this network monitoring tool helps security administrators in detecting the following cases. Hackersare trying to poison the cache of the DNS server
|
|
Business-episode of Sports Center
: During an episode of Sports Center, one of the anchors misread the teleprompter and said LeBron James was closing his school for at risk youth.
|
|
Examples of software and one state of art piece of equipment
: Choose three examples of software and one state-of-the-art piece of equipment that would benefit the lab.
|
|
Platform security architecture
: How does the Platform Security Architecture (PSA) build trust while reducing security costs and time-to-market?
|
|
Data analysis and data cleansing
: Data Analysis, Data Cleansing, exploratory analysis for native-country, race, education and work class of the dataset. machining learning model training
|