Reference no: EM131491662
ADVANCED E-SECURITY ASSIGNMENT
Please answer the following questions-
QUESTIONS-
1. This question is about the public key used in web site encryption. The key is called a "digital certificate". Web sites with encryption start with https not http.
a. Find a company that issues digital certificates.
One way is to go to your favorite encrypted web site, and click on the padlock symbol. This will tell you the name of the company that issued the digital certificate for the web site.
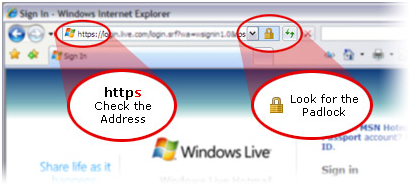
Alternatively, you could just pick a company from the list of recognized digital certificates for the Mozilla web browser.
Either way, find the name of a company that issues digital certificates for web sites.
b. Go to the web site of that company that issues digital certificates. Look up their contact details, and write down the company's street address and phone number.
c. Browse their web site, and find how much does it cost for a digital certificate for a year? (Use the cheapest choice, e.g., single-name certificate).
d. How does someone apply for a digital certificate from this company? Do they ask for a driver's licence? An incorporation certificate? Or do they only ask that you generate a CSR (certificate signing request), which a web server program can make using its domain name.
e. In your opinion, could a criminal obtain a digital certificate from this company? Why or why not?
2. A few short questions about computer security.
a. Anti-virus software is popular for Microsoft Windows. Find the typical detection rate for popular anti-virus software. Please give recent references for what you find (i.e., since 2017 began, or as new as possible)
b. Using the web, find out one recently severe DDoS attack. Who and how did they launch the attack? What damages?
c. How big is the biggest botnet currently in use? What country is it likely to have come from? Please give references for what you find.
Note that the BredoLab Botnet (also known as Oficla) used to run on about thirty million computers, but it was mostly dismantled back in 2010.
3. For identity theft events, see website privacyrights
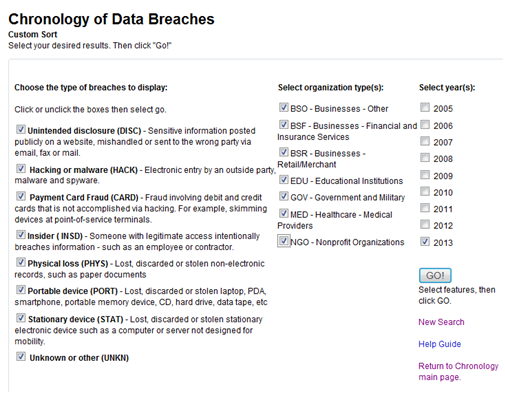
a. Limit the search to only 2017. What is the biggest (i.e., most identities stolen) identity theft incident that has happened so far in 2017? Briefly describe the date, the organization, how many people were affected, and what happened.
b. Tick all the boxes to search to all organization types, and limit the search to only the type "Hacking or malware (HACK)". What is the biggest (i.e., most identities stolen) identity theft incident that has happened so far in 2017?
If this turns out to be the same answer as for (a) above, then pick the second-biggest theft in the hacking category.
Briefly describe the date, the organization, how many people were affected, and what happened.
4. Some fun questions about criminal web sites.
a. Go look up a list of recently-registered domain names. Click on a recent day, to see all the web domain names that were registered on that day.
Using this or any similar web site, pick a recent day in 2017. What day did you check, and roughly how many domain names were registered? (Rounding is okay)
b. From those domains, randomly choose 5 domain names. Copy-and-paste the domain name into your web browser, to see if there is a web site there.
How many of those 5 domains have a web site already set up? How many of them go nowhere, or redirect to a domain registry?
c. Pick one recently registered domain. Use the whois search to look up the domain name.
What is the name of the contact person? It should be listed as "Registrant Name"? Is there a phone number, email address, or physical address? Write down as much information about?
d. Either run a traceroute program on your computer, or go to a web site with a traceroute interface (look for one on Google). A visual traceroute program is nice.
Using traceroute, can you find in which country (and, if you can figure it out, which city) is the web site physically hosted?
e. Does the web site itself have any contact details, like phone number or address? If so, find what city the phone number is in.
5. Cost-benefit analysis! Your company's web site is sometimes broken into by hackers, with the following estimates of probabilities and costs:
- Each day there is a 1% chance (once in a hundred days) that a script kiddie will merely deface the web site but cause no other damage, costing only $2,000 in lost sales.
- Each day there is a 0.25% chance (once in four hundred days) that an expert hacker will delete data and steal customers' credit card numbers, costing $800,000.
- Remember how hackers stole all the data from Ashley Madison and killed the company? We estimate that each day there is a 0.01% chance (once in ten thousand days) that an expert hacker will steal all the company's data and kill it, costing $5,000,000.
The big boss wants you to advise on which of these three solutions to buy:
I. We could do nothing and accept the problem.
II. A nice IBM firewall costs a huge $300,000 per year. It claims to prevent all script kiddie hackers and 97% of expert hackers.
III. A cheap Microsoft firewall costs only $50,000 per year. It claims to prevent 90% of script kiddie hackers and 50% of expert hackers.
The big boss wants you to advise which to choose. Feel free to use a spreadsheet or calculator or whatever you find the most convenient to answer these questions:
- Calculate the annualized loss expectancy (ALE) for the three kinds of hacker attacks. What is the total annual loss expectancy?
- For the three possible solutions, calculate the total annualized loss expectancy (ALE) if that solution was used?
