Reference no: EM132884961 , Length: word count:2400
ITNE2005R Network Security Implementation - Victorian Institute of Technology
Learning Outcome 1: Analyse and configure routers on the network perimeter with router software security features
Learning Outcome 2: Evaluate and configure firewall protocols and features to perform basic security operations on a network
Learning Outcome 3: Critically review the enterprise network requirements and configure site-to-site Virtual Private Networks using standard router software features
Learning Outcome 4: Analyse the enterprise security requirements and configure intrusion prevention systems on network routers.
Learning Outcome 5: Monitor network traffic and implement security policies to control access, resist attacks, and protect network devices
Objectives
This assessment item relates to the unit learning outcomes as in the unit descriptors. The purpose of this assignment is to enable students to work in teams and expand their thinking through reading and sharing ideas.
Case Study
In 2018, FunTech (PRIVATE) Limited is recorded as a the top 10 fastest growing company with 800% EPS growth in a year. Recently, the company has added 50 part time and 100 full time employees. The company has expanded 3 new branches in different cities. The network expansion is almost completed, and all the offices are connected with each other via WAN (Internet). Data's from all the offices are stored and executed from the main data centre which is located in the head office. This data centre even holds highly confidential and sensitive data. The CTO of the company is worried since there are only few security devices installed in the network and there is a high risk of the network getting compromised.
Based on the report presented by IT department, some abnormal traffic pattern was monitored in company's network both from inside and outside the network. Initial investigation shows that 1) some of the company's hardware has some major loopholes (not secured) which was not expected 2) the head office network is being constantly receiving a ransomware message 3) strange network traffic patterns can be seen. It's also observed that the capacity of mail server is 30 mails per second, but the server is sometimes receiving more than 100 mails in a second which is not normal. IT department is highly suspicious about this abnormal traffic and to clarify what is going on, the company is hiring a third-party security company to conduct a risk assessment. Implementing an IT security risk assessment is highly recommended and can prevent security breaches and its impacts.
* 1 main office (Melbourne)
*5 regional office across Australia
The small segment of network design of FunTech (private) Limited is provided. Based on the network diagram, complete the following task.
(You are free to make necessary assumption if required)
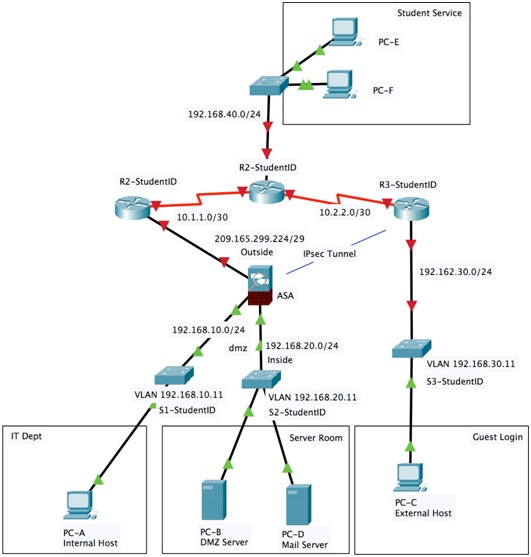
Part A
Task 1: Fill the addressing table before you start your configuration
|
Device
|
Interface
|
IP Address
|
Subnet Mask
|
Default Gateway
|
Switch Port
|
|
R1-
StudentID
|
|
|
|
N/A
|
|
|
|
|
|
N/A
|
N/A
|
|
Loopback 1
|
172.20.1.1
|
255.255.255.0
|
N/A
|
N/A
|
|
R2--
StudentID
|
|
|
|
N/A
|
N/A
|
|
|
|
|
N/A
|
N/A
|
|
R3--
StudentID
|
|
|
|
N/A
|
|
|
|
|
|
|
N/A
|
N/A
|
|
S1--
StudentID
|
VLAN 1
|
|
|
|
N/A
|
|
S2--
StudentID
|
VLAN 1
|
|
|
|
N/A
|
|
S3--
StudentID
|
VLAN 1
|
|
|
|
N/A
|
|
ASA
|
VLAN 1 (Et0/2)
|
|
|
N/A
|
|
|
VLAN 2 (Et0/0)
|
|
|
N/A
|
|
|
VLAN 3 (Et0/1)
|
|
|
N/A
|
|
|
PC-A
|
NIC
|
|
|
|
|
|
PC-B
|
NIC
|
|
|
|
|
|
PC-C
|
NIC
|
|
|
|
|
|
PC-D
|
NIC
|
|
|
|
|
|
PC-E
|
NIC
|
|
|
|
|
|
PC-F
|
NIC
|
|
|
|
|
Task 2: Configure Basic Device Settings
• Configure host names as shown in the topology plus your student ID.
• Configure interface IP addresses as achieved from IP Addressing Table.
• Configure static and dynamic routing
• Verify connectivity among devices before another configuration.
Task 3: Configure Secure Router Administrative Access
• Configure encrypted passwords and a login banner.
• Configure the EXEC timeout value on console and VTY lines.
• Configure login failure rates and VTY login enhancements.
• Configure Secure Shell (SSH) access and disable Telnet.
• Configure local authentication, authorization, and accounting (AAA) user authentication.
• Secure the router against login attacks and secure the IOS image and the configuration file.
• Configure a router NTP server and router NTP clients.
• Configure router syslog reporting and a syslog server on a local host.
Task 4: Configure a Zone-Based Policy Firewall and Intrusion Prevention System
• Configure a Zone-Based Policy Firewall (ZPF) on an R3 using the CLI.
• Configure an intrusion prevention system (IPS) on an R3 using the CLI.
Task 5: Configure ASA Basic Settings and Firewall
• Configure basic settings, passwords, date, and time.
• Configure the inside and outside VLAN interfaces.
• Configure port address translation (PAT) for the inside network.
• Configure a Dynamic Host Configuration Protocol (DHCP) server for the inside network.
• Configure administrative access via Telnet and SSH.
• Configure a static default route for the Adaptive Security Appliance (ASA).
• Configure Local AAA user authentication.
• Configure a DMZ with a static NAT and ACL.
• Verify address translation and firewall functionality.
Task 6: Configure a Site-to-Site VPN between the ASA and R3
• Configure an IPsec site-to-site VPN between the ASA and R3-S0000 using ASDM and the CLI.
• Activate and verify the IPsec site-to-site VPN tunnel between the ASA and R3.
Part B
Conclude your report
Analyse the project security before and after the implementation of provided configuration.
Write an executive summary on the output of this project of the provided project
Attachment:- Network Security Implementation.rar