Reference no: EM13989911
Section 1 #1. Just as with graphs, it is possible to generate an infinite number of tests from a grammar. How and what makes this possible?
We know that code generators translate graphical source language into textual language that implies a natural approach in representing the generator with the help of graphs set. Testing all input models that triggers any possible application sequence is impossible because of the large amount of combinatorial possibilities. Just like graphs it is possible to generate infinite numbers of tests from grammar by triggering any possible application sequence for testing. Even though, it would be impractical because ofunnecessary and large number of combinatorial possibilities. However, it would be vital to include as many tests a possible to reveal any errors in the code.
Section 2 #1. Consider the stream BNF in Section 1 and the ground string \B 10 06.27.94."Give three valid and three invalid mutants of the string. Stream BNF from section 5.1.1: G 17 08.01.90
B 13 06.27.94
G 13 11.21.94
B 04 01.09.03
Section 2 #2. Provide reachability conditions, infection conditions, propagation conditions, and testcase values to kill mutants 2, 4, 5, and 6 in table 1.
|
Original Method
|
|
With Embedded Mutants
|
|
int Min (int A, int B)
|
|
int Min (int A, int B)
|
|
{
|
|
{
|
|
int minVal;
|
|
int minVal;
|
|
minVal = A;
|
|
minVal = A;
|
|
if (B < A)
|
Δ1
|
minVal = B;
|
|
{
|
|
if (B < A)
|
|
minVal = B;
|
Δ2
|
if (B > A)
|
|
}
|
Δ3
|
if (B < minVal)
|
|
return (minVal);
|
|
{
|
|
} // end Min
|
|
minVal = B;
|
|
|
Δ4
|
Bombo:
|
|
|
Δ5
|
minVal - A:
|
|
|
Δ6
|
minVal = failOnZero (B):
|
|
|
|
}
return (minVal);
|
|
|
|
1 // end Min
|
Table 1.
Section 2 #3. Answer questions (a) through (d) for the mutant in the two methods, findVal() andsum().
(a) If possible, find a test input that does not reach the mutant.
(b) If possible, find a test input that satisfies reachability but not infection for the mutant.
(c) If possible, find a test input that satisfies infection, but not propagation for the mutant.
(d) If possible, find a test input that strongly kills mutant m.
//Effects: If numbers null throw NullPointerException //Effects: If x null throw NullPointerException
// else return LAST occurrence of val in numbers[] // else return the sum of the values in x
// If val not in numbers[] return -1
1. public static intfindVal (int numbers[], intval) 1. public static int sum (int[] x)
2. { 2{
3. intfindVal = -1; 3. int s = 0;
4. 4. for (inti=0; i<x.length; i++) }
5. for (inti=0; i<numbers.length; i++) 5. {
5'.// for (inti=(0+1); i<numbers.length; i++) 6. s = s + x[i];
6. if (numbers [i] == val) 6'. // s = s - x[i]; //AOR
7. findVal = i; 7. }
8. return (findVal); 8. return s;
9. } 9. }
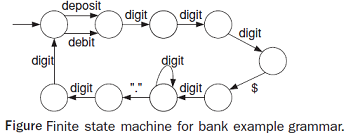
Section 3 #1 Generate tests to satisfy PDC for the bank example grammar.
bank ::= action*
action ::= dep | deb
dep ::= "deposit" account amount
deb ::= "debit" account amount
account ::= digit3
amount "$"digit + "."digit2
digit ::= "0" I "1" I "2" I "3" I "4" I "5" I "6" I "7" I "8" I "9"
Section 3 #2 Consider the following BNF with start symbol A:
A::= B"@"C"."B
B::= BL | L
C::= B | B"."B
L::= "a" | "b" | "c" | ... | "y" | "z" and the following six possible test cases:
t1 = [email protected]
t2 = [email protected]
t3 = mm@pp
t4 = [email protected]
t5 = bill
t6 = @x.y
For each of the six tests, (1) identify the test sequence as either \in" the BNF, and give a derivation, or (2) identify the test sequence as \out" of the BNF, and give a mutant derivation that results in that test. (Use only one mutation per test, and use it only one time per test).
Section 3 #3. Java provides a package, java.util.regex, to manipulate regular expressions. Write aregular expression for URLs and then evaluate a set of URLs against your regular expression.
This assignment involves programming, since input structure testing withoutautomation is pointless.
(a) Write (or find) a regular expression for a URL. Your regular expression does not need to be so general that it accounts for every possible URL, but give your best effort (for example "*" will not be considered a good effort). You are strongly encouraged to do some web surfing to find some candidate regular expressions.
One suggestion is to visit the Regular Expression Library.
(b) Collect a set of URLs from a small web site (such as a set of course web pages).
Your set needs to contain at least 20 (different) URLs. Use the java.util.regexpackage to validate each URL against your regular expression.
(c) Construct a valid URL that is not valid with respect to your regular expression (and show this with the appropriate java.util.regex call). If you have done an outstanding job in part 1, explain why your regular expression does not have any such URLs.