Reference no: EM133144259
COIT20261 Network Routing and Switching - Central Queensland University
Objectives
This assessment lets you demonstrate your knowledge of routing concepts by completing several exercises. You will utilize material learned in the unit and may extend that learning through additional reading as required. The assignment is designed to help you to achieve the unit learning outcomes as listed in the unit profile.
Question 1 Routing Table construction
The network diagram below shows four routers named Toby, Joan, Mohan, and Boon. Assume that all the networks shown are aware of each other and have fully updated routing tables and router Boon was configured as default router. Construct the routing table for routers Boon and Toby. List masks in longest mask order, and in dotted-decimal format.
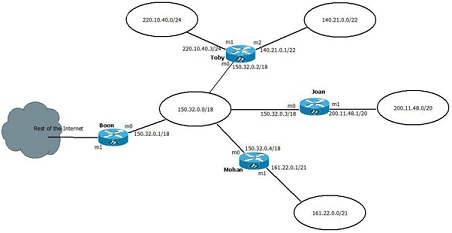
Fig. 1 Network Diagram
Question 2 - Forwarding process - classless addressing
First study and understand the forwarding process as explained in Forouzan Chapter 7. Answer the following two questions.
a) Refer to Figure 1 network diagram from Question 1. Assume that a packet arrives at router Boon with a destination address of 140.21.3.120. Show the router's forwarding process, that is, all the calculations it does to determine where to send the packet, the results at each step, and explain the router's decision at the end. Use a table to organize your data.
b) In the same diagram (Figure 1), assume that a packet arrives at router Joan with a destination address of 200.11.64.2. Show the router's forwarding process, that is, all the calculations it does to determine where to send the packet, the results at each step, and explain the routers decision at the end. Use a table to organize your data.
Question 3 - Distance Vector 3-step routing algorithm
In Week 8, the algorithm used to calculate shortest path using RIP is discussed, and the following diagram is used as an aid:
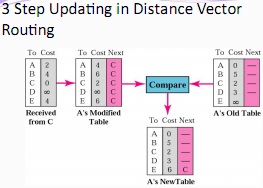
Working through this question will give you a feel for the logical processing by which Routers update each other by broadcasting a copy of their table to one another. You may find reviewing the materials for Week 8 helpful (especially the diagrams). You should draw the network diagram described by the tables below (use slide #12 & 13 in week 8 as a guide) and update the diagram as you go - this will help you answer the questions or verify your answers.
Shown below are the initial state routing tables for Routers A, B, C, D and E which all have the same destination networks listed, abbreviated to destinations A, B, C, D and E, with aggregated costs. For example, a cost of 6 equates to 6 hops. The solution table blanks are provided in the Answer Template. The initial state tables (five of them) are shown below:
The questions:
a) Router D receives an update from Router C. Process this update to show Router D's modified and final tables
b) Router A receives an update from Router B. Process this update to show Router A's modified and final tables.
c) Router E receives an update from Router A. Process this update to show Router E's modified table, and its final updated tables. Are the routes for E's final table now showing least possible cost i.e., the shortest paths? Discuss with reasons
d) Draw a diagram showing all routers and the known distances between them after the above three updates have been processed.
Question 4 Fragmentation
An IP datagram 5,140 bytes long with no options arrives at a router, which determines that the next destination is an Ethernet network through which the datagram must travel. Complete the following questions, showing your calculations and reasoning.
a) Assume that the router decides to fragment the packet into 4 fragments. Determine a correct size for each fragment and identify the starting byte and ending byte of each fragment.
b) Calculate the fragmentation offset for each fragment.
c) The total number of bytes from all 4 fragments leaving the router will be greater than the initial datagram size that arrived. Explain by how much, and the reason for this.
Attachment:- Routing and Switching.rar