Reference no: EM131046279
The CRC algorithm as presented in this chapter requires lots of bit manipulations. It is, however, possible to do polynomial long division taking multiple bits at a time, via a table-driven method, that enables efficient software implementations of CRC. We outline the strategy here for long division 3 bits at a time (see Table 2.6); in practice we would divide 8 bits at a time, and the table would have 256 entries. Let the divisor polynomial C = C(x) be x3 + x2 +1, or 1101. To build the table for C, we take each 3-bit sequence, p, append three trailing 0s, and then find the quotient
q = p ?000÷C, ignoring the remainder. The third column is the product C × q, the first 3 bits of which should equal p.
(a) Verify, for p = 110, that the quotients p ?000 ÷ C and p ?111 ÷ C are the same; that is, it doesn't matter what the trailing bits are.
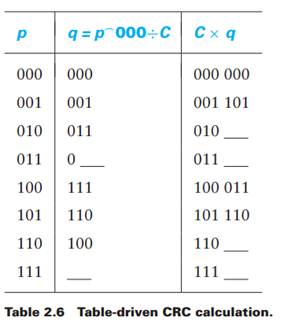
(b) Fill in the missing entries in the table.
(c) Use the table to divide 101 001 011 001 100 by C. Hint: The first 3 bits of the dividend are p = 101, so from the table the corresponding first 3 bits of the quotient are q = 110. Write the 110 above the second 3 bits of the dividend, and subtract C×q = 101 110, again from the table, from the first 6 bits of the dividend. Keep going in groups of 3 bits. There should be no remainder.
|
How dcf techniques are useful in overcoming financial risks
: Explain how DCF techniques are useful in overcoming financial risks at the time of taking investment decision, supporting your answer with an example - Compare between any two brands and their local demand in the market
|
|
Develop curiosity to generate significant and problematic
: Hopefully, this semester your accompanying research helped you to become more critical consumers of the material you read, and to develop the curiosity to generate significant and problematic questions.
|
|
An example of a byte/bit sequence that should never appear
: For each of the following framing protocols, give an example of a byte/bit sequence that should never appear in a transmission.
|
|
Identify most significant cybersecurity threats to a company
: For this assignment, imagine that you are a cybersecurity consultant hired to identify the most significant cybersecurity threats to a company.
|
|
Fill in the missing entries in the table
: Write the 110 above the second 3 bits of the dividend, and subtract C×q = 101 110, again from the table, from the first 6 bits of the dividend. Keep going in groups of 3 bits. There should be no remainder.
|
|
Identify the top hr risks that mark french need to manage
: Mark French has called his senior management team in early on a Monday morning about three weeks ago. He handed each of the managers a document titled, Future Directions. Identify the top five HR risks that Mark French and his team will need to man..
|
|
Designing a sliding window protocol for a 1-mbps
: Assuming that each frame carries 1 KB of data, what is the minimum number of bits you need for the sequence number in the following cases? Assume the speed of light is 3 × 108 m/s.
|
|
Create a informational report on dodge data services
: Create a 2-3 page professional-looking informational report (stapled; no report covers) on a topic that provides information to Dodge Data Services.
|
|
What is the minimum number of bits you need
: Assuming that each frame carries 1 KB of data, what is the minimum number of bits you need for the sequence number?
|