Reference no: EM132983812
Secure Programming
Task: Based on the coursework to date and your own research answer ten questions below. Question 11 is an optional bonus question. Each question is worth 10 marks, but questions are not of equal difficulty. Some questions seek demonstration of tests on Webgoat. Other questions require examples of code and these should be sourced and referenced from on-line tutorials. Answers should be at least 300 words (excluding references). Include references where appropriate. References should be in the Harvard style. Marks will be awarded for analysis of the problem or issue, correctness of information provided and evidence of independent research.
Note: The questions are "open-ended" and I encourage you to explore the issues covered in each question. It is not enough just to provide a description, I am looking for evidence of critical thinking: analysis of issues, examples of your investigations, etc.
Question 1
In your role as a Security Consultant at InterCorp, your manager has asked you to brief the application development group on implementing Microsoft's Security Development Lifecycle. What are some of the benefits of undertaking such a program? How will it impact their existing Software development methodologies? Explain how you can draw the application development group's attention into the skill of threat modelling.
Question 2
As part of a secure code review of an ASP.Net web application you have discovered the following code for the login page:
var username = Request.Form["username"]; var password = Request.Form["password"];
var sqlString = "SELECT * FROM Users WHERE username ='" + username + "' AND password = HASHBYTES('SHA2_512', '" + password + "'+ salt)" ;
var connString = WebConfigurationManager.ConnectionStrings
["NorthwindConnectionString"].ConnectionString;
using (var conn = new SqlConnection(connString)) {
var command = new SqlCommand(sqlString, conn);
var dataReader = command.ExecuteReader(CommandBehavior.SingleResult);
if (dataReader.HasRows){
loggedIn = true;
}
dataReader.Close();
}
Identify the vulnerability and remediate the code using appropriate countermeasures. Document your findings and the remediation implemented.
Question 3
OWASP is an organisation that is focused on improving the security of software. In particular, they have concentrated on "Injection flaws". Explain what an Injection flaw is. Based on Webgoat, how would you test for an Injection flaw? Work through your test and include appropriate screen shots.
Question 4
In your role as an analyst for TMP Co you have been asked to review the following authentication routine for a customer's python web application. The application is expected to handle large numbers of users at peak times. Identify any issues with the code and evaluate potential fixes and the trade-offs they may require. Justify your choice of a fix and then document the code showing where and how to implement the fix.
import hashlib
def authenticate_user(username, password): #retrieve user details from database user = usermodel.details(username) password_hash = user.password
if hashlib.md5(password) == password_hash: return 'True'
else:
return 'False'
Question 5
In your role as a Security Consultant at InterCorp, your manager has asked you to brief the application development group on implementing Microsoft's Security Development Lifecycle. What are some of the benefits of undertaking such a program? How will it impact their existing Software development methodologies? Explain how you can draw the application development group's attention into the skill of threat modelling.
Question 6
During an application pen-test you noticed that the application is providing a large amount of information back to the user under error conditions. Explain the security issues this may present. Describe and analyse the correct methodology for handling errors, and recording diagnostic information. What else might this information be useful for?
Question 7
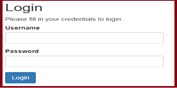
When logging on to your account on a company's website you see the following message:
What may this be indicative of? Explain why this is not valid and describe a more robust approach.
N.B. There may be multiple causes for this; credit will be awarded for identifying at least 2 issues.
Question 8
You have been asked by your manager to investigate the advantages and disadvantages of encryption using GPU chips. As part of your investigation highlight recent advances in encryption acceleration using NVIDIA's CUDA technology. What API's are available and what are their advantages and limitations? Highlight security issues. Your investigation must be supported by references and ideally some coding examples (e.g., from on-line tutorials).
Question 9
You have decided to discuss a possible security flaw in your organisation's new software which will soon be released to production. You decide to talk at next team meeting and ask the team to make sure users cannot enter HTML code as input into the application. You need to cover the following points: What is this type of security flaw? How would you mitigate it? Prepare an example using the MS Threat Analysis tool and give an example of a use case. Since you will be addressing a development team, some example mitigation code examples (from on-line tutorials) would be desirable.
Question 10
In Threat Analysis, what is a "trust boundary"? Your goal is to improve security by fortifying the trust boundaries of your organisation's web site. What recommendation would you make to your manager? Include explanations of advantages and issues. Illustrate your recommendation using MS Threat Analysis tool.
Question 11
Your manager has instructed you to write a review for the development team on using MS Attack Surface Analyser. You must define what makes up the attack surface of an application. Your explanation should be supported by examples, references to tutorials and for completeness, screenshots of your use of the attack surface software.
Attachment:- Secure Programming Assignment.rar