Reference no: EM131650511
Assignment
NB: - I do not want to get a copied paper. some has given me and it was retuned by my professor. No plagiarism. recent reference no more than three years. Bear in mind I do not want a copy paper and get another Zero. Someone has played on my grades and time I do not know what he benefited from putting me in water my grade.
Technical Project Paper: Information Systems Security
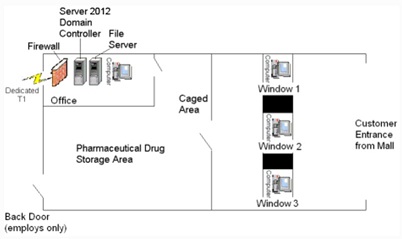
Suppose you are the IT professional in charge of security for a small pharmacy that has recently opened within a shopping mall. The daily operation of a pharmacy is a unique business that requires a combination of both physical and logical access controls geared towards protecting medication and funds located on the premises, as well as the personally identifiable information and protected health information of your customers that resides on your system. Your supervisor has tasked you with identifying inherent risks associated with your pharmacy and establishing strong physical and logical access control methods to mitigate the identified risks.
1) Firewall (1)
2) Windows 2012 Active Directory Domain Controllers (DC) (1)
3) File Server (1)
4) Desktop computers (4)
5) Dedicated T1 Connection (1)
Write an eight to ten page paper in which you:
1. Identify at least five potential physical threats that require attention.
2. Determine the impact of at least five potential logical threats that require attention.
3. Detail the security controls (i.e., administrative, preventative, detective, and corrective) that the pharmacy could implement in order to protect it from the five selected physical threats.
4. Explain in detail the security controls (i.e., administrative, preventative, detective, and corrective) that could be implemented to protect from the five selected logical threats.
5. For each of the five selected physical threats, choose a strategy for addressing the risk (i.e., risk mitigation, risk assignment, risk acceptance, or risk avoidance). Justify your chosen strategies.
6. For each of the five selected logical threats, choose a strategy for handling the risk (i.e., risk mitigation, risk assignment, risk acceptance, or risk avoidance). Justify your chosen strategies.
7. Use at least five quality resources in this assignment (no more than 2-3 years old) from material outside the textbook. Note: Wikipedia and similar Websites do not qualify as quality resources.
Your assignment must follow these formatting requirements:
• Be typed, double spaced, using Times New Roman font (size 12), with one-inch margins on all sides; citations and references must follow APA or school-specific format. Check with your professor for any additional instructions.
• Include a cover page containing the title of the assignment, the student's name, the professor's name, the course title, and the date. The cover page and the reference page are not included in the required assignment page length.