Reference no: EM13852525
Assignment 1: Identifying Potential Malicious Attacks, Threats and Vulnerabilities
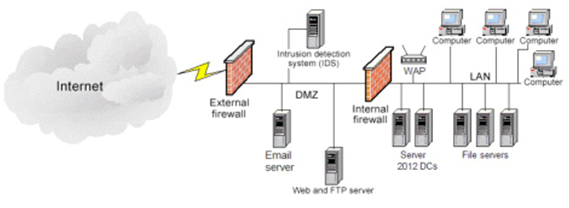
You have just been hired as an Information Security Engineer for a videogame development company. The organization network structure is identified in the below network diagram and specifically contains:
1) 2 - Firewalls
2) 1 - Web / FTP server
3) 1 - Microsoft Exchange Email server
4) 1 - Network Intrusion Detection System (NIDS)
5) 2 - Windows Server 2012 Active Directory Domain Controllers (DC)
6) 3 - File servers
7) 1 - Wireless access point (WAP)
8) 100 - Desktop / Laptop computers
9) VoIP telephone system
The CIO has seen reports of malicious activity being on the rise and has become extremely concerned with the protection of the intellectual property and highly sensitive data maintained by your organization. As one of your first tasks with the organization, the CIO requested you identify and draft a report identifying potential malicious attacks, threats, and vulnerabilities specific to your organization. Further, the CIO would like you to briefly explain each item and the potential impact it could have on the organization.
Write a four to five (4-5) page paper in which you:
1. Analyze three (3) specific potential malicious attacks and / or threats that could be carried out against the network and organization.
2. Explain in detail the potential impact of the three (3) selected malicious attacks.
3. Propose the security controls that you would consider implementing in order to protect against the selected potential malicious
attacks.
4. Analyze three (3) potential concerns for data loss and data theft that may exist in the documented network.
5. Explicate the potential impact of the three (3) selected concerns for data loss and data theft.
6. Propose the security controls that you would consider implementing in order to protect against the selected concerns for data loss and data theft.
7. Use at least three (3) quality resources in this assignment (no more than 2-3 years old) from material outside the textbook. Note: Wikipedia and similar Websites do not qualify as quality resources.
Your assignment must follow these formatting requirements:
• Be typed, double spaced, using Times New Roman font (size 12), with one-inch margins on all sides; citations and references must
follow APA or school-specific format. Check with your professor for any additional instructions.
• Include a cover page containing the title of the assignment, the student's name, the professor's name, the course title, and the date.
The cover page and the reference page are not included in the required assignment page length.
The specific course learning outcomes associated with this assignment are:
• Explain the concepts of information systems security as applied to an IT infrastructure.
• Describe the principles of risk management, common response techniques, and issues related to recovery of IT systems.
• Describe how malicious attacks, threats, and vulnerabilities impact an IT infrastructure.
• Explain the means attackers use to compromise systems and networks, and defenses used by organizations.
• Use technology and information resources to research issues in information systems security.
• Write clearly and concisely about network security topics using proper writing mechanics and technical style conventions.
Grading for this assignment will be based on answer quality, logic / organization of the paper, and language and writing skills
|
Find the pure strategy nash equilibrium
: Firms A and B are the only firms in the market for widgets. Each firm can choose between cooperating and fighting. If both firms choose to cooperate, each gets a profit of 10. If both firms choose to fight, each gets a profit of 5. Suppose firms choo..
|
|
Two firms face the abatement costs
: Assume that two power plants, Firm 1 and Firm 2, release arsenic in a small urban community that exceeds the emissions standard. To meet the standard, 40 units of SO2 must be abated in total. The two firms face the following abatement costs: Determin..
|
|
What is the bertrand-nash equilibrium
: The inverse demand curve for sugar is P = 100−Q. There are two firms, C and D, who produce sugar. Firms produce sugar using a technology with a cost function characterized by C(Qi) = 20Qi where Qi is the quantity produced by each firm. What is the Be..
|
|
The inverse demand curve for widgets
: The inverse demand curve for widgets is P = 130−2Q. There are two firms, A and B, who produce wid-gets. Each firm has a constant marginal and average cost of producing the good that equals 10. What is the Cournot-Nash equilibrium? You need to solve t..
|
|
Identifying potential malicious attacks
: Identifying Potential Malicious Attacks
|
|
Find the prices that form an equilibrium
: Suppose two firms sell an homogeneous product; they compete in prices. Their respective marginal costs are MC1(q) = 10 and MC2(q) = 20. Find the prices that form an equilibrium (for simplicity and reality, assume that prices are quoted in units no sm..
|
|
Compete in prices in homogeneous good market
: Suppose three firms compete in prices in an homogeneous good market. Their costs are the same, mc = 10 (marginal cost). Find the equilibrium prices of this game. (Are there many equilibria? If so, notice what all of them have in common).
|
|
What is the firms cost function
: Gail works in a flower shop, where she produces 10 floral arrangements per hour. She is paid $10 per hour for the first eight hours she works and $15 an hour for each additional hour she works. What is the firm’s cost function? What are its AC, AVC, ..
|
|
Minimum acceptable price to the seller
: Jennifer buys a piece of costume jewelry for $33 for which she was willing to pay $42. The minimum acceptable price to the seller, Nathan, was $30. Jennifer experiences:
|