Reference no: EM131954498
Assignment
Question 1
The AIDA project (Affective, Intelligent Driving Agent), is an intelligent navigation system that aims to bring an innovative driving experience. Instead of focusing specially on determining routes to a specified waypoint, our system utilizes analysis of driver behavior in order to identify the set of goals the driver would like to achieve (Where he wants to go? would he like to visit some special place?).
Also, AIDA involves an understanding of the city beyond what can be seen through the windshield, incorporating information such as business and shopping districts, tourist and residential areas, as well as real-time event information and environmental conditions. Functionalities that gather information about driver preferences additionally help AIDA to behave more intelligently.
One mandatory task for AIDA is to predict the destination of the driver as well as the most likely route that he/she will follow. This will in turn allow for useful reactions from AIDA such as proposing route alternatives when something unexpected happens in the predicted route, or providing the right information at the right time (e.g. a fuel warning before passing by a gas station) or even helping save energy.
Answer these questions
1. Define PEAS
2. Propose appropriate agent type
3. Suggest the environment type for the above agent.
• Partially or Fully Observable
• Single agent or multi agent
• Deterministic or stochastic
• Episodic or sequential
• Static or dynamic
• Discrete or continuous
Question 2
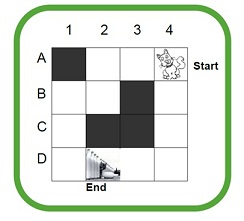
Consider the following problem. Give a formulation for this problem where cat want to reach to the place where other cats have bottles of milk. Draw the searching tree and solve using any applicable searching strategy. The squares colored as grey cannot be used.