Reference no: EM131100380
E27: Computer Vision - Spring 2016 - HOMEWORK 12
Backpropagation in a simple network
The binary XOR function is given by the following truth table:
|
y1
|
y2
|
y1 ⊗ y2
|
|
-1
|
-1
|
-1
|
|
-1
|
1
|
1
|
|
1
|
-1
|
1
|
|
1
|
1
|
-1
|
It can be computed by a simple two-layer network with the following structure:
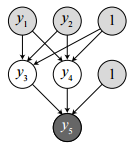
Note that both the input and hidden layer of the network have bias nodes. The output is computed by
y3 = f(x3) = f(w03 + w13 y1 + w23 y2)
y4 = f(x4) = f(w04 + w14 y1 + w24 y2)
y5 = f(x5) = f(w05 + w35 y3 + w45 y4)
where wij is the weight from node i to node j and w0j is the weight from a bias node.
Download the xor_nnet.py file from the course webpage and complete the steps marked # TODO to implement the back-propagation algorithm described in the class handout for this simple network. If you keep the α parameter and tolerance specified in the file, your implementation should converge in 61 iterations.
Attachment:- xor_nnet.py.rar
|
Evaluate any limitations that the item may have
: Evaluate any limitations that the item may have (i.e. timeliness, small sample size, bias, etc.), identify what audience the item is intended for and discuss any conclusions the author(s) may have made, especially in relation to other studies.
|
|
Function for the new state income tax
: The state income tax in Connecticut is modeled by the function below, where x is income in dollars. Suppose that Connecticut decided to increase its tax rates by 20% and add a filing fee of $100. Write a function for the new state income tax.
|
|
Topic of social constructionism theory
: Specific aspect of the problem to focus on. In class you will create your thesis statement to use when doing your research and writing your paper - You must tie your paper into the theoretical base and ensure your topic fits in with those of your p..
|
|
New product into a very competitive market
: A company will soon be introducing a new product into a very competitive market and is currently planning its marketing strategy. The decision has been made to introduce the product in three phases.
|
|
Implement the back-propagation algorithm
: Download the xor_nnet.py file from the course webpage and complete the steps marked # TODO to implement the back-propagation algorithm described in the class handout for this simple network
|
|
Percent of error in measurement of the defective scale
: Skeeter, the dog, weighs exactly 36.5 pounds. When weighed on a defective scale, he weighed 38 pounds. (a) What is the percent of error in measurement of the defective scale to the nearest tenth?
|
|
Create your justifications additional exciting remember to
: Create your justifications additional exciting remember to. A number of avid gamers tried out guarding your adjust, declaring who's has not been censorship. Nearly all predetermined who's ended up being censorship.
|
|
A county chairwoman of a certain political party
: A county chairwoman of a certain political party is making plans for an upcoming presidential election. She has received the services of six volunteer workers for precinct work, and she wants to assign them to four precincts in such a way as to ma..
|
|
Employee of a certain company
: Each employee of a certain company is in either Department X or Department Y, and there are more than twice as many employees in Department X as in Department Y.
|