Reference no: EM131739725
Part-1
Given the following design for a money transfer protocol which utilizes public key cryptography to assure confidentiality and authenticity of the transmission.
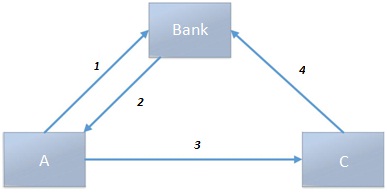
Issuing a Check:
1. Payee (A) will contact the bank requesting the issuance of $ amount check made payable to (B).
2. Bank responds by sending the payee a check receipt CR, where:
CR = RSA( PuA , check )
check = RSA( PuC , token )
token = AES128( KeyBank , amount )
3. Payee (A) receives the check receipt from the bank, extract the check from it and pass it to the receiver (C).
4. The receiver extracts the token from the check and pass it to the bank encrypted with its own private key to collect the money.
From C to Bank: RSA( PrC , token )
Given the following information about A, C, and the Bank:Given the following information about A, C, and the Bank:
For A:
Key length: 1024
Public Exponent: 65537 Public modulus [n]:
B5112FD2E82FB505D8C641DFC7087EBEC3971492CE3B5581BFE239AB192B190B443188BA995FB8BE231021A99E B1679EFE6257BC0DAF95552F92D87BB0E0D6BEB79601DFC74020E915A615FF5C5C7662C3ED5E76266EC4A0A030 92CE3B558B3905FD0A6468120091257EF75B0BBFAC5BDBF56FD4496133F640C7078982372117
Public exponent [e]: 010001 Private exponent [d]:
241C2F5B726EC13D4F440AB324306F867FDF4B7D13A005A780AB0F312E2DC82AD508C3E9E2D892316930B865E9
7E1BDA3B854555FDACBCAD667574B3064D70C5F611E7C6AF45BE29BADA7E5F5494DD8DD79C2BFCCFC1F898E20 BCA8F4BE7AB4142A1499E2DB21FE29E9AD29A6CFACED52BFE1DC94CD52EF76F6ACB1BF167DB81
For C:
Key length: 1024
Public Exponent: 65537 Public modulus [n]:
AB39243C0238D017C8179590824AAB0CA69E9815DF41C34E229AAB7C1F285999122CFBA56D67BA707207480696 928B5719296293123F39BE10EDE7CAB748EE52A088BD094773B313B50A17F088CBBBA70B0537761D12E2EE2D80
54B4974C955C9BF2AACD0DAA1081165E6BE52552E2CABFD6A5232A591369CCF812466C01596B
Public exponent [e]: 010001 Private exponent [d]:
45778870E441E2835385E6035C29291E97D70E43097227E7E278380CC2A35F3E903639DE92F59B999559C8EA0B5 AE7376E18F14A5403DCCC7517E08BC932C8A58961376EB1A4ED80EBA15B3877E0BCE1BA0BEDC6FA06C04C6D5E8 75B30898EC045678168EB06BB3344FEAE2F904761B37D3631DA864FA3AC35B25C539E245CA1
For the Bank:
AES128 Key: 670DBA40AB1F3752EF0DC1D0F8FB4958
a. Calculate the messages sent in steps 1 to 4 if A is sending $ amount equals to your NYIT ID to C.
b. Explain two different vulnerabilities and attack scenarios that are applicable to the above design.
c. Propose an enhancement to the above design to make it more secure.