Reference no: EM132842965
Learning Outcome 1: Have a knowledge and understanding of the issues involved in the design, realization /administration, and management of a networked computing environment.
Learning Outcome 2: Be able to design, install and support a local area network based on established user requirements.
Assignment task Description:
You are a newly employed graduate engineer working for an IT Network Support & Services Company. You have been are presented with the following challenge: A businesswoman wants you to design, install, test and support two secure computer networks for her primary and secondary business sites. The secondary business site is located 25 miles away from the main premises and she wants you to also prepare the network design and carry out the installation on a later date. The office buildings for the primary and secondary site were newly purchased and it will require fully functioning secure networks to run her business. The floor plans can be seen in the images below:
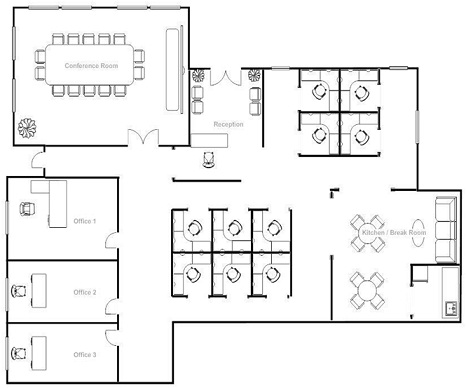
Figure 1: The floorplan of the primary business site
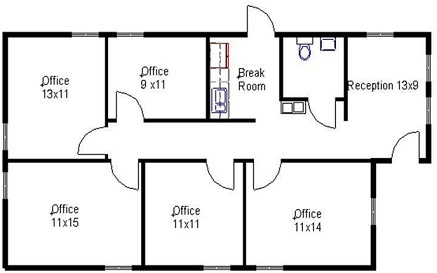
Figure 2: The floorplan of the secondary business site:
To proceed with the given assignment, your line manager wants you to carry out three main tasks.
Task 1: Network Designs
Your line manager wants you to provide detailed network designs for the primary and secondary business sites of the company using the provided office floor plans as a guide. The customer has provided the following specifications for the network.
Network Specifications: Primary business site
• Office 1 should be used as the Communication Room (comms room)
• There should be at least 15 workstations which must include one for the reception and conference room respectively.
• Three of the workstations should be running Linux OS i.e. Debian & Ubuntu LTS versions.
• In the comms room, there is a need for at least one hardware firewall to be connected to the border router and the main router should serve as the DHCP server.
• The network must have a DNS server, FTP server, and at least two 24-port switches.
• Most core network devices should be in the comms room. They will need racks. It is expected that most of the networking infrastructure should be stored in the same room unless in exceptional cases.
• The LAN must be 100% redundant in the case of a single point failure. Redundancy is critical. In the case that one of the circuits fails the other one must be up and able to warn for backup.
• There must be a Backup server and Print server.
• You are expected to choose your network devices sensibly i.e., a carrier-class router should not be used when you only need an enterprise-class router.
• You must consider scalability for future network expansion.
• Your network must have four VLANs which should be named Management, IT Support, Human Resources, and Sales Team.
• The workstations required for each VLAN are as follows: Management (3), IT support (3) Human Resources (3), and Sales Team (6).
• VLAN Routing must be enabled to ensure that workstations in the different departments can communicate with each other.
• Your network must have at least one Layer 3 switch, to ensure devices that are on the same subnet or virtual LAN connect at lightning speeds.
• The main server required for network administration must be Linux-based (i.e., Debian or Ubuntu OS).
• The main router must have an access control list enabled to block the following UDP & TCP ports: MS RPC (135), Syslog (514), IRC - TCP ports 6660-6669, and SNMP (161 -162).
• You must also provide a brief description of the network devices or software needed. For example, Server OS or VM technologies.
• There is a 10G SFP+ transceiver connection that will need to be connected to an ISP provider router. This connection comes to the comms room from the ISP's building.
Network Specifications: Secondary business site
• The secondary business site is a bit smaller than the main site with only five rooms.
• One of the rooms should be a comms room with at least one hardware firewall to be connected to the border router. This border router must be able to communicate with the border router of their main office premises via their respective ISPs or using a VPN.
• The comms room should have the main router which can serve as a DHCP server and at least one 24-port switch. Note: The main router serving as a DHCP server is not a compulsory requirement for this site. The workstations IP configuration can be configured manually if you want that option, however, testing must show that all devices can communicate with each other.
• The main router must have an access control list enabled to block the following ports: TFTP (69) & NETBIOS/IP 137 - 139.
• Most devices should be in the comms room and the LAN must also be 100% redundant.
• Each office and the reception area are equipped with 1 desktop PC and all PCs can connect to a Print Server.
• The PCs in the secondary site should be able to communicate with PCs on the main site.
Task 2: Network Implementation and Testing
Your line manager wants you to implement the network design on a virtual platform to test some of the required network services and functionalities before you can carry out the physical network installations. You are expected to implement and test the proposed network using an Open-Source network simulator or emulator such as Cisco packet tracer, GNS3, Boson NetSim, VIRL, VIRL, CORE, etc. A list of emulators and simulators can be found here: list of emulators & simulators.
Furthermore, you are expected to create comprehensive test and evaluation plans of the network designs and implemented services. This should be in tabular format.
Task 3: Required Network Administrative tasks
Your manager wants you to implement and execute the following administrative tasks on the networks implemented on the virtual platform. This is to ensure that the same tasks can be carried out when the physical network installation is carried out. You are also expected to carry out some further administrative tasks on the Linux server that is designative for administrative purposes only. To ensure you can perform the required administrative tasks, you are expected to first execute the tasks on a Linux server installed on a VMWare Player or VirtualBox.
The required administrative tasks for this section are as follows:
• The main router should be configured as the DHCP server as advised earlier and you must ensure that the IP addresses for the main router, DNS server, Linux Server, FTP server, Backup server, Print server are all excluded from the address pool.
• All workstations should be enabled to dynamically request IP from the DHCP server when they are switched on.
• Configure SSH on the main router and test these functionalities.
• Ensure all workstations can ping each other and other core network devices i.e., main router.
• All workstations must be able to connect to the internet.
• Create 15 network users and assign network administrative duties to two of the users. Note: this must be done on the Linux Server.
• Ensure that all users have an initial password which they will change when they first login in.
• Create two user groups (primary and secondary). The two network administrations should be in the primary group while the rest of the users should be placed in the secondary group.
• Aside from the network administrator accounts, create two other privileged accounts that give members the ability to run commands as root.
Attachment:- Network Systems Administration.rar