Reference no: EM131428319
Question 1
(a) Routing Information Protocol (RIP) uses User Datagram Protocol (UDP) in the transport layer and it is considered as a connectionless and unreliable protocol. In this situation, how does RIP ensure the reliability and consistency of the routing updates between routers?
(b)
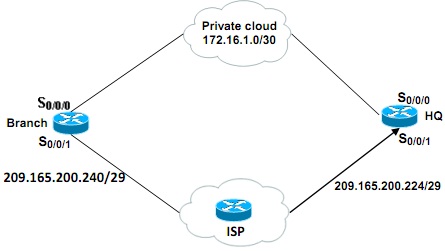
Figure 1(b)
The HQ and the Branch of ABC Corporation are connected through a private WAN (cloud) using leased line as well as via the Internet for backup as shown in Figure 1(b).
i. Identify the type of routing used between the routers and the Branch that facilitates high availability and also prevents layer-3 looping.
ii. Justify your proposed solution and explain its working principle.
iii. Explain the disadvantage of your proposed solution if any.
Question 2
(a) You have been assigned to manage an enterprise network and you found that the network performance is poor due to the faulty switch (Cisco) in the switching rack and it is replaced with new one (Juniper) as shown in Figure - 2(a). The existing switches were configured with Inter Switch Protocol.
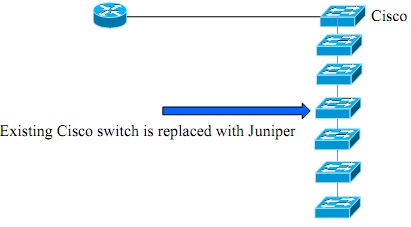
Figure 2(a)
There are six VLANs in this switching rack and all VLANs should be able to communicate with each other.
i. Propose an appropriate solution to establish the full connectivity of the network.
ii. Discuss a solution to resolve the problems you identified in part i., explaining fully your solution.
(b)
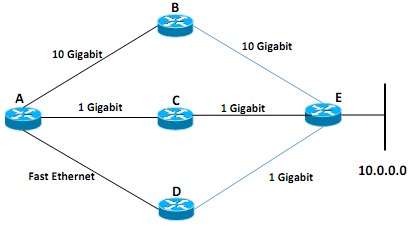
Figure 2(b)
All routers shown in Figure 2(b) are enabled with Open Shortest Path First (OSPF) with default settings. Router-A learns the network 10.0.0.0 via routers B, C and D.
i. Analyze and explain the operational problems involved in building a topology table to establish a route from router-A to the network 10.0.0.0.
ii. Propose your solution to solve the problems and explain the result of your proposed solution.
(c) As a network administrator, evaluate the situations in which you would choose to use the distance vector routing protocols.
SECTION B
Answer ANY TWO (2) of the THREE (3) questions in this section. All questions carry equal marks.
Question 3
(a) Your organization has decided to upgrade the network and also implement a link-state routing protocol and you are assigned to carry out this task. As a network administrator, evaluate the requirements of routing devices that are important to implement the link state protocol.
(b) Using the Bellman Ford algorithm, construct the routing table for router B in Figure 3(b)".
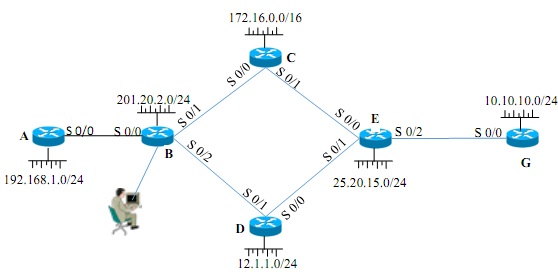
Figure 3(b) Use Table-3(b) to create the routing table.
Network Exit interface Next Hop Address Hop Count Administrative Distance
Table-3(b)
|
Network
|
Exit interface
|
Next Hop Address
|
Hop Count
|
Administrative Distance
|
(c)
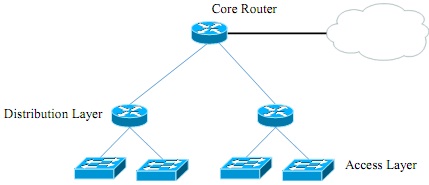
Figure - 3(c)
A default static route is configured on the core router that provides access to the Internet. Within the organization, Open Shortest Path First (OSPF) is used for routing with private IP addressing. Choose and explain an appropriate routing technique that provides the complete Internet connectivity.
