Reference no: EM131744145
Case Study Assignment
Read the case study titled "ING Life" found below.
Write a three to four page paper in which you:
1. Assess the probable difficulties and risks associated with using a public infrastructure such as the Internet as part of a business solution.
2. Analyze ING's solution for providing security to determine if the solution is adequate or inadequate. Provide a rationale for your answer.
3. Critique the extranet solution and recommend one change to the solution to provide better connectivity to brokers.
4. Use at least two quality resources in this assignment. Note: Wikipedia and similar Websites do not qualify as quality resources.
Your assignment must follow these formatting requirements:
• Be typed, double spaced, using Times New Roman font (size 12), with one-inch margins on all sides; references must follow APA or school-specific format.
The specific course learning outcomes associated with this assignment are:
• Compare and contrast among local area and wide area network technologies and architectures.
• Compare and contrast among data communication technologies that include transmission media, data link control protocols, and multiplexing.
• Use technology and information resources to research issues in communication networks.
• Write clearly and concisely about communication networks using proper writing mechanics and technical style conventions.
Case Study 3 ING Life
ING Life (formerly NN Financial) is a leading provider of life insurance products in Canada. The company is based in Ontario and operates out of three regional offices. Over 2000 brokerage partners market its products [BRUN99, IBM00]. In 1997 most of the brokers relied on fax, phone, and postal services to request policy information. Response times could sometimes be measured in hours. The company did have a 56-kbps frame relay wide area network, but that only connected the Ontario headquarters to 70 managing general agent offices (Figure III.1). The systems in Ontario converted the frame relay requests to SNA from TCP/IP and routed them to the corporate mainframe in Connecticut.
In December of 1997, ING decided it had to reduce response times to remain competitive and attract new brokers. The company wanted a cost-effective solution that could provide its brokers fast access to mainframe data and scale to accommodate new partners. ING investigated extending the existing frame relay network and estimated the cost at a prohibitive $3.3 million.
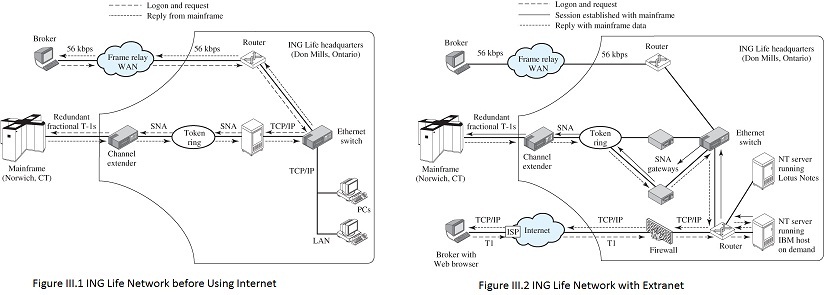
Figure III.1 ING Life Network before Using Internet and Figure III.2 ING Life Network with Extranet
Instead, the company decided to build an extranet and offer a Web-to-host service that would allow partners to access mainframe data directly via the Internet. ING estimated the annual cost of extranet services for 2000 brokers at $70,000. The annual cost of maintaining the existing WAN for 70 brokers was $750,000.
Besides reducing maintenance costs, the Web-to-host solution offered other benefits. The client software installed automatically as a browser applet, thereby reducing administrative costs. Also, using a browser as an interface meant that brokers were no longer tied to a specific workstation or PC.
The new solution would include two NT servers, a new SNA gateway (to translate between SNA and IP), and a Cisco Pix firewall connected to the Internet via a leased T-1 line (Figure III.2). The NT servers would run Lotus Notes, IBM Host on Demand (Web-to-host software), and Web server software. Because this service would send private data over the public Internet, security was a concern. The Pix firewall would prevent unauthorized access to the data. In addition, the Web-to-host software used an SSL (secure sockets layer) connection (described in Chapter 18). Before bringing the service on line, ING had security consultants probe the system for vulnerabilities.
By July of 1999, ING had 350 brokers connected to the extranet and plans to connect the remaining brokers by sometime in 2000. To use the new service, brokers connect to the Internet using dial-up and point their browser at the Web server. The Host on Demand client loads automatically as a browser applet. The applet provides TN3270 emulation services. After the applet has loaded, the broker can access the corporate mainframe as if he is using a directly connected TN3270 terminal. Response times for extranet requests are less than one minute.