Reference no: EM133542804
Securing Networks
Question 1
Install and Configure Spam Assassin
This question is concerned with the installation, configuration, and testing of S- pam Assassin, which is an open source software package for filtering (removing, or flagging) SPAM (unwanted email).
The home page for Spamassassin and a useful collection of web pages providing information about Spa- massassin is available at SPAMASSASSIN. It is best to ignore any information which advises how to configure Spamassassin by means of the system known as cPanel because installation of that system is not required, or desirable, in this context.
Note: Spam Assassin is normally applied to all the incoming email at a server, but this exercise will not be conducted on an email server, but rather on a stan- dalone host. Spam Assassin can be installed in this situation, but it will be applied to an email provided as a file, by using the fi lter (a program which accepts in- put, from stdin, modifies i t, and prints the result to stdout) used by the Spam Assassin system, rather than using Spam Assassin for all the incoming email.
This question is divided into three sub questions:
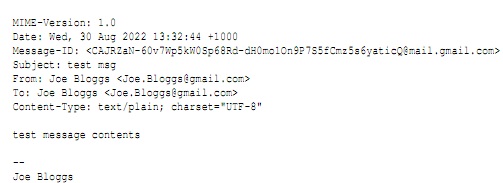
Figure 1: The full text of a simple email message
(a) Use apt (a command-line tool provided in debian Linux (like ubuntu) and its variants) or synaptic (a graphic tool provided in Debian Linux and its variants) to install Spamassassin on your VM.
(b) By adding a whitelisting rule for [email protected] and a blacklisting rule for [email protected], configure Spam Assassin to allow all e- mail from [email protected] and to block all email from [email protected].
(c) Test, by using the spamassassin filter (a command), that Spam Assassin is now reporting all emails from [email protected] as spam, and all email from [email protected] is reported as ham (not spam). Include in your assignment the results of these tests which show that Spam Assassin is working correctly.
To carry out the tests, you will need an email message from [email protected] and also one from [email protected]. It is not difficult to generate such an email (by sending yourself an email message and changing the email of the sender). In addition, a sample email address is shown in Figure1.
Question 2
This question continues from where Tutorial 8 finished. Starting with the net- work shown in Figure2which has a firewall prevents communication from the

Figure 2: A network with a firewall
Internet to all nodes in the domain except Node Web at ports 80 and 443..
Your tasks in this exercise are as follows:
(a) Add rules to the firewall which enable nodes at A and H to communicate with port 80 on nodes Y.
(b) Add rules to the firewall which enable nodes at A and H to communicate with port 80 on nodes Z.
(c) Add a new stream together with a test to show that traffic between nodes in the intranet (Domain) and the Internet except the traffic explicitly allowed in the preceding rules is blocked.
(d) Add a new steam and a test to show that traffic within the Intranet is allowed.
(e) Add a new stream and a test to show that traffic to or from any port other than 80 or 443 from node Web is blocked.