Reference no: EM132636035
Question: Suppose that Bob sends N packets, each of length L bits, to Alice over two links (shown below). Suppose that the transmission rate of the first link (from Bob to the router) is mR bits/sec, where m ≥ 1, and the transmission rate of the second link (from the router to Alice) is R bits/sec.
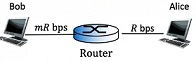
Suppose also that Bob transmits the N packets at intervals of a seconds, i.e., the duration between the transmission of the last bit of a packet by Bob and the transmission of the first bit of the next packet by Bob is a seconds. The router is a store-and-forward router. Considering a ≥L/R (1 - 1/m), find a formula, in terms of N, L, R, m and a, that characterizes the end-to-end delay of sending the N packets to Alice (i.e., the time needed for the last bit of the Nth packet to arrive at Alice since Bob starts transmitting the first bit of the first packet). Consider only the transmission delay that occurs in sending packets in your analysis. Show your work in detail.
Also, using your formula, find the end-to-end delay when N = 1000, L = 5000, R = 10,000,m = 2, and a = 0.25.