Reference no: EM132601463
ITC542 Internetworking with TCP/IP - Charles Sturt University
Assessment item - Networking Fundamentals
Learning Outcome 1: be able to analyse IP addressing requirements and design an addressing scheme.
Learning Outcome 2: be able to analyse the requirements of IP routing and choose appropriate routing methods.
Learning Outcome 3: be able to demonstrate how internetworking devices obtain their network configuration.
Learning Outcome 4: be able to explain how data flows through the internet.
Learning Outcome 5: be able to ascertain and evaluate selection of applications and protocols for transferring data across the internet.
Question 1
Complete the Hands-On Projects 3-1 and 3-2 from the prescribed textbook (pg. 144-145). The files required to complete these projects are available from the "resources" folder in the subject site. In order to complete these activities, students should insert screenshots in the assignment document along with a brief informative description of each step taken to complete the project. Marks will be deducted if the description is not provided.
Question 2
Watch the following two videos and write a reflective piece based on your observations and insights on the workings of both Link State and Distance Vector Routing, highlighting the major differences. In addition to the videos, students are encouraged to consult authentic additional resources such as text book, research articles etc. to enhance understanding of the topics.
Question 3 Case study task
Let us consider three hosts connected together in a local network having private IP addresses 10.0.1.14, 10.0.1.15 and 10.0.1.20. Between this local network of three hosts and the rest of the internet is a NAT enabled switch/router as shown in Figure1 below. All information in the form of IP datagrams being sent from or incoming towards these hosts must pass through this device.
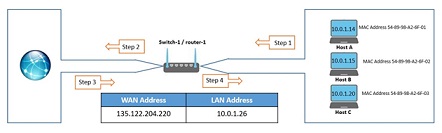
Figure 1: Network Diagram
Task 1
Figure 1 above shows a switched network, with Host A, B and C connected to ports Fa0/1, Fa0/2 and Fa0/3 respectively; the current MAC address table of Switch-1 is empty as below:
a) Discuss what would happen next if Switch-1 received a frame from Host-A with the destination MAC address of host-B?
b) Discuss what would happen next if Switch-1 received a frame from Host-B with the destination MAC address of host-A?
In both cases, illustrate the changes in the MAC address table in your answer.
Task 2
Let us assume that the host with IP address 10.0.1.20 sends an IP data-gram destined to host 128.119.165.183. The source port is randomly selected as 3428, and the destination port as 80.
What are the source and destination addresses of the IP datagram as well as the source and destination port numbers for the TCP segment in the datagram at:
a) step one (i.e. after it has been sent from the host but before it reaches the router).
b) step two? (i.e. after it has been transmitted from the router).
c) step three (just before it is received by the router)
d) step four (after it has been transmitted by the router but before it is received by the host).
Attachment:- Internetworking assignment.rar