Reference no: EM131002948
Question 1. The instruction set architecture for a simple computer must support access to 64 KB of byte-addressable memory space and eight 16-bit general-purpose CPU registers.
a. If the computer has three-operand machine language instructions that operate on the contents of two different CPU registers to produce a result that is stored in a third register, how many bits are required in the instruction format for addressing registers?
b. If all instructions are to be 16 bits long, how many op codes are available for the three-operand, register operation instructions described above (neglecting, for the moment, any other types of instructions that might be required)?
c. Now assume (given the same 16-bit instruction size limitation) that, besides the instructions described in (a), there are a number of additional two-operand instructions to be implemented, for which one operand must be in a CPU register while the second operand may reside in a main memory location or a register. If possible, detail a scheme that allows for at least 50 register-only instructions of the type described in (a) plus at least 10 of these two-operand instructions. (Show how you would lay out the bit fields for each of the machine language instruction formats.) If this is not possible, explain in detail why not and describe what would have to be done to make it possible to implement the required number and types of machine language instructions.
Question 2. Multiplication of two 4-bit numbers (as shown in Figure 1) can be implemented as a Wallace tree multiplier (as shown in Figure 2) by using carry saver adders.
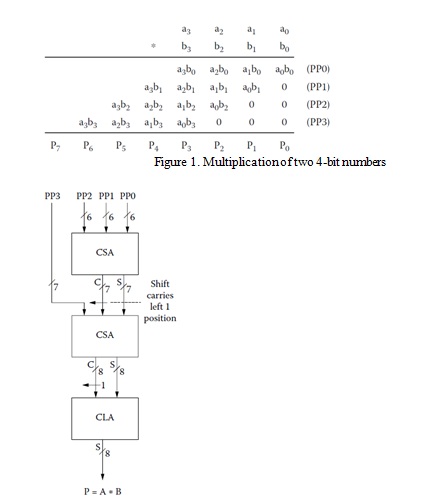
Figure. 2 The Wallace tree multiplier for 4-bit numbers
Show Figures 1 and 2 for the following multiplication of a 5-bit number and 4-bit number:
a4 a3 a2 a1 a0
b3 b2 b1 b0
--------------------------------------------------------------
Question 3: Conversion from decimal fraction to binary fraction is accomplished by multiplying the number by 2, using the integer part of the product as the next digit (and then discarding the integer). For example
.625 × 2 = 1.25 .1(the integer part of this product is 1)
.25 × 2 = 0.50 .10(the integer part of this product is 0)
.50 × 2 = 1.00 .101(the integer part of this product is 1)
So, 0.625 can be represented by .101 in binary (.101 = 1/2 + 0/4 + 1/8 = .625)
Show how the decimal value -27.5625 would be represented in IEEE 754 single (32 bits) and double (64 bits) precision formats. (Reminder: single precision exponents are expressed in excess-127 notation, and double precision exponents are expressed in excess-1023 notation)
|
Case study: assessment task 2
: Discuss the highest and best use principle and the relevance of the information provided by its application to the aged care home.
|
|
Unit: 401010 health variations 1
: Unit: 401010 Health Variations 1, Explain the pathogenesis of Crohn’s disease that has led to the development of Lucy’s obstruction of the proximal ascending colon.
|
|
Preliminary work for two industry research papers
: You are required to find two organisations: one large organisation with more than 5,000 employees and one small-to-medium organisation with between 50-1,000 employees.
|
|
Advanced financial accounting
: You are to research the issue of using graphical representation as a means of communicating financial information, and write an essay to critically evaluate the use of graphs in financial reports with reference to the Conceptual Framework for Financi..
|
|
Multiplication of two 4-bit numbers
: Multiplication of two 4-bit numbers (as shown in Figure 1) can be implemented as a Wallace tree multiplier (as shown in Figure 2) by using carry saver adders.
|
|
Determine which candidate would have won
: Determine which candidate would have won if all of the preference ballots had been reversed. Does this election illustrate a violation of the reversal criterion?
|
|
What is the magnitude of the force
: What is the magnitude of the force F→ on the 5.0 nC charge in the figure(Figure 1) ? What is the direction of the force F→ on the 5.0 nC charge in the figure? Give your answer as an angle measured cw from the +x-axis.
|
|
One-third of the stock of avis and best
: Matthew, Kelly, and Tammy each own one-third of the stock of Avis and Best.
|
|
What are the dimensions of the banner
: A small plane is flying a banner in the shape of rectagular. The area of the banner is 144 square feet. The width of the banner is 1/4 the length of the banner. What are the dimensions of the banner
|