Reference no: EM13847300
Assignment 1:
1. The figure below shows a rooted tree,
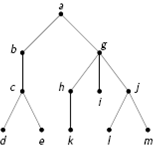
1.1. Find the height/level of the tree as shown above?
1.2 How many leaves does the tree have?
2. Mike sells on the average 15 newspapers per week (Monday - Friday). Find the probability that
2.1 In a given week he will sell all the newspapers
2.2 In a given day he will sell five newspapers.
3. Suppose that of 100 computers checked for viruses 30 where infected and 70 where not. If we select 10 computers at random what is the probability that at most 4 of them are infected?
Assignment 2:
1. You become a manager of Pick n Pay store and you are told that customers arrive at the store at an average of 30 per hour. What is the probability that you must wait at least 3 minutes for the first customer?
2. David bought a new phone. After the first 5 hours of use, the average remaining lifetime of the battery is 7 hours. Find the probability that the battery will last between 11 and 15 hours.
3. From the digraph below ,answer each of the following questions
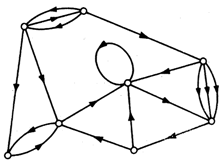
3.1 Label and find the number of edges, degrees and vertex in the above digraph.
3.2 Find the corresponding matrix of the digraph above.
3.3 Are there any sources or sinks, justify your answer?