Reference no: EM131428122
Question 1
(a)
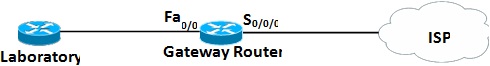
Figure Q1 (a)
i. Explain the difference between attaching a serial interface to a service provider in a production environment and attaching a serial interface to another Router in a laboratory environment.
ii. Choose an appropriate routing technique between the Internet Service Provider and the Gateway Router. Justify your selection.
(b)
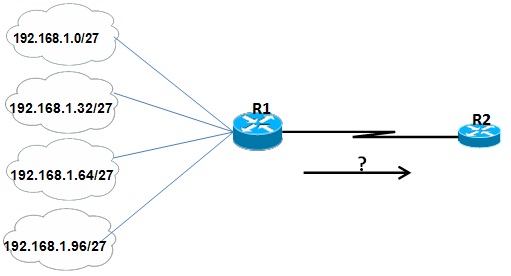
Figure Q1 (b)
i. Identify the type of route used between Routers R1 and R2 that facilitates Router R2 to reach the four networks shown in the Figure Q1 (b).
ii. Explain how you will configure the routing between Routers R1 and R2.
iii. Justify your selection by discussing its advantages.
(c) As a network administrator, explain in which situations you would choose to use the distance vector routing protocols and link-state routing protocols.
Question 2
(a)
Figure Q2 (a)
Analyze the routing table shown in the above Figure Q2 (a), and explain how the Router selects the path to the network 192.168.4.0.
(b) Provide FOUR (4) reasons routing loop occurrences and explain their respective implications on network operation.
(c) Routing Information Protocol (RIP) uses User Datagram Protocol (UDP) in the transport layer. UDP is considered as a connectionless and unreliable protocol. In this situation, how does RIP ensure the reliability and consistency of the routing updates between Routers.
Question 3
HQ# show ip route
<output omitted>
10.0.0.0/30 is subnetted, 1 subnets
C 10.10.10.252 is directly connected, Serial0/0/0
172.16.0.0/30 is subnetted, 1 subnets
C 172.16.100.0 is directly connected, Serial0/0/1
R 192.168.1.0/24 [120/1] via 10.10.10.254, 00:00:03, Serial0/0/0
R 192.168.2.0/24 [120/16] via 10.10.10.254, 00:00:03, Serial0/0/0
R 192.168.3.0/24 [120/1] via 10.10.10.254, 00:00:03, Serial0/0/0
R 192.168.7.0/24 [120/1] via 172.16.100.2, 00:00:04, Serial0/0/1
Figure Q3 (a)
Analyze the output shown in the above Figure Q3 (a).
i. Explain why the network 192.168.2.0/24 is not reachable from the HQ Router.
ii. Explain how HQ Router was informed by RIP that the 192.168.2.0/24 is not reachable.
(b)
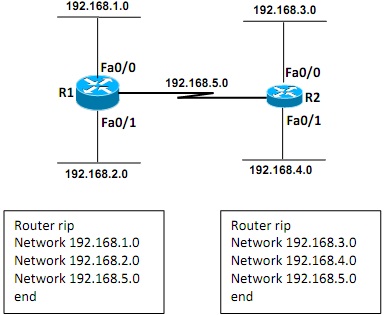
Figure Q3 (b)
Both Routers R1 and R2 are configured with RIP as shown in the above Figure Q3 (b).
i. Analyse three ways the unnecessary updates in RIP negatively impact upon the Local Area Network (LAN) environments.
ii. Modify the RIP configuration so RIP updates do not affect the LAN segments.
(c) With the aid of a block diagram, explain how a Router performs the route lookup process when it receives an IP packet and decides which route in the routing table is the best match.