- Calculate the cost-benefit of the three different solutions.
- If the boss asks, is there a large difference between the solutions (are two solutions about the same), or is there a clear winner?
- A magazine article claims that the IBM firewall doesn't stop 97% of expert hackers, it only stops 95% of expert hackers. Would this small difference cause you to change your advice?
- The Microsoft salesperson offers to reduce the price from $50,000 to only $30,000 per year. Would this change your advice?
6. The following table contains a set of packet filter firewall rules for an IP network ranging from 192.168.1.0 to 192.168.1.254. In this network,
- The router that connects to the outside world has two network connections, and the one on the internal side is 192.168.1.1
- The email server (Simple Mail Transfer Protocol = SMTP) is at 192.168.1.2
- The web server (Hyper Text Transfer Protocol = HTTP) is at 192.168.1.3
- Only computers on our local network should be able to contact the web proxy server, which is at 192.168.1.4 and listens on port 8080.
(a) Briefly explain the effect of each of the following rules. Remember that in this context, 192.168.1.0 = 192.168.1.* = any local address.
|
|
Source
Address
|
Source
Port
|
Destination Address
|
Destination
Port
|
Action
|
|
1
|
Any
|
Any
|
192.168.1.0
|
> 1023
|
Allow
|
|
2
|
192.168.1.1
|
Any
|
Any
|
Any
|
Deny
|
|
3
|
Any
|
Any
|
192.168.1.1
|
Any
|
Deny
|
|
4
|
192.168.1.0
|
Any
|
Any
|
Any
|
Allow
|
|
5
|
Any
|
Any
|
192.168.1.2
|
SMTP = 25
|
Allow
|
|
6
|
Any
|
Any
|
192.168.1.3
|
HTTP = 80
|
Allow
|
|
7
|
192.168.1.0
|
Any
|
192.168.1.4
|
HTTP_ALT = 8080
|
Allow
|
|
8
|
Any
|
Any
|
Any
|
Any
|
Deny
|
(b) Your web proxy server is at 192.168.1.4 and listens on port 8080. An outside computer at 123.18.243.3 attempts to open a connection from port 5150 to your web proxy server. Typical packets are below:
Will the outside computer be able to connect? Give details.
|
Packet
|
Direction
|
Source Address
|
Dest. Address
|
Protocol
|
Dest. Port
|
Action
|
|
1
|
In
|
123.18.243.3
|
192.168.1.4
|
TCP
|
8080
|
?
|
|
2
|
Out
|
192.168.1.4
|
123.18.243.3
|
TCP
|
5150
|
?
|
(c) To provide more protection, two new rules (labeled 0a and 0b) are added at the start, so the rules look like the table below. Will the outside computer at 123.18.243.3 be able to connect from client port 5050 to the web proxy server now? Why or why not?
|
|
Source
Address
|
Source
Port
|
Destination Address
|
Destination
Port
|
Action
|
|
0a
|
192.168.1.0
|
Any
|
192.168.1.4
|
HTTP_ALT = 8080
|
Allow
|
|
0b
|
Any
|
Any
|
192.168.1.4
|
Any
|
Deny
|
|
1
|
Any
|
Any
|
192.168.1.0
|
> 1023
|
Allow
|
|
2
|
192.168.1.1
|
Any
|
Any
|
Any
|
Deny
|
|
3
|
Any
|
Any
|
192.168.1.1
|
Any
|
Deny
|
|
4
|
192.168.1.0
|
Any
|
Any
|
Any
|
Allow
|
|
5
|
Any
|
Any
|
192.168.1.2
|
SMTP = 25
|
Allow
|
|
6
|
Any
|
Any
|
192.168.1.3
|
HTTP = 80
|
Allow
|
|
7
|
192.168.1.0
|
Any
|
192.168.1.4
|
HTTP_ALT = 8080
|
Allow
|
|
8
|
Any
|
Any
|
Any
|
Any
|
Deny
|
(d) The outside computer now sends packets from client port 25 to the web proxy server's port 8080. Will the outside computer be able to connect? Give details.
|
Packet
|
Direction
|
Source Address
|
Dest. Address
|
Protocol
|
Dest. Port
|
Action
|
|
1
|
In
|
123.18.243.3
|
192.168.1.4
|
TCP
|
8080
|
?
|
|
2
|
Out
|
192.168.1.4
|
123.18.243.3
|
TCP
|
25
|
?
|
(e) If we replaced rule 0a with rule 4, would that change anything? That is, will this set of rules work the same as the rules in part (d)?
|
|
Source
Address
|
Source
Port
|
Destination Address
|
Destination Port
|
Action
|
|
4
|
192.168.1.0
|
Any
|
Any
|
Any
|
Allow
|
|
0b
|
Any
|
Any
|
192.168.1.4
|
Any
|
Deny
|
|
1
|
Any
|
Any
|
192.168.1.0
|
> 1023
|
Allow
|
|
2
|
192.168.1.1
|
Any
|
Any
|
Any
|
Deny
|
|
3
|
Any
|
Any
|
192.168.1.1
|
Any
|
Deny
|
|
5
|
Any
|
Any
|
192.168.1.2
|
SMTP = 25
|
Allow
|
|
6
|
Any
|
Any
|
192.168.1.3
|
HTTP = 80
|
Allow
|
|
7
|
192.168.1.0
|
Any
|
192.168.1.4
|
HTTP_ALT = 8080
|
Allow
|
|
8
|
Any
|
Any
|
Any
|
Any
|
Deny
|