Reference no: EM132371179 , Length: word count:1500
Overview of Internetworking Assignment - Network Requirement Analysis and Plan
Purpose of the This assignment is designed to assess students' knowledge and skills related to the assessment (with following learning outcomes:
- Analyse and report on the current and future state of the internetworking infrastructure and its applications.
- Implement a process to support the administration and management of internetworking.
Assignment Description -
Project Scope: A typical network layout diagram of a higher education Institute is given as under (for illustrative purposes only). The Institute has sections segregated as Melbourne and Sydney campuses connected through WAN. Within the campuses we have laboratories and other office workstations segregated into School of IT and School of Business. The Network requirements are given as under;
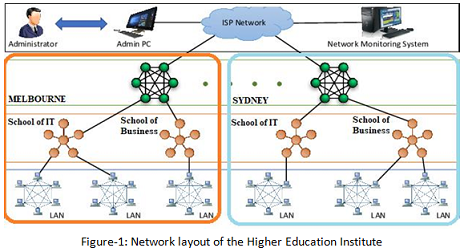
Network requirements -
1. Two campuses have separate local area networks. Staff users from two campuses should be capable of accessing other campuses.
2. There should be clear restriction of Lab (students) host not capable of pinging any office (staff) hosts.
3. Printing services should be available to all the schools users.
4. Wireless access is available to all the staff and student and guest as well on both campuses.
5. Internet should be provided to all the sections.
6. IP network design is required
7. Hardware requirements with costs specification.
8. Configuration details on the hardware (Routers, switches and workstations).
Assignment requirements: As a group you are required to design and simulate a network fulfilling the above mentioned requirement. The report should have a detailed explanation of the planning and designing of network. It is recommended that bullet points are included whenever necessary.
1. Project Scope
2. Project requirements
3. Network design - Consider the human factor design concepts
4. IP addressing in a tabular form (include justification whenever necessary)
5. Network topology diagram and simulation (CISCO Packet tracer is mandatory)
Switch configuration
Router configuration
Access point and server configuration guidelines
Security configuration
Student should show the demo of the network design in Week 11 lab. Work progress and consultation will be done during week 9 and 10. Demonstration marks will be awarded in regards to the stage of the completion of the design
The format of the demonstration will be
a) An individual demo,
b) At least 3 viva voce questions related to the design, and
c) Demo and viva voce duration 5 - 7 minutes (at max). The following is to be covered.
Demonstration of the network design simulation in CISCO Packet Tracer.
Note: As per the need, the lab tutor can allocate 15 minutes in Week 9 and Week 10 for work progression check and consultation.