Question 4
(a) Router# show ip eigrp topology
IP-EIGRP Topology Table for AS 1
Codes: P - Passive, A - Active, U - Update, Q - Query, R - Reply, r - Reply status
<output omitted>
P 10.10.12.0/24, 1 successors, FD is 5514496
via 172.16.1.38 (5514496/28160), Serial0/1/0 via 172.16.1.42 (7693056/6172416), Serial0/1/1
<output omitted>
P 10.10.14.128/25, 1 successors, FD is 6026496
via 172.16.1.38 (6026496/2172416), Serial0/1/0 via 172.16.1.42 (7181056/28160), Serial0/1/1
<output omitted>
Figure Q4 (a) Analyze the output shown in the above Figure Q4 (a).
i. Explain how the DUAL algorithm chooses the best path to the network 10.10.12.0/24 and 10.10.14.128/25.
ii. If the chosen path is suddenly down, explain what will happen.
(b) Even though Enhanced Distance Vector Routing Protocol (EIGRP) is classified as a Distance Vector Protocol, its architecture and operation are different from other Distance Vector Protocols as it has fast convergence. Explain why EIGRP is different from other Traditional Distance Vector Protocols apart from fast convergence.
(c) When analyzing your network traffic, you have found that only 50% of the bandwidth is available for data traffic in the 128 kbps serial connection between the HQ and Production yard. The network uses EIGRP as a protocol. The autonomous System number used is 5.
i. Explain how you will solve this problem and restrict the EIGRP to using less than 30% of the bandwidth.
ii. Provide the configuration for your proposed solution.
Question 5
(a) Your organization has decided to implement a link-state routing protocol and you are assigned to carry out this task. As a network administrator, explain briefly the requirements of routing devices that are important to configure the link state protocol.
(b)
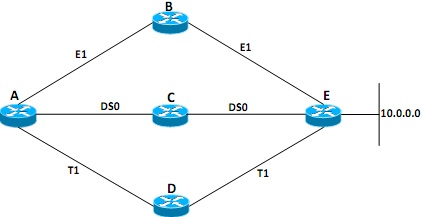
Figure Q5 (b)
Calculate the best path to the network 10.0.0.0 from the Router A using the Edsger Dijkstra's Shortest Path First (SPF) algorithm.
(c)
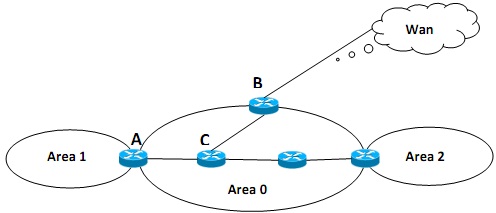
Figure Q5 (c)
Identify the type of Routers A, B and C and explain their roles.
(d)
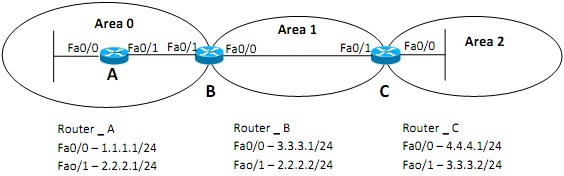
Figure Q4 (d)
When designing OSPF networks, all areas should be connected to the backbone area. However, due to topography constraints in Panda Corporation, it is not possible to connect the area-2 with the area-0. You are assigned to solve this problem.
i. Propose a solution to establish the connectivity for the area-2.
ii. With the aid of diagram, explain your proposed solution.
iii. Provide the configuration of your proposed solution.
Question 6
(a) Provide examples where you would recommend using the Border Gateway Protocol (BGP).
(b)
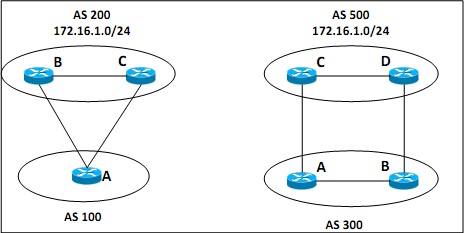
Figure Q6 (b)
Demonstrate how BGP path attributes can be used to set the preferred route as AC from AS100 to 200 and the preferred route as BD from AS 300 to AS 500.
(c) Addresses which are globally routable and reachable on the IPv6 Internet are known as global unicast addresses. With the aid of a diagram, explain the structure of a global unicast address for a typical site.