(d)
SW1#show interfaces fastEthernet 0/1 switchport
Switchport: Enabled
Administrative Mode: trunk Operational Mode: trunk
Operational Trunking Encapsulation: dot1q Negotiation of Trunking: On
Access Mode VLAN: 99
Trunking Native Mode VLAN: 1 (default)
Trunking VLANs Enabled: ALL Pruning VLANs Enabled: 2-1001 Capture Mode Disabled
Capture VLANs Allowed: all Protected: false
Appliance trust: none
SW2#show interfaces fastEthernet 0/1 switchport
Switchport: Enabled
Administrative Mode: access Operational Mode: trunk
Operational Trunking Encapsulation: dot1q Negotiation of Trunking: On
Access Mode VLAN: 1 (default) Trunking Native Mode VLAN: 1 (default) Trunking VLANs Enabled: ALL
Pruning VLANs Enabled: 2-1001 Capture Mode Disabled
Capture VLANs Allowed: all Protected: false
Appliance trust: none
Figure- 3(d)
Figure - 3(d) shows the partial output of trunk link configuration between layer-2 switches SW1 and SW2. However, a trunk is still not established across the configured link. Identify any TWO (2) problems in the above configurations and provide solution(s).
Question 4
(a)
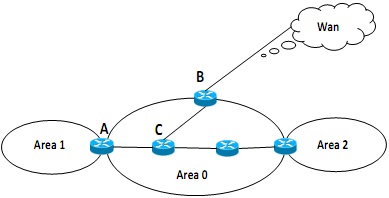
Figure - 5(a)
Identify the type of routers A, B and C shown in Figure - 4(a) and explain their roles in routing.
(b)
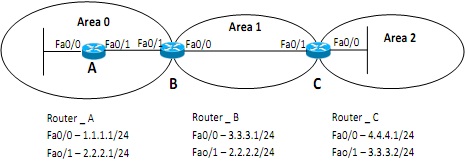
Figure - 5(b)
When designing OSPF networks, all areas should be connected to the backbone area. However, due to topography constraint in ABC Corporation, it is possible to connect the area-2 with the area-1. You are assigned to solve this problem.
i. Propose a solution to establish the connectivity for the area-2.
ii. With the aid of diagram, explain your proposed solution.
iii. Provide the configuration of your proposed solution
(c)
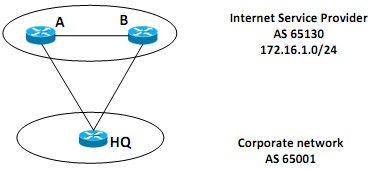
Figure - 4 (c)
An online trading company has dual connections to local ISP for 24/7 connectivity. A main link between HQ and A is 1.544 Mbps and a backup link between HQ and B is 512 Kbps. You are assigned to provide the routing as per the user's requirements. Assess this situation and provide a routing solution with justification.
Question 5
(a)
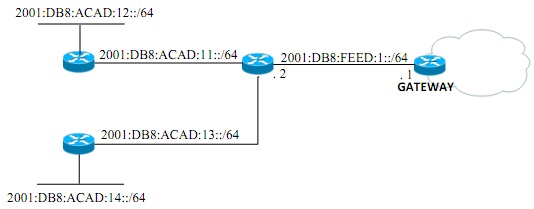
Figure - 5(a)
You have been assigned to configure the Gateway router to establish the connectivity to all the subnets as shown in Figure 5(a).
i. Propose the most efficient and economical solution that does not gives router overhead.
ii. Explain your proposed solution.
(b) By default, OSPF routers exchange Link State Advertisements (LSAs) by flooding them to all OSPF neighbors and this action affects the performance of the Broadcast and Non- Broadcast Multiple Access topology shown in Figure 5(b). Explain how OSPF addresses this LSA flooding problem to enhance network performance.
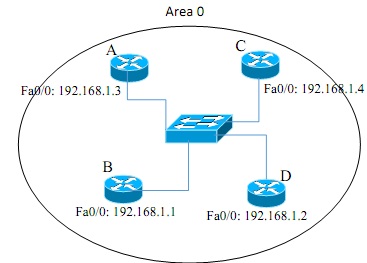
Figure - 5(b)
(c) A Teredo client has the address 2001::62C3:1B8D:346B:EBC9:7C94:EA26. With reference to this IPv6 address, answer the following questions.
i. What is the external IPv4 address?
ii. What is the UDP port number for this Teredo client's traffic?