Reference no: EM132689368
ITNE2005 Develop a security Infrastructure for a Medium-Size Network - Victoria Institute of Technology
Objectives
This assessment item relates to the unit learning outcomes as in the unit descriptor. This assessment is designed to evaluate student's ability on working with the routers, firewalls and VPN tunnels and adopting those technologies in enterprise level networks.
Learning outcome 1 Explain network security issues and develop a comprehensive network security policy to counter threats against information security
Learning outcome 2 Analyse and configure routers on the network perimeter with router software security features
Learning outcome 3 Evaluate and configure firewall protocols and features to perform basic security operations on a network
Learning outcome 4 Critically review the enterprise network requirements and configure site-to-site virtual private networks using standard router software features
Learning outcome 5 Analyse the enterprise security requirements and configure intrusion prevention systems on network routers
Learning outcome 6 Monitor network traffic and implement security policies to control access, resist attacks, and protect network devices
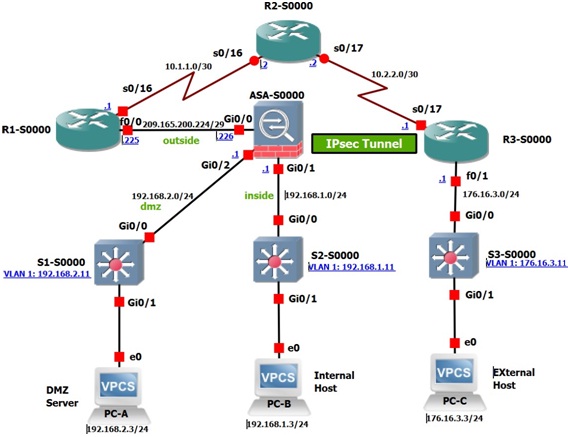
Figure 1: Network Topology
Note: Integrated Services Routers (ISR) have Fast Ethernet interfaces instead of Gigabit Ethernet interfaces.
Addressing Table
|
Device
|
Interface
|
IP Address
|
Subnet Mask
|
Default Gateway
|
Switch Port
|
|
R1-S0000
|
F0/0
|
209.165.200.225
|
255.255.255.248
|
N/A
|
ASA G0/0
|
|
S0/0 (DCE)
|
10.1.1.1
|
255.255.255.252
|
N/A
|
N/A
|
|
Loopback 1
|
172.20.1.1
|
255.255.255.0
|
N/A
|
N/A
|
|
R2-S0000
|
S0/0
|
10.1.1.2
|
255.255.255.252
|
N/A
|
N/A
|
|
S0/1 (DCE)
|
10.2.2.2
|
255.255.255.252
|
N/A
|
N/A
|
|
R3-S0000
|
F0/1
|
172.16.3.1
|
255.255.255.0
|
N/A
|
S3 G0/0
|
|
S0/0
|
10.2.2.1
|
255.255.255.252
|
N/A
|
N/A
|
|
S1-S0000
|
VLAN 1
|
192.168.2.11
|
255.255.255.0
|
192.168.2.1
|
N/A
|
|
S2-S0000
|
VLAN 1
|
192.168.1.11
|
255.255.255.0
|
192.168.1.1
|
N/A
|
|
S3-S0000
|
VLAN 1
|
172.16.3.11
|
255.255.255.0
|
172.16.3.1
|
N/A
|
|
ASA
|
VLAN 1 (G0/1)
|
192.168.1.1
|
255.255.255.0
|
N/A
|
S2 G0/0
|
|
VLAN 2 (G0/0)
|
209.165.200.226
|
255.255.255.248
|
N/A
|
R1 F0/0
|
|
VLAN 2 (G0/2)
|
192.168.2.1
|
255.255.255.0
|
N/A
|
S1 G0/0
|
|
PC-A
|
NIC
|
192.168.2.3
|
255.255.255.0
|
192.168.2.1
|
S1 G0/1
|
|
PC-B
|
NIC
|
192.168.1.3
|
255.255.255.0
|
192.168.1.1
|
S2 G0/1
|
|
PC-C
|
NIC
|
172.16.3.3
|
255.255.255.0
|
172.16.3.1
|
S3 G0/1
|
In this lab, you will perform the following tasks:In this Assignment you are required to complete all the following parts:
Task 1: Configure Basic Device Settings:
• Configure host names as shown in the topology plus your student ID.
• Configure interface IP addresses as shown in the IP Addressing Table.
• Configure static and dynamic routing
Task 2: Configure Secure Router Administrative Access
• Configure encrypted passwords and a login banner.
• Configure the EXEC timeout value on console and VTY lines.
• Configure login failure rates and VTY login enhancements.
• Configure Secure Shell (SSH) access and disable Telnet.
• Configure local authentication, authorization, and accounting (AAA) user authentication.
• Secure the router against login attacks and secure the IOS image and the configuration file.
• Configure a router NTP server and router NTP clients.
• Configure router syslog reporting and a syslog server on a local host.
Task 3: Configure a Zone-Based Policy Firewall and Intrusion Prevention System
• Configure a Zone-Based Policy Firewall (ZPF) on an R3 using the CLI.
• Configure an intrusion prevention system (IPS) on an R3 using the CLI.
Task 4: Secure Network Switches
• Configure passwords and a login banner.
• Configure management VLAN access.
• Secure access ports.
• Protect against Spanning Tree Protocol (STP) attacks.
• Configure port security and disable unused ports.
Task 5: Configure ASA Basic Settings and Firewall
• Configure basic settings, passwords, date, and time.
• Configure the inside and outside VLAN interfaces.
• Configure port address translation (PAT) for the inside network.
• Configure a Dynamic Host Configuration Protocol (DHCP) server for the inside network.
• Configure administrative access via Telnet and SSH.
• Configure a static default route for the Adaptive Security Appliance (ASA).
• Configure Local AAA user authentication.
• Configure a DMZ with a static NAT and ACL.
• Verify address translation and firewall functionality.
Task 6: Configure a DMZ, Static NAT, and ACLs on an ASA
• Configure static NAT to the DMZ server using a network object.
• View the DMZ Access Rule (ACL) generated by ASDM.
• Test access to the DMZ server from the outside network.
Task 7: Configure ASA Clientless SSL VPN Remote Access Using ASDM
• Configure a remote access SSL VPN using the Cisco Adaptive Security Device Manager (ASDM).
• Verify SSL VPN access to the portal.
Task 8: Configure a Site-to-Site VPN between the ASA and R3
• Configure an IPsec site-to-site VPN between the ASA and R3-S0000 using ASDM and the CLI.
• Activate and verify the IPsec site-to-site VPN tunnel between the ASA and R3.
Upon Completion of the above configuration tasks, you have been asked to draft a Policy on using of VPN by telecommuters. The policy should include the following sections:
1. Objectives 3. Audience 5. Exceptions
2. Purpose 4. Policy 6. Violations
Attachment:- Develop a security Infrastructure.rar