Reference no: EM132206012 , Length: word count:1800
Assessment - Evaluation of Botnet Attacks and its Mitigation Methods
Purpose of the assessment (with ULO Mapping)
The purpose of the assignment is to analyse the botnet attacks in cybersecurity; evaluate available defensive resolutions, and recommend a security solution. Students will be able to complete the following ULOs:
a. Analyse cyber security threats and attacks
b. Implement and evaluate security testing tools in a realistic computing environment
Assignment 1: Evaluation of Botnet Attacks and its Mitigation Methods
Assignment Description
Internet of Things (IoT), equipped with massively interconnected Cyber-Physical Devices (CPDs) is opening a new era of ubiquitous computing and smart communications. The IoT is expected to create many new business opportunities in smart home care, industry automation, and critical infrastructure protection.
To enable the prevalent IoT services, many of the small computing devices, which were considered unworthy and unintelligent, have been reformatted and given the cyber-communication capacity. This has enabled many smart applications, but on the other hand, it has created serious security problems as these devices are not properly configured for security. These CPDs are inherently lack the computing resources (CPU processing or computer memory); therefore, they are open to many serious attacks including hijacking attacks which will dupe them to be part of BOTNET attacks.
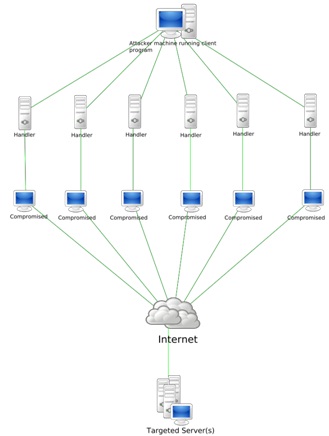
Figure 1: Example of Botnet Attack
The BOTNET attack is a serious problem in Cyber Security. In this report, you are to investigate:
1. The Botnet attack modules/structures
2. Botnet attack types and their implications to the victim services
3. Evaluation of protective technologies
4. Recommendation of protective resolution
5. Conclusion and remarks on future works.
Your group report should include the following sections and subsections:
1. Introduction to botnet attack and a simple case example addressing the significance of this report.
2. The Botnet attack modules/structures
a. Modules
i. The attacker or master
ii. Handler
iii. Agents
iv. Victims
b. Botnet attack life cycle
i. Initial infection
ii. Secondary infection
iii. Connection or rally
iv. Malicious activities
v. Maintenance and upgrading
3. Botnet attack types and their implications to the victim services
a. Select at least three examples from the list1.
b. Evaluate their attack implication to the potential victim services
4. Recommendation of your choice of the mitigation solution
5. Conclusion and remarks on future works