Reference no: EM133069448
L/615/1646 Network Security - Al Hussein Technical University
Assignment - A Secure Network with 2 Remote Offices
Cisco packet tracer and security workstation
Learning Outcome 1: Examine Network Security principles, protocols and standards.
Learning Outcome 2: Design a secure network for a corporate environment.
Learning Outcome 3: Configure Network Security measures for the corporate environment.
Learning Outcome 4: Undertake the testing of a network using a Test Plan.
Assignment Brief
Your employer, Secure Network Solution, LLC, asked you as their Lead Network Engineer to lead a project to build a new secure network to connect the client's headquarter to two remote offices, Remote 1 and Remote 2. All locations must belong to different network subnets. However, the devices on these networks may be separated using VLANs.
After evaluating the client's requirements, it has determined that the following should be achieved in the secure network
- Data servers in the headquarter network are accessible to employees at Remote 1 and Remote 2.
- Reports from Remote 1 and Remote 2 are securely sent to the headquarter office.
- All traffic should be scanned for security attacks.
- All employees should be able to securely exchange emails among each other.
- There is a site-to-site VPN connection between Remote 1 and Remote 2.
- The headquarter network is divided into five VLANs: Finance, HR, Engineering, Support, and Servers.
Part 1:
You will need to produce a report that includes the following:
1. Cover page, table of contents, and an introduction to provide an overview of your report.
2. A detailed discussion of different types of Network Security devices needed to implement a secure network.
3. An exploration of possible Network Security protocols and associated technologies that will enable a secure network for the client.
4. A detailed comparison of at least two major Network Security protocols.
5. An explanation of the importance of network security to the client.
6. A discussion of different cryptographic types of Network Security.
7. Review of what is meant by Quality of Service (QoS) in relation to Network Security configuration.
Part 2:
In this part you need to analyze the specification from the client below for completion of this project within a given timeframe:
Headquarter Office:
People: 10 administrative staff in each of HR and Finance, 20 employees in Engineering, and 10 in Support. There are 4 servers that are managed by 2 network and security admins. The servers include FTP, HTTP, Mail, and DNS
Building: all staff and machines are located on the same floor.
Remote Offices:
Remote 1: One manager, 5 administrative staff. Remote 2: One manager, 10 administrative staff. Resources: 17 computers in total.
Figure 1 shows the proposed design model and Table 1 Lists the suggested addressing scheme:
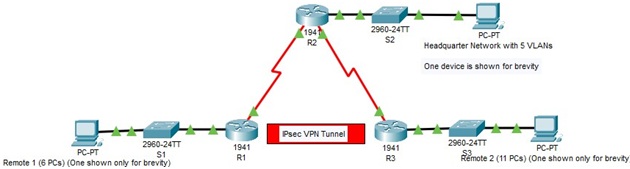
Figure 1: Proposed Design Model
The VLANS should be numbered as follows:
HR 5
Finance 10
Engineering 15
Support 20
Servers 50
Please include the following in your portfolio:
» A design plan for the secure network, blueprint and justification document.
» Network Security configuration (scripts/files/screenshots)
» A fully completed test plan including an evaluation of results and recommendations for improvements to security of the network.
» Evidence of an implemented network. [Soft copy of Packet Tracer simulation and screenshots should be provided].
|
|
|
|
Table 1: Suggested Addressing Scheme
|
|
|
|
|
Device
|
Interface
|
IP Address Subnet Mask Default Gateway
|
Switch Port
|
|
|
|
R1
|
G0/0
|
175.133.1.1 255.255.255.0 N/A
|
S1 F0/13
|
|
|
|
|
S0/0/0 (DCE)
|
10.1.1.2 255.255.255.252 N/A
|
N/A
|
|
|
|
R2
|
|
Depends on the
|
S2 F0/1
|
|
|
|
|
G0/0
|
sub-interface 255.255.255.0 N/A
|
|
|
|
|
|
S0/0/0
|
10.1.1.1 255.255.255.252 N/A
|
N/A
|
|
|
|
|
S0/0/1 (DCE)
|
10.2.2.1 255.255.255.252 N/A
|
N/A
|
|
|
|
R3
|
G0/0
|
155.154.3.1 255.255.255.0 N/A
|
S3 F0/13
|
|
|
|
|
S0/0/1
|
10.2.2.2 255.255.255.252 N/A
|
N/A
|
|
|
|
|
|
Remote 1
|
|
|
|
|
Device
|
Interface
|
IP Address Subnet Mask Default Gateway
|
Switch Port
|
|
|
|
PC-1
|
NIC
|
175.133.1.11 255.255.255.0 175.133.1.1
|
S1 F0/1
|
|
|
|
PC-2
|
NIC
|
175.133.1.12 255.255.255.0 175.133.1.1
|
S1 F0/2
|
|
|
|
PC-3
|
NIC
|
175.133.1.13 255.255.255.0 175.133.1.1
|
S1 F0/3
|
|
|
|
PC-4
|
NIC
|
175.133.1.14 255.255.255.0 175.133.1.1
|
S1 F0/4
|
|
|
|
PC-5
|
NIC
|
175.133.1.15 255.255.255.0 175.133.1.1
|
S1 F0/5
|
|
|
|
PC-6
|
NIC
|
175.133.1.16 255.255.255.0 175.133.1.1
|
S1 F0/6
|
|
|
|
|
|
Remote 2
|
|
|
|
|
Device
|
Interface
|
IP Address
|
Subnet Mask
|
Default Gateway
|
Switch Port
|
|
|
PC-1
|
NIC
|
155.154.3.11
|
255.255.255.0
|
155.154.3.1
|
S3 F0/1
|
|
PC-2
|
NIC
|
155.154.3.12
|
255.255.255.0
|
155.154.3.1
|
S3 F0/2
|
|
PC-3
|
NIC
|
155.154.3.13
|
255.255.255.0
|
155.154.3.1
|
S3 F0/3
|
|
PC-4
|
NIC
|
155.154.3.14
|
255.255.255.0
|
155.154.3.1
|
S3 F0/4
|
|
PC-5
|
NIC
|
155.154.3.15
|
255.255.255.0
|
155.154.3.1
|
S3 F0/5
|
|
PC-6
|
NIC
|
155.154.3.16
|
255.255.255.0
|
155.154.3.1
|
S3 F0/6
|
|
PC-7
|
NIC
|
155.154.3.17
|
255.255.255.0
|
155.154.3.1
|
S3 F0/7
|
|
PC-8
|
NIC
|
155.154.3.18
|
255.255.255.0
|
155.154.3.1
|
S3 F0/8
|
|
PC-9
|
NIC
|
155.154.3.19
|
255.255.255.0
|
155.154.3.1
|
S3 F0/9
|
|
PC-10
|
NIC
|
155.154.3.20
|
255.255.255.0
|
155.154.3.1
|
S3 F0/10
|
|
PC-11
|
NIC
|
155.154.3.21
|
255.255.255.0
|
155.154.3.1
|
S3 F0/11
|
Headquarter
You will need more than one switch with multiple VLANs. The assignment of the IP addresses for the PCs is left to you to choose as you see fit based on the VLAN network addresses.
|
VLAN#
|
Name
|
VLAN Subnet IP
|
|
5
|
HR
|
182.168.5.0/27
|
|
10
|
Finance
|
182.168.10.0/27
|
|
15
|
Engineering
|
182.168.15.0/27
|
|
20
|
Support
|
182.168.20.0/27
|
|
50
|
Servers
|
182.168.50.0/27
|
|
99
|
Native
|
182.168.99.0/27
|
The servers, however, should be assigned the following IP addresses.
|
Device
|
Interface
|
IP Address
|
|
FTP
|
NIC
|
182.168.50.2
|
|
HTTP
|
NIC
|
182.168.50.2
|
|
DNS
|
NIC
|
182.168.50.3
|
|
Mail
|
NIC
|
182.168.50.3
|
Design and configure a secure network for the headquarter and remote offices:
1. Investigate the purpose and requirements of the secure network according to the given scenario.
2. Determine which network hardware and software to use in the network. Justify your choices.
3. Design and implement a secure network prototype according to the given scenario using Packet Tracer simulator.
4. Configure Network Security measures for your network. Those measures include Firewalls, Routers, Switches, Gateways, passwords, SSH, SSL, IPSec, VPN, HTTPs, FTPs, DHCP and DNS.
5. Provide Network Security configuration scripts/files/screenshots with comments.
Undertake the testing of a network security using a Test Plan
1. Create a test plan for your network. Your test plan should consider different testing methods in terms of checks on network security, testing for network vulnerabilities etc.
2. Comprehensively test your network using the devised test plan. Tests should be carried out on all devices (Firewall, Servers, Routers, Switches, gateways, passwords). Record the test results and analyze these against expected results. You need to provide scripts/files/screenshots of the testing of your network.
3. Critically evaluate the design, planning, configuration and testing of your network security. Make some improvement recommendations.
Attachment:- Network Security.rar