Reference no: EM131058052
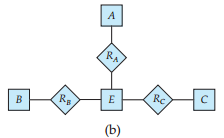
Consider the representation of a ternary relationship using binary relationships as described in Section 7.7.3 and illustrated in Figure 7.27b (attributes not shown).
a. Show a simple instance of E, A, B,C, RA, RB, and RC that cannot correspond to any instance of A, B,C, and R.
b. Modify the E-R diagram of Figure 7.27b to introduce constraints that will guarantee that any instance of E, A, B,C, RA, RB, and RC that satisfies the constraints will correspond to an instance of A, B,C, and R. c. Modify the translation above to handle total participation constraints on the ternary relationship.
d. The above representation requires that we create a primary-key attribute for E. Show how to treat E as a weak entity set so that a primary-key attribute is not required.
|
What makes it feel better or worse
: Create a picture log of your family or friends that have habitual holding patterns. Use 10 pictures that look like they're from 10 different people. From the pictures guess what area of the body is creating the holding pattern, pain or discomfort ..
|
|
Cost of borrowing in cash and cost of borrowing
: Calculate the difference between cost of borrowing in cash and cost of borrowing in gold (in dollar amount). Note in calculating the difference, deduct the cost of borrowing in gold from the cost of borrowing in cash. All rates are quoted in conti..
|
|
Foreign key constraints can only reference the primary key
: Explain how to enforce total participation constraints using complex check constraints or assertions (see Section 4.4.7). (Unfortunately, these features are not supported on any widely used database currently.)
|
|
Evaluation of asset composition useful for capital structure
: 1. Why is the evaluation of asset composition useful for capital structure analysis? 2. Is net income a reliable measure of cash available to meet fixed charges?
|
|
How to treat e as a weak entity set
: Modify the E-R diagram of Figure 7.27b to introduce constraints that will guarantee that any instance of E, A, B,C, RA, RB, and RC that satisfies the constraints will correspond to an instance of A, B,C, and R. c. Modify the translation above to h..
|
|
Need a final paper for finance
: Each student is required to conduct a detailed analysis of a company as part of a term paper. The analysis will look at issues like:Industry description; composition (domestic versus imports; large firms versus small firms); prospects.
|
|
Fantastic holding payout policy
: Write an essay about Fantastic Holding's Payout policy - outline, analyse and interpret the company's payout policy over the review period. How is this payout policy compared (a) to that of its major competitors, and/or (b) to that of the industry..
|
|
What are the benefits of globalization on folk cultures
: What are the consequences and benefits of globalization on folk/local cultures? Discuss points, use and bold at least three chapter terms, and give at least one example. 150-200 words.
|
|
The local tax assessor correctly value his house
: You have just been made a valuation analyst. Before you get training (what else is new!), your boss asks you to value a number of items: 1) a publicly-traded company; 2) a family business; 3) a shopping center; 4)